Fullwidth Featured
GhostDZ RAT v1.1D
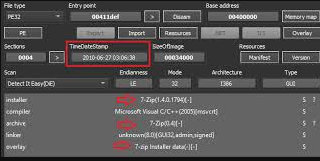
The GhostDZ RAT v1.1D has emerged as a significant threat in modern cyberattacks, particularly due to its stealthy infiltration capabilities and persistence mechanisms. Often deployed in targeted attacks, this malware enables threat actors to gain long-term access to compromised systems, exfiltrate sensitive data, and execute malicious commands remotely. Its ability to evade detection while maintaining […]
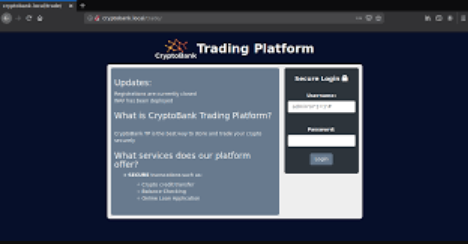
CryptoBanker v0.17a Cracked
The rise of cryptocurrency has given birth to a new generation of financial malware, with CryptoBanker emerging as one of the most sophisticated threats targeting digital asset holders. This advanced malware exemplifies how cybercriminals are adapting traditional banking trojan techniques to exploit cryptocurrency transactions, creating specialized tools for financial theft in the blockchain era. Operating as […]
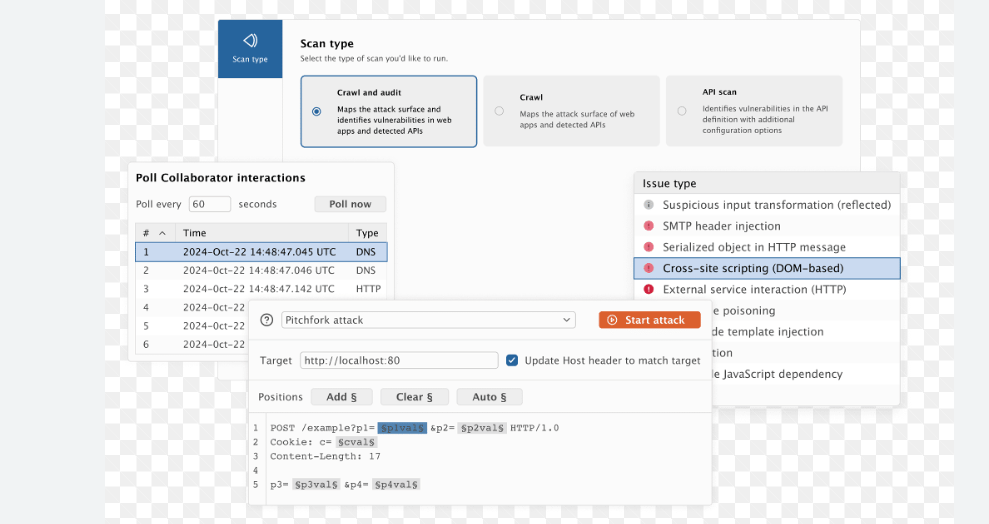
Burp Suite Professional 2021.9 Build 10295
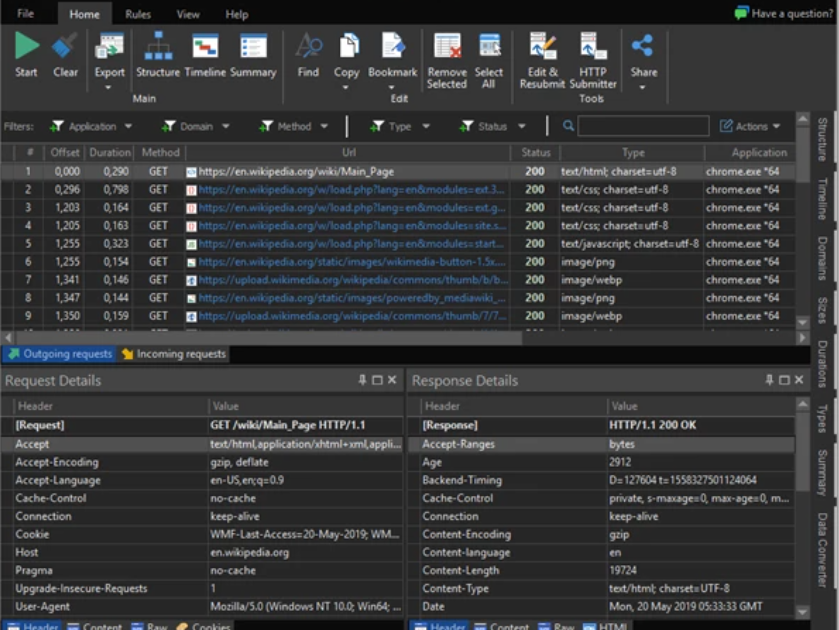
In modern cybersecurity, penetration testing and vulnerability assessment tools play a critical role in both offensive and defensive operations. One such tool, Burp Suite Professional 2021.9 Build 10295, has become a staple for security professionals and malicious actors alike due to its powerful capabilities in web application testing. While ethical hackers use it to identify […]
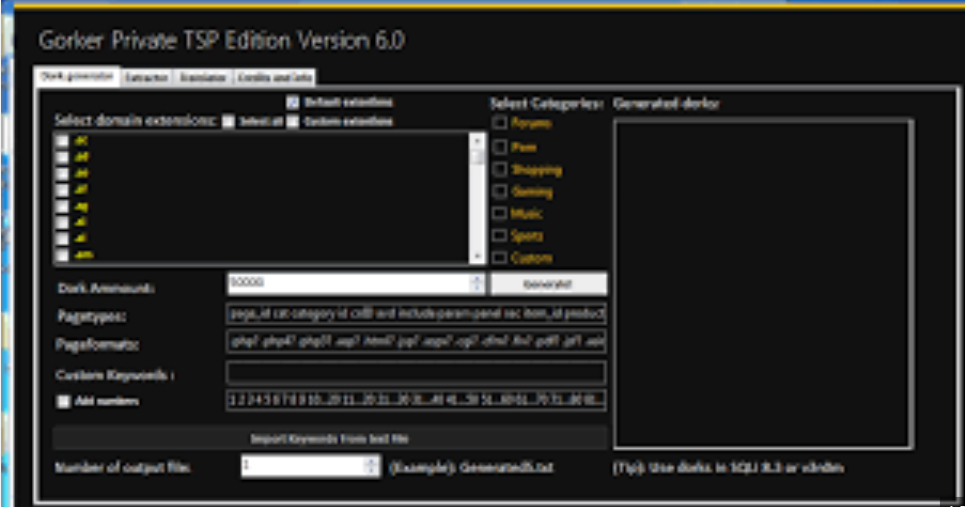
Gorker Private TSP Edition 6.0
