Android Tester v6.4.6
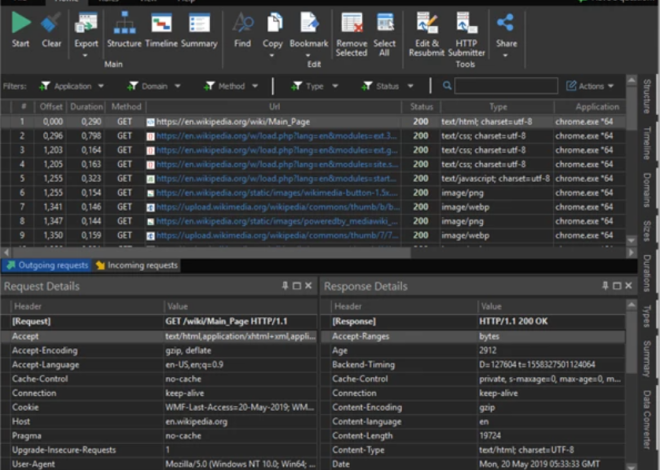
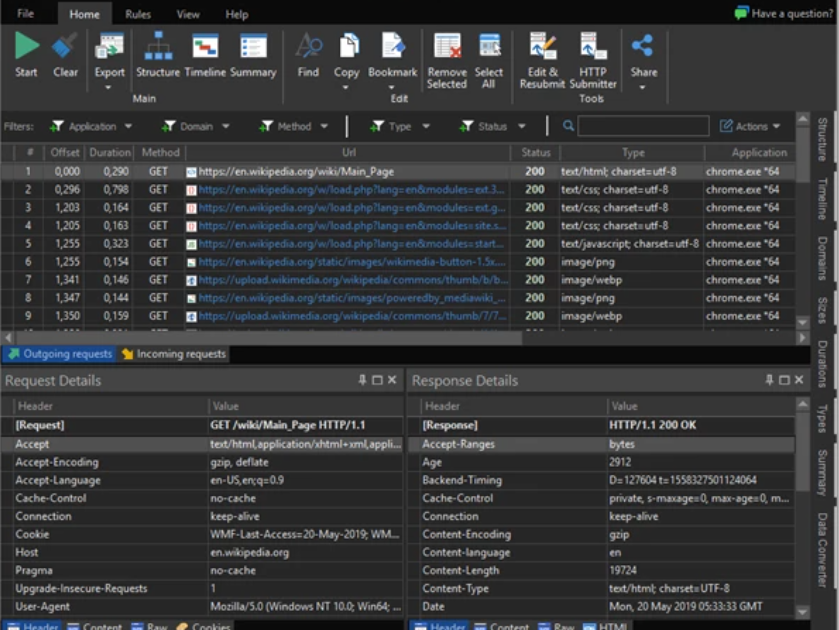
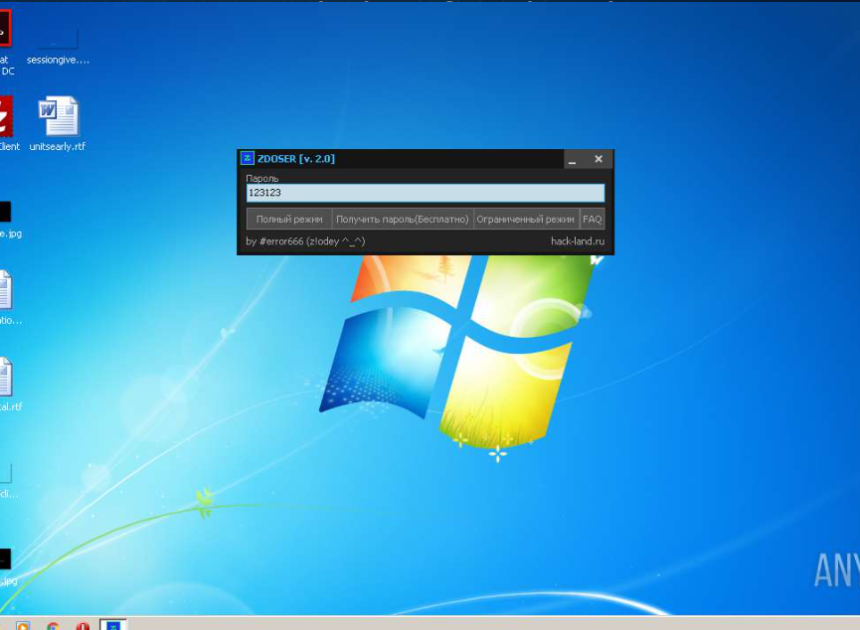
In the expanding world of mobile malware, a particularly dangerous application has emerged as a significant threat to Android users. This Android Tester v6.4.6, often distributed under the guise of legitimate testing tools, has become a favored weapon for cybercriminals targeting mobile devices. Its sophisticated capabilities allow attackers to gain complete control over infected devices, […]
HawkScan v1.9.6 Cracked
In the evolving landscape of cyber threats, tools designed for network reconnaissance and vulnerability assessment are frequently repurposed by malicious actors to facilitate attacks. One such tool, like HawkScan v1.9.6, often distributed in cracked versions, enables attackers to bypass security measures and identify weaknesses in target systems. While legitimate security professionals use similar software for […]
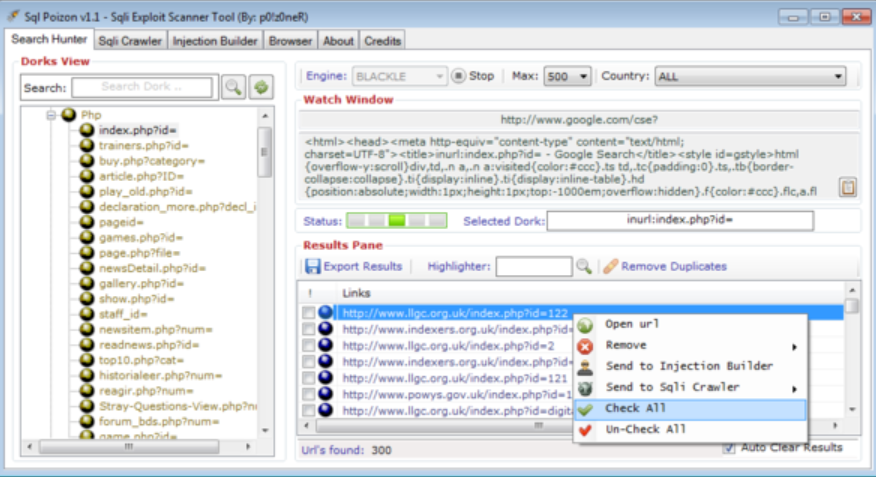
Dork Searcher V3 By CRYP70
Cyberattacks continue to evolve, leveraging increasingly sophisticated tools. Among these, Dork Searcher V3 By CRYP70 plays a critical role in identifying and exploiting vulnerabilities. This type of tool streamlines the process of gathering sensitive information from exposed systems, enabling attackers to deploy follow-up exploits efficiently. As a result, it has become a significant enabler of modern […]
Shell FINDER V-7
Firstly, the Shell FINDER V-7 has emerged as a significant tool in modern cyberattacks, frequently leveraged by threat actors to identify and exploit vulnerabilities in target systems. Not only does it automate reconnaissance and payload delivery, but it also proves particularly dangerous in the hands of malicious actors due to its efficiency. Recently, campaigns utilizing this software have conducted targeted […]
ANZ.COM Bank Brute 2025
In the evolving landscape of financial cybercrime, specialized brute-force tools targeting online banking platforms have emerged as a significant threat to financial institutions and their customers. These sophisticated attack tools are designed to bypass security measures and gain unauthorized access to online banking accounts, enabling cybercriminals to conduct fraudulent transactions, steal sensitive financial data, and […]
Coinbase Checker and Bruter 2025
As cryptocurrency adoption grows, so do the tools designed to exploit weaknesses in digital asset platforms. Among these, automated credential-testing tools have become a significant threat in 2025, enabling attackers to breach accounts at scale. Coinbase Checker and Bruter tools are frequently used in credential stuffing and brute-force attacks, targeting exchanges, wallets, and financial services. […]
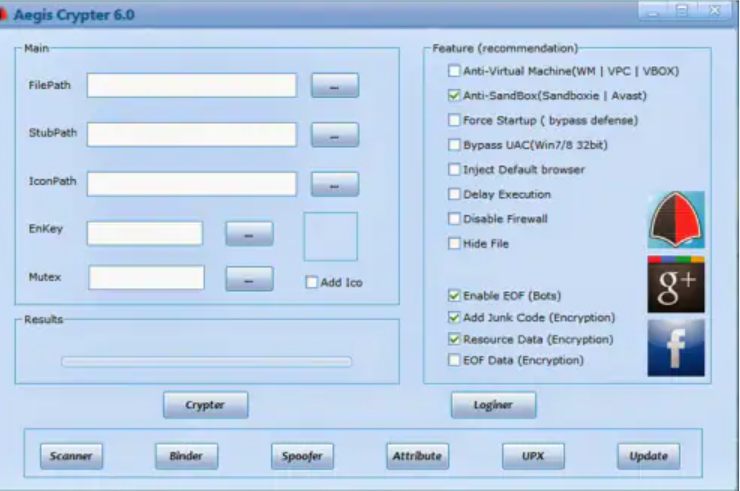
HACK PACK Crypters, Binders, Keyloggers
In the evolving landscape of cyber threats, attackers frequently employ tools such as crypters, binders, and keyloggers to facilitate malicious activities. These components often come bundled in “HACK PACK Crypters,” providing cybercriminals with the ability to obfuscate malware, combine malicious payloads with legitimate files, and stealthily capture sensitive user data. Threat actors leverage such tools […]
ATM Card Cloning All Tools 2025
Cybercriminals continually refine their methods to exploit financial systems, with ATM Card cloning remaining a significant threat. Attackers now utilize highly sophisticated tools to steal card data, bypass security measures, and withdraw funds illegally. These tools employ advanced techniques, including skimming, magnetic stripe manipulation, and malware deployment, which create significant risks for banks and individuals. To develop […]
OpenBullet Anomaly 2024
In 2024, automated credential-testing frameworks have become one of the most dangerous tools in a cybercriminal’s arsenal, enabling large-scale account takeover attacks with frightening efficiency. These sophisticated platforms have evolved beyond simple brute-force tools into modular attack systems that combine credential stuffing, vulnerability scanning, and session hijacking capabilities. OpenBullet Anomaly 2024 role in modern cyberattacks […]
CT Eagles MBY 2.2.0.4 Original Version
In the ever-evolving landscape of cyber threats, specialized tools designed to exploit banking and financial systems have become increasingly sophisticated. Among these, a particular category of malware has emerged that specifically targets online banking sessions, payment platforms, and financial applications. The 2024 version of these banking trojans represents a significant evolution in capability, combining traditional […]