Pandora hVNC Cracked 2024
The rise of advanced remote access tools in cyberattacks has significantly increased the sophistication of modern threats. Among these tools, “Pandora hVNC Cracked 2024” has gained notoriety for enabling stealthy, persistent access to compromised systems. Often distributed through phishing campaigns or exploit kits, this tool allows attackers to bypass security measures and maintain undetected control over victim machines. Its ability to evade detection while providing full remote access makes it a favoured choice for cybercriminals conducting espionage, data theft, and ransomware deployments.
Download Link 1
Download Link 2
Download Link 3
Download Link 4
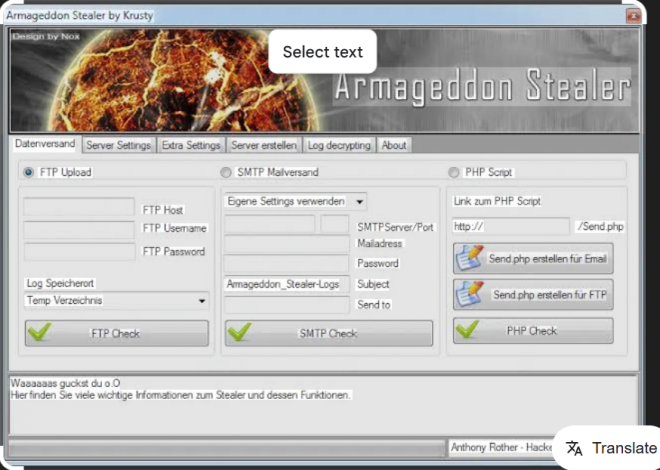
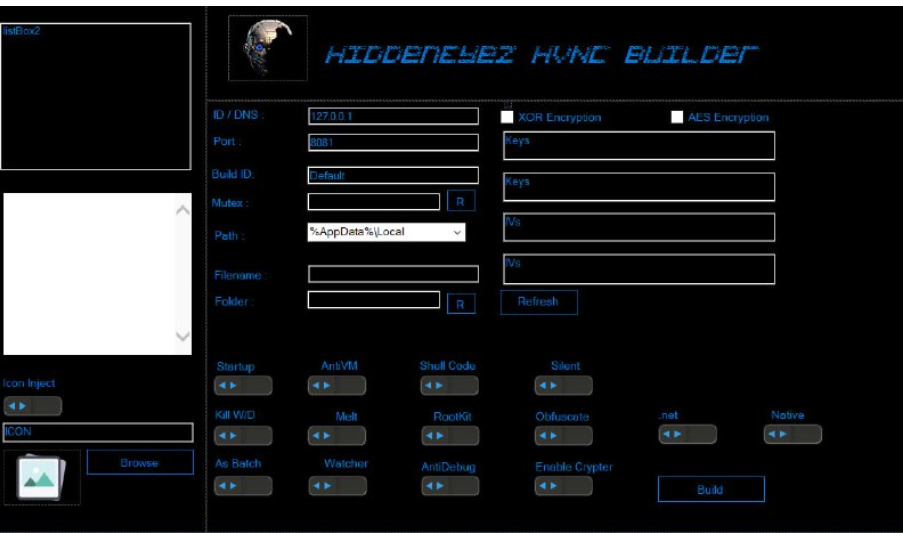
This software is a modified, illicit version of a legitimate remote administration tool, repurposed for malicious use. It operates as a hidden Virtual Network Computing (VNC) solution, granting attackers remote control over a victim’s desktop while remaining undetected by the user. Typical malicious applications include credential theft, surveillance, lateral movement within networks, and the delivery of secondary payloads, such as ransomware or spyware. Due to its cracked nature, it is often distributed through underground forums, eliminating licensing restrictions and making it accessible to less technically skilled attackers.
Key Features of Pandora hVNC Cracked 2024
| Feature | Description |
| Hidden VNC | Operates in a stealth mode, avoiding detection by users or basic security tools. |
| Process Injection | Injects into legitimate processes to evade endpoint detection. |
| Persistence Mechanisms | Establishes long-term access via registry modifications or scheduled tasks. |
| Anti-Analysis Techniques | Detects and avoids sandboxing or virtual machine environments. |
| Encrypted C2 Communication | Uses secure channels to communicate with attacker-controlled servers. |
| Credential Harvesting | Captures keystrokes, clipboard data, and stored credentials. |
How Pandora hVNC Cracked 2024 Works
Infection and Execution
The software typically infiltrates systems through phishing emails, malicious downloads, or exploit kits. Once executed, it employs process hollowing or DLL injection to embed itself into a trusted system process (e.g., explorer.exe). This technique helps it evade basic process-based detection mechanisms.
Stealth and Persistence of Pandora hVNC Cracked 2024
To avoid detection, the tool operates in a hidden desktop mode, ensuring that any remote interactions remain invisible to the logged-in user. It establishes persistence by creating scheduled tasks, modifying registry run keys, or even deploying kernel-mode drivers in more advanced cases. Some variants also turn off security software or manipulate logs to erase traces of their activity.
Payload Delivery and C2 Communication
Once active, the software connects to a command-and-control (C2) server using encrypted protocols, such as HTTPS or custom TLS tunnels. Attackers can then deploy additional payloads, such as info-stealers or ransomware, directly through the established channel. The HVNC functionality allows them to interact with the desktop in real-time, mimicking legitimate user actions to bypass behavioural analysis tools.
Evasion Techniques
To hinder analysis, the software may check for virtualized environments, delay execution, or use code obfuscation. Some versions also employ rootkit-like capabilities to hide network connections and processes from monitoring tools.
By combining these techniques, the tool provides attackers with a powerful, covert means of maintaining access and executing malicious activities while minimizing the risk of detection.