Parasite HTTP Botnet with All Plugins 2025
Modern cyberattacks increasingly rely on sophisticated botnets that leverage legitimate web protocols to blend into normal network traffic. The Parasite HTTP Botnet with All Plugins 2025 represents a dangerous evolution in this space, combining the stealth of HTTP-based communication with modular attack capabilities. Unlike traditional botnets that use easily detectable IRC or custom protocols, this threat operates through standard web traffic, making it exceptionally difficult to distinguish from legitimate user activity. Its plugin-based architecture allows attackers to customize functionality for diverse malicious campaigns, from DDoS attacks to credential harvesting, while maintaining a low profile in compromised networks. The availability of pre-configured plugins has lowered the technical barrier for cybercriminals, contributing to its rapid adoption in both targeted attacks and broad malicious campaigns.
Download Link 1
Download Link 2
Download Link 3
Download Link 4
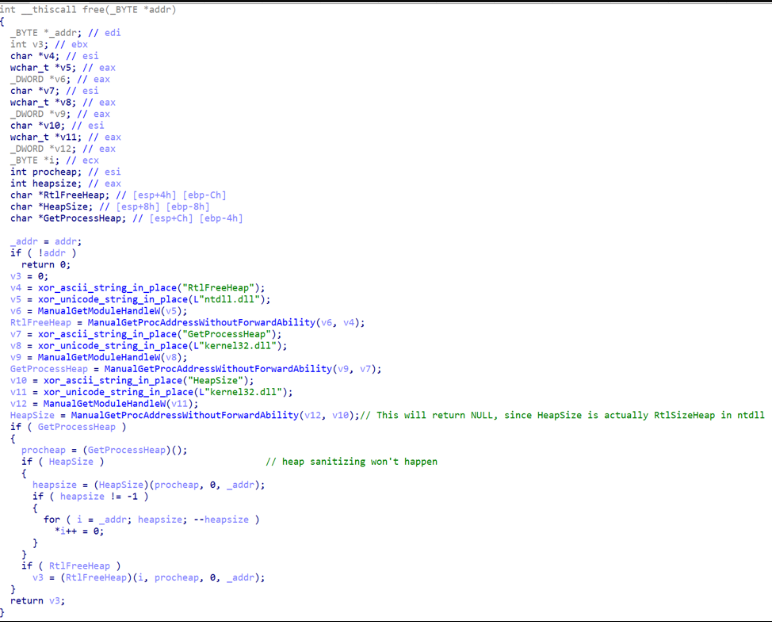
This software is a modular botnet framework that uses HTTP/HTTPS protocols for command-and-control (C2) communication. It functions as a malware toolkit that infects devices and organizes them into a coordinated attack network under the attacker’s control. The botnet primarily spreads through exploit kits, phishing campaigns, and malicious software bundles. Once installed on a victim machine, it establishes persistence and connects to the C2 server, awaiting further instructions. The “all plugins” designation refers to its comprehensive suite of malicious modules that can be activated remotely, allowing attackers to deploy multiple attack vectors from a single infection. This makes it particularly valuable for cybercriminals who want to maximize their returns from each compromised device.

Key Features
| Feature | Description |
| HTTP/HTTPS C2 | Blends malicious traffic with normal web activity |
| Modular Plugins | Supports on-demand loading of attack modules |
| Process Injection | Conceals activity within legitimate processes |
| Persistent Infection | Survives reboots via multiple mechanisms |
| Geo-Targeting | Can restrict attacks by geographic location |
| Encrypted Configs | Obfuscates bot settings to evade analysis |
| Plugin Ecosystem | Includes DDoS, info stealer, proxy, and crypto miner modules |
| Self-Propagation | Can spread laterally through networks |
How Parasite HTTP Botnet 2025 Works
1. Initial Infection Vector
The botnet employs multiple distribution methods:
- Exploit Kits: Targets browser and plugin vulnerabilities
- Phishing Lures: Malicious Office documents with macros
- Software Bundling: Hidden in pirated/cracked applications
- Drive-by Downloads: Compromised websites with fake updates
2. Installation & Persistence
Upon execution, the malware:
- Conducts environment checks for security tools/VMs
- Drops payload in %AppData% or %Temp% directories
- Establishes persistence through:
- Registry Run keys
- Scheduled tasks
- Windows service creation
- Injects into explorer.exe or other trusted processes
3. C2 Communication
The bot maintains contact through:
- HTTP POST requests mimicking API calls
- Custom headers containing encrypted commands
- Rotating C2 domains using DGA (Domain Generation Algorithm)
- Fallback channels through cloud storage APIs
4. Plugin System Operation
The core innovation is its modular attack system:
DDoS Module
- Executes HTTP flood, Slowloris, or TCP attacks
- Adjusts intensity based on victim hardware
- Can target specific application endpoints
Infostealer Plugin
- Harvests browser credentials and cookies
- Captures clipboard content (for crypto theft)
- Logs keystrokes and screenshots
Proxy Module
- Turns infected devices into SOCKS proxies
- Routes attacker traffic through victims
- Often sold as “residential proxies” in underground markets
Cryptominer Plugin
- Deploys XMRig or similar miners
- Adjusts CPU usage to avoid detection
- Mines to attacker-controlled pools
5. Attack Execution
When activated, plugins:
- Receive encrypted configurations from C2
- Allocate system resources without crashing host
- Implement evasion techniques:
- Traffic randomization
- Process hollowing
- Sleep obfuscation
- Report results/stats back to C2
6. Self-Preservation
The botnet includes advanced protection:
- Watchdog processes that restart crashed components
- Auto-update mechanism for plugins
- Sandbox detection that disables keylogging in VMs
Competitor malware removal (kills other bot processes)


