Poenix Keylogger 2025 Cracked
Cyberattacks have evolved significantly in recent years, with keyloggers remaining a persistent threat due to their ability to capture sensitive user data stealthily. Among these, cracked versions of keylogging software—often distributed illegally—pose an even greater risk, as they bypass security measures and licensing restrictions, making them attractive tools for malicious actors. Poenix Keylogger 2025 tools are frequently used in credential theft, corporate espionage, and other cybercrimes, as they leverage their ability to operate undetected while exfiltrating valuable information.
Download Link 1
Download Link 2
Download Link 3
Download Link 4
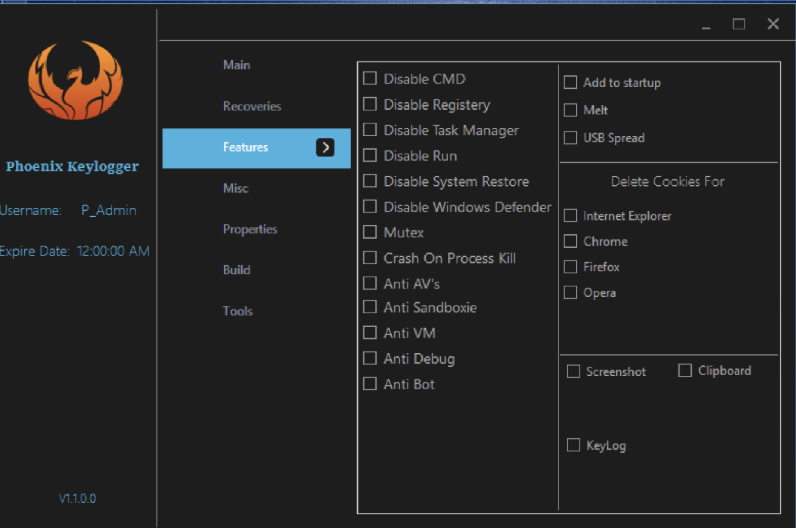
This software is a type of surveillance tool designed to record keystrokes on a target system, logging everything from passwords to chat messages. While legitimate versions may be used for monitoring purposes, such as parental control or employee oversight, cracked variants are typically repurposed for malicious activities. The software operates covertly, often disguising itself as a benign process to evade detection by security software. Its capabilities extend beyond simple keystroke logging, including features like screen capture, clipboard monitoring, and remote data exfiltration.
Key Features of Poenix Keylogger 2025
| Feature | Description |
| Keystroke Logging | Records all keyboard inputs, including passwords and typed messages. |
| Stealth Mode | Hides processes and files to avoid detection by antivirus or system scans. |
| Remote Data Exfiltration | Sends captured data to a remote server or attacker-controlled endpoint. |
| Screen Capture | Takes periodic screenshots to visually monitor user activity. |
| Clipboard Monitoring | Logs any data copied to the clipboard, such as passwords and credit card numbers. |
| Persistence Mechanisms | Ensures the software remains installed after system reboots. |
| Customizable Triggers | Allows attackers to activate logging based on specific applications or events. |
How Poenix Keylogger 2025 Works
The software employs several techniques to infiltrate, persist, and exfiltrate data from a target system. Below is a breakdown of its functionality:
Delivery and Installation
- The payload is typically delivered via phishing emails, malicious downloads, or exploit kits. Once executed, the installer may use obfuscation or packing techniques to evade signature-based detection.
- In some cases, the software exploits vulnerabilities in the operating system or applications to gain elevated privileges, ensuring deeper access.
Persistence Mechanisms
- To maintain long-term access, the software may modify registry keys, create scheduled tasks, or inject itself into legitimate system processes. This ensures it remains active even after a system restart.
Data Capture Techniques of Poenix Keylogger 2025
- Keystroke Logging: The software hooks into keyboard input functions at the operating system (OS) level, intercepting keystrokes before they reach applications.
- Screen Capture: It periodically takes screenshots, often triggered by specific events (e.g., visiting a banking website).
- Clipboard Monitoring: By monitoring the system clipboard activity, it captures copied text, which may include sensitive data.
Exfiltration Methods
- Collected data is usually encrypted and transmitted to a command-and-control (C2) server via HTTP, FTP, or other protocols. Some variants may store logs locally until an internet connection is available.
- To avoid raising suspicion, the software may mimic legitimate traffic or use domain generation algorithms (DGAs) to bypass network-based detection.
Evasion Tactics
- The software employs anti-analysis techniques, such as detecting virtual machines or sandbox environments, to hinder reverse engineering.
- It may also turn off security software or modify firewall rules to ensure uninterrupted operation.
By combining these techniques, the software effectively operates as a spyware tool, silently harvesting sensitive data while remaining undetected for extended periods. Understanding its mechanisms is crucial for developing effective countermeasures, such as behavioral analysis and endpoint detection systems.