In the evolving landscape of cyber threats, specific tools have gained notoriety for their role in facilitating sophisticated attacks. One such tool, often referred to in cybersecurity circles, is a remote access trojan (RAT) that enables attackers to gain persistent control over compromised systems. Its modular design and stealth capabilities make it a favoured choice […]
Hidemyass Checker 2025
Cybercriminals continue to evolve their tactics to maintain anonymity and bypass security measures, with proxy-checking tools becoming an essential component of modern attack infrastructure. These specialized utilities allow threat actors to verify and manage large networks of proxy servers, ensuring their malicious activities remain untraceable. The 2025 generation of these tools demonstrates alarming sophistication, incorporating […]
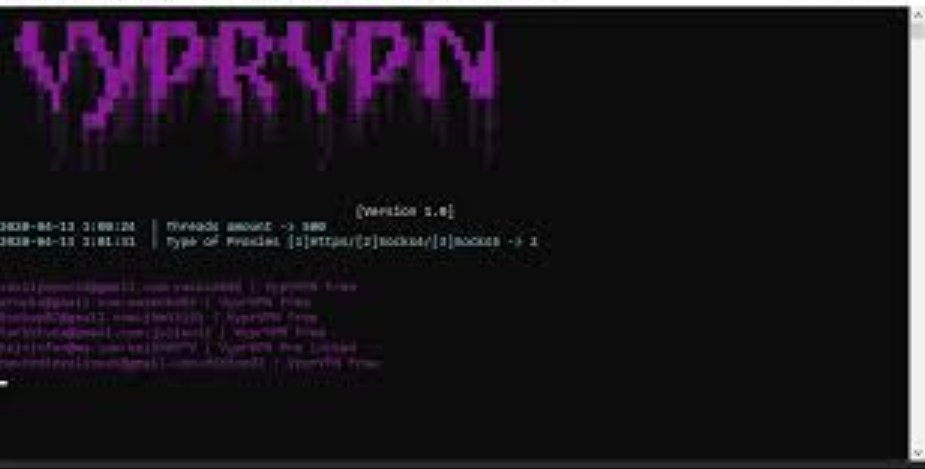
VyprVPN Checker 2025
In the evolving landscape of cybersecurity, tools designed to test network vulnerabilities play a crucial role, both for defenders and attackers. Among these tools, VyprVPN Checker 2025 has gained attention for its dual-use potential. While they can help legitimate users verify their anonymity and connection security. Malicious actors have repurposed them to identify and exploit […]
Woxy 3.0+166 Config updated 2023
The cybersecurity landscape in 2023 has seen a surge in sophisticated attack tools that leverage legitimate software infrastructures for malicious purposes. Among these, advanced proxy-based utilities have emerged as particularly dangerous enablers of cybercrime, allowing attackers to mask their activities behind layers of seemingly legitimate traffic. Woxy 3.0+166 Config updated tools have become essential components […]
