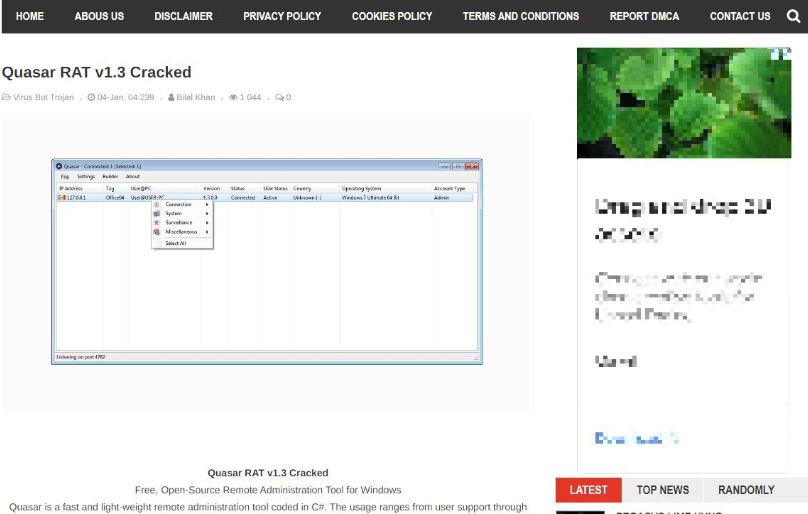
Quasar RAT v1.3 Cracked
Cyber threats continue to evolve, with remote access trojans (RATs) playing a significant role in modern attacks. One such tool, a cracked version of a well-known RAT, has spread widely across underground forums, enabling malicious actors to gain unauthorized access to systems. Quasar RAT v1.3 Cracked empowers attackers to conduct espionage, steal data, and deliver additional malware payloads. These cracked versions, in particular, eliminate licensing restrictions and lower the barrier to entry, making powerful surveillance tools easily accessible to less-skilled cybercriminals.
Download Link 1
Download Link 2
Download Link 3
Download Link 4
This software functions as a remote administration tool, but threat actors have repurposed it for malicious activities. While legitimate remote access tools support IT management and troubleshooting, this cracked variant mainly serves for covert surveillance and unauthorized control. Attackers often distribute it via phishing emails, malicious downloads, or exploit kits. After installation, they gain full control of the target system, allowing them to execute commands, log keystrokes, extract data, and even activate webcams or microphones—all without the victim’s awareness.
Key Features of Quasar RAT v1.3 Cracked
| Feature | Description |
| Remote Shell Access | Provides command-line control over the infected system. |
| Keylogging | Logs keystrokes to steal credentials and sensitive data. |
| Screen Capture | Takes screenshots of the victim’s desktop. |
| File Exfiltration | Uploads, downloads, or deletes files on the compromised machine. |
| Persistence Mechanisms | Ensures the malware remains active after system reboots. |
| Webcam & Microphone Access | Enables spying via the victim’s hardware. |
| Process Manipulation | Terminates or spawns processes to evade detection. |
How Quasar RAT v1.3 Cracked Works
The malware employs several techniques to infiltrate, persist, and execute its payload. Below is a breakdown of its functionality:
Infection & Delivery
The initial infection typically occurs through social engineering, such as a malicious email attachment or a fake software installer. Once executed, the malware may exploit vulnerabilities in the system to escalate privileges or disable security software.
Persistence
To maintain access, the malware modifies system registry keys or creates scheduled tasks, ensuring it runs every time the system starts. Some variants also inject their code into legitimate processes to avoid detection.
Command & Control (C2) Communication
The malware establishes a connection to a remote server controlled by the attacker. This communication is often encrypted or disguised as normal traffic (e.g., HTTPS) to bypass network monitoring. The C2 server sends commands, which the malware executes on the victim’s machine.
Payload Execution
Depending on the attacker’s objectives, the malware can:
- Steal Data: Harvest credentials, documents, and browser histories via keyloggers and file searches.
- Spread Laterally: Move across a network by exploiting weak passwords or unpatched vulnerabilities.
- Download Additional Malware: Fetch secondary payloads, such as ransomware or spyware.
Evasion Techniques
To avoid detection, the malware may:
- Use process hollowing (running malicious code within a legitimate process).
- Disable security tools via Windows Management Instrumentation (WMI) or PowerShell scripts.
- Employ obfuscation to hide its network traffic.


