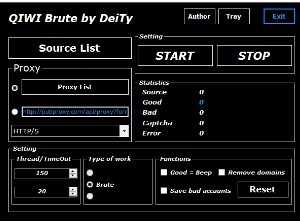
QIWI Brute 2024
QIWI Brute 2024 is a specialized cybersecurity tool designed for penetration testers and ethical hackers to assess the strength of QIWI wallet security. It simulates brute-force attacks to identify weak credentials and vulnerabilities in payment systems. This tool is intended solely for authorized security research and must never be used for illegal activities.
Download Link 1
Download Link 2
Download Link 3
Download Link 4

What Is QIWI Brute 2024?
QIWI Brute 2024 is an automated brute-forcing utility that tests QIWI wallet accounts for weak passwords and security flaws. Unlike malicious hacking tools, it serves as a legitimate means for security professionals to evaluate financial system resilience. By identifying vulnerabilities, organizations can implement stronger authentication measures to protect user funds.
Detailed Features
- Multi-Threaded Attacks: Leverages parallel processing for faster credential testing.
- Proxy Support: Routes requests through proxies to avoid IP bans and detection.
- Custom Wordlists: Allows integration of personalized password dictionaries for targeted attacks.
- CAPTCHA Bypass: Implements advanced techniques to circumvent basic CAPTCHA protections.
- Session Management: Resumes interrupted attacks without losing progress.
- User-Agent Rotation: Randomizes HTTP headers to mimic legitimate traffic.
- Rate Limit Evasion: Adjusts request timing to avoid triggering security locks.
- Two-Factor (2FA) Testing: Supports testing of SMS or email-based 2FA weaknesses.
- Logging & Reporting: Generates detailed logs of tested credentials and successful breaches.
- API Integration: Works with QIWI’s payment system interface for structured testing.
Why Use QIWI Brute 2024?
Security researchers and financial institutions use QIWI Brute 2024 to proactively identify weak points in digital payment systems. By simulating real-world attack scenarios, ethical hackers can help strengthen authentication protocols, enforce stricter password policies, and enhance fraud prevention mechanisms. This tool is critical for compliance testing and safeguarding financial assets.
Additional Information & Education
- Legal Implications: Unauthorized use of accounts without permission violates cybersecurity laws.
- Ethical Hacking: Always obtain explicit consent before testing any financial system.
- Mitigation Strategies: Enable strong 2FA, monitor login attempts, and enforce complex passwords.
- Responsible Disclosure: Report discovered vulnerabilities in QIWI for patching.
Download Link 1
Download Link 2
Download Link 3
Download Link 4


