Poulight Stealer cracked
Poulight Stealer is a potent information-stealing malware designed to extract sensitive data from infected systems. The cracked version, widely circulated in underground forums, provides unauthorized access to its premium features without payment. While its use is illegal and poses significant cybersecurity risks, understanding its capabilities is essential for defense and awareness.
Download Link 1
Download Link 2
Download Link 3
Download Link 4
What is Poulight Stealer?
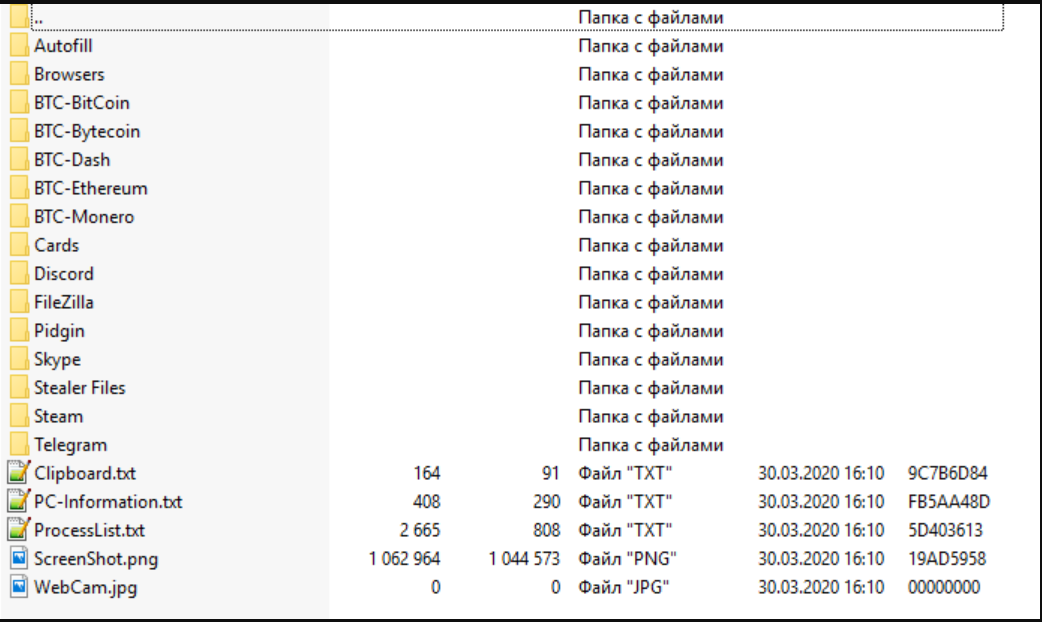
Poulight Stealer is a malicious tool that infiltrates systems to harvest credentials, financial data, cryptocurrency wallets, and other personal information. The cracked version bypasses official licensing, allowing cybercriminals to deploy it freely. It operates stealthily, evading detection while exfiltrating data to remote servers controlled by attackers.
| Feature | Description |
|---|---|
| Credential Harvesting | Extracts saved passwords from browsers (Chrome, Firefox, Edge) and FTP clients. |
| Cryptocurrency Theft | Targets wallet files (e.g., Exodus, Electrum) and monitors the clipboard to hijack crypto transactions. |
| System Information Logging | Gathers system specs, OS version, and installed software for profiling the victim. |
| Keylogging | Records keystrokes to capture login credentials and other sensitive inputs. |
| Screen Capture | Takes screenshots of the victim’s screen to extract visual information. |
| Anti-Detection Mechanisms | Employs obfuscation and virtual machine (VM) evasion to bypass antivirus and analysis tools. |
| Discord Token Theft | Steals Discord authentication tokens to hijack user sessions and accounts. |
| Auto-Update Functionality | Keeps the malware updated with the latest techniques to maintain effectiveness. |
| Custom C2 Communication | Allows attackers to set and use custom command-and-control servers for data exfiltration. |
Why Use Poulight Stealer Cracked?
Despite its illegal nature, cybercriminals use the cracked version of Poulight Stealer due to:
- Cost-Free Access: Avoids paying for the official version while retaining full functionality.
- High Success Rate: Effectively bypasses security measures on many systems.
- Versatility: Targets a wide range of data, making it valuable for identity theft and fraud.
- Ease of Deployment: User-friendly interfaces and tutorials in hacking communities lower the barrier to entry.


