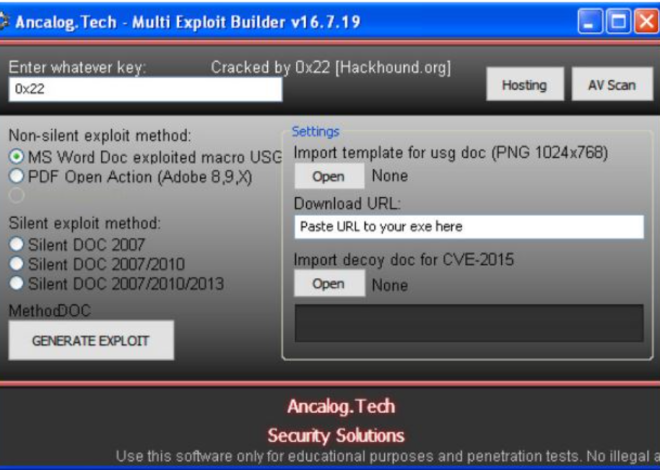
BEST CRACKING PACK 2025
In 2025, comprehensive cracking toolkits have become a pervasive threat in the cybercriminal ecosystem, enabling attackers to automate credential theft, system breaches, and data exfiltration at scale. Best cracking pack 2025 all-in-one packages bundle multiple exploitation tools into a single interface, lowering the technical barrier for would-be attackers while increasing the efficiency of experienced hackers. […]
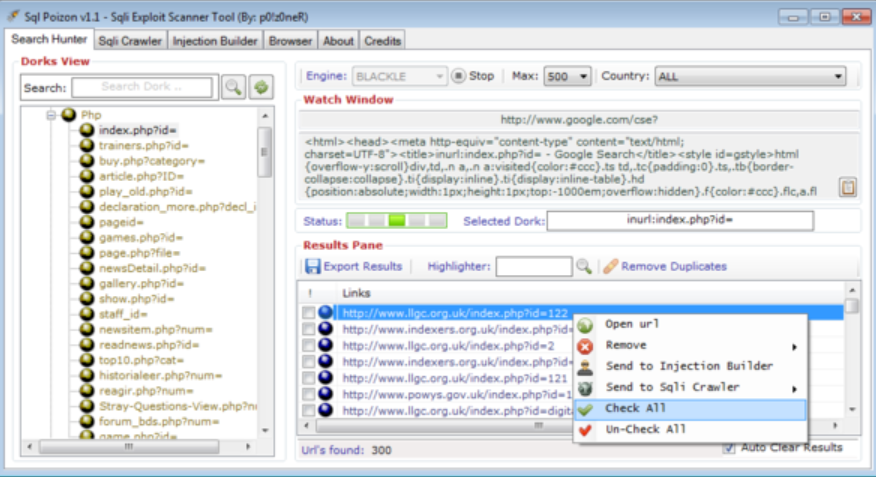
AURA AIO CHECKER 30 Modules 2025
In 2025, modular credential-checking platforms have emerged as one of the most dangerous tools in a cybercriminal’s arsenal, enabling large-scale account takeover attacks with frightening efficiency. AURA AIO CHECKER 30 Modules all-in-one (AIO) systems combine dozens of specialized validation modules into a single interface, allowing attackers to test stolen credentials across financial institutions, social media […]
NinjaTok tiktok Bot 2024
In recent years, tools like NinjaTok TikTok Bot 2024 have become a growing threat in the cybersecurity landscape. These automated bots are designed to manipulate social media platforms by generating fake engagement, spreading malware, or conducting large-scale spam campaigns. Attackers use them to artificially inflate follower counts, like/dislike ratios, and comment sections, often for financial […]
Alfey Mail Access Checker
In 2024, email access validation tools have become a critical component of cybercriminal operations, enabling attackers to efficiently identify and exploit compromised email accounts. Alfey Mail Access Checker 2024 specialized tools automate the process of testing stolen credentials against major email providers, helping attackers filter out non-working logins before launching targeted campaigns. By verifying active […]
njRAT v0.7d Edition by Hidden Person
The cyber threat landscape continues to evolve with increasingly sophisticated remote access tools, among which njRAT v0.7d Edition has emerged as a particularly dangerous variant of a well-known remote administration tool. This enhanced version demonstrates how cybercriminals are refining existing malware with new capabilities to bypass modern security measures. njRAT v0.7d Edition by Hidden Person […]
Teardroid v4
In the evolving landscape of cyber threats, remote access trojans (RATs) continue to be a persistent tool for attackers, allowing unauthorized control over compromised systems. Among these, Teardroid v4 has emerged as a notable Android-based malware, frequently employed in targeted attacks to steal sensitive data, monitor user activity, and deliver additional payloads. Its modular design and […]
Lost Door Aws 9.2
In the evolving landscape of cloud-based cyberattacks, sophisticated tools targeting AWS (Amazon Web Services) environments have become increasingly prevalent. Lost Door Aws 9.2 specialized utilities enable threat actors to exploit misconfigured cloud resources, escalate privileges, and establish persistent access to critical infrastructure. As organizations continue migrating operations to the cloud, attackers have adapted by developing […]
Subbus RAT 2025 Cracked
The cybersecurity landscape faces an escalating threat from next-generation remote access Trojans, with Subbus RAT 2025 emerging as a particularly sophisticated example of modern malware evolution. This advanced threat demonstrates how cybercriminals are leveraging cutting-edge techniques to create more resilient and feature-rich attack tools. SUBBUS RAT has been observed in high-profile attacks against financial institutions […]
PENTAGON RAT 2024
The “PENTAGON RAT 2024” is a highly advanced remote access trojan (RAT) that poses a major threat in modern cyberattacks. Unlike traditional malware, it not only evades detection but also maintains persistent access to compromised systems. Security experts have linked it to espionage, data theft, and credential harvesting. Itsmodular architecture allows attackers to deploy additional malicious payloads. As a result, it has become a versatile tool for both cybercriminals and state-sponsored […]
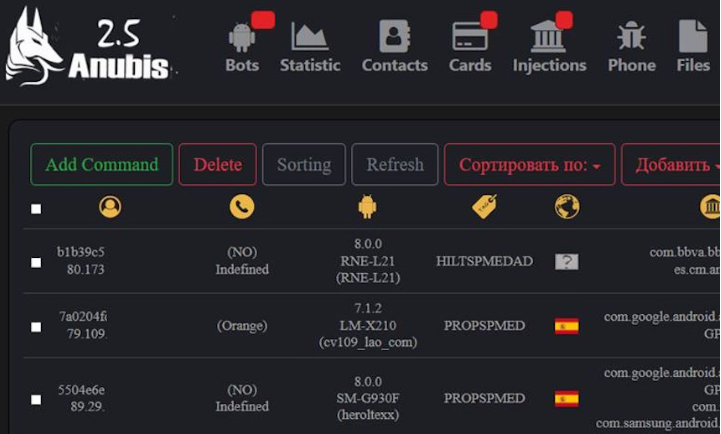
ANUBIS 7.0 ANDROID BOTNET (Panel + Builder+ Tutorial)
The rise of mobile-focused malware has introduced dangerous new threats to personal and enterprise security, with advanced botnet frameworks posing one of the most severe risks. Modern Android botnet kits now offer sophisticated infection vectors, evasion techniques, and monetization capabilities that rival traditional Windows malware. ANUBIS 7.0 ANDROID BOTNET toolkits typically include builder applications, command-and-control […]