HULK DDOS 2024
Distributed Denial-of-Service (DDoS) attacks remain a persistent threat in cybersecurity, and tools like HULK DDoS 2024 have emerged as potent weapons for disrupting online services. Unlike traditional DDoS methods, modern iterations employ advanced evasion techniques and increased scalability, making them more challenging to mitigate. These attacks overwhelm target servers with massive volumes of malicious traffic, often […]
BLAZING DORK V1.5 CRACKED
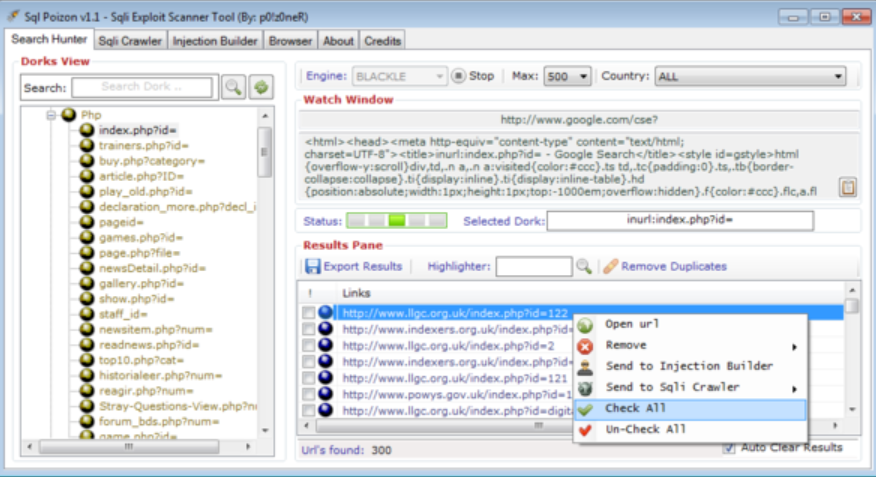
In recent years, cybercriminals have increasingly relied on sophisticated tools to carry out attacks, with one notable example being a modified version of a well-known penetration testing framework. This BLAZING DORK V1.5, often distributed illicitly, has been repurposed for malicious activities, including unauthorized network intrusions, data exfiltration, and the deployment of ransomware. Its widespread abuse […]
Chase Bank bruter 2025
Financial institutions remain prime targets for cybercriminals, and in 2025, automated brute-force tools have become increasingly sophisticated in breaching online banking systems. These tools are designed to exploit weak authentication mechanisms, enabling attackers to gain unauthorized access to accounts, steal sensitive financial data, and initiate fraudulent transactions. Unlike broad phishing campaigns, these tools execute targeted, […]