Fullwidth Featured
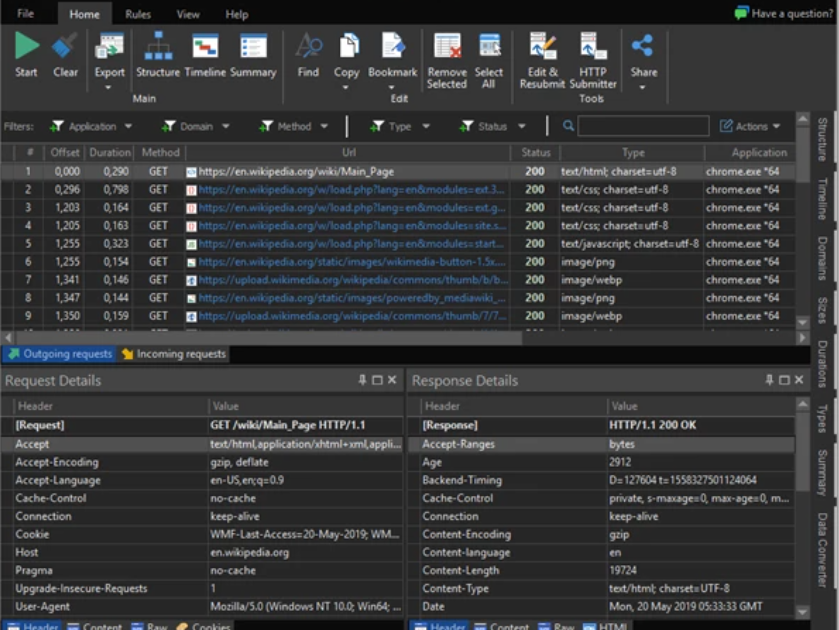
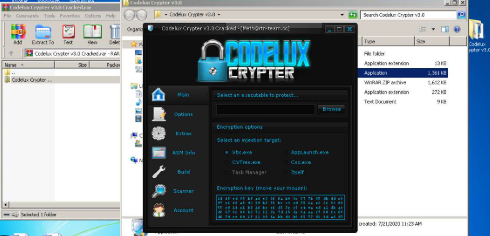
Codelux Crypter v3.0 Cracked
Codelux Crypter v3.0 Cracked have become a critical tool for cybercriminals, enabling them to bypass security measures and deploy malware undetected. Cracked versions of such tools, often leaked or illegally distributed, lower the technical barrier for attackers, allowing even those with minimal expertise to launch sophisticated attacks. These crypters are commonly used in ransomware campaigns, […]
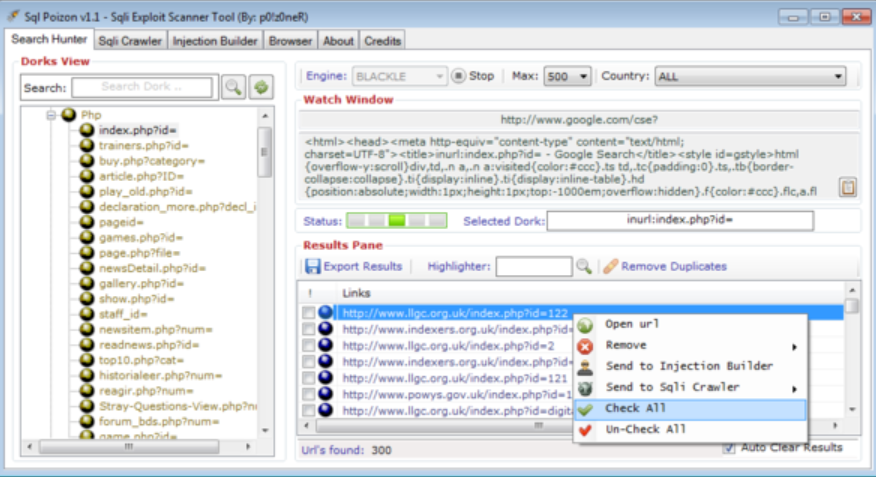
SQLi-DB-SQL Injection Dork Scanner v1.0
SQLi-DB-SQL Injection remains one of the most critical vulnerabilities in web applications, allowing attackers to manipulate databases and extract sensitive information. Automated tools designed to exploit these vulnerabilities play a significant role in both offensive security testing and malicious cyberattacks. Among these tools, SQLi dork scanners are widely used to identify vulnerable websites by leveraging […]
CyberSeal Crypter 2025 Cracked
In today’s threat landscape, CyberSeal Crypter 2025 Crackedplay a significant role in enabling cybercriminals to bypass security defences. These tools are frequently used to obfuscate malicious payloads, making them undetectable by traditional antivirus solutions. By encrypting, compressing, or modifying signatures, crypters allow attackers to deliver ransomware, spyware, and trojans without raising suspicion. Cracked or illegally […]
Trillium-security-multisploit-tool-v4-private-edition
In today’s evolving threat landscape, advanced exploitation frameworks have become a critical tool for both security professionals and malicious actors. One such tool, often referenced in penetration testing and cyberattack simulations, is a Trillium-security-multisploit designed to automate and streamline the exploitation of multiple vulnerabilities. These tools play a dual role—helping ethical hackers assess security defenses while […]
Proxifier Standard Edition V4.03 X64 with Keys
In the realm of cybersecurity, specific tools designed initially for legitimate purposes can be repurposed for malicious activities. One such example is Proxifier Standard Edition V4.03 X64, a powerful network utility that enables users to redirect and manage application traffic through proxy servers. While this software serves legitimate use cases, such as bypassing network restrictions […]