Revenge RAT V 0.2 with Tutorial
Revenge RAT v0.2 with tutorial is a next-generation Remote Access Trojan designed for covert system infiltration and persistent control. This lightweight yet powerful tool combines fileless execution, advanced evasion techniques, and modular plugin support, making it a significant threat to both individual users and enterprise networks. Bundled with a detailed tutorial, Revenge RAT v0.2 enables even less experienced hackers to deploy sophisticated attacks, from data exfiltration to ransomware deployment.
Download Link 1
Download Link 2
Download Link 3
Download Link 4
What is Revenge RAT v0.2 With Tutorial?
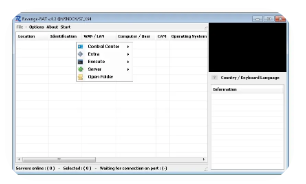
Revenge RAT v0.2 is a Windows-based RAT distributed in underground hacking communities as a customizable malware solution. Unlike traditional RATs, it operates with low detection rates due to its polymorphic code generation and process injection techniques. The included tutorial provides step-by-step instructions for:
Payload creation
C2 (Command & Control) setup
Persistence mechanisms
Data exfiltration
This version introduces enhanced anti-analysis features, including sandbox detection and debugger evasion, making it harder for security tools to identify.
Detailed Features of Revenge RAT v0.2
| Feature Category | Technical Specifications |
|---|---|
| Remote Control | Full desktop access, mouse/keyboard control |
| Data Theft | Browser password extraction, clipboard logging, file exfiltration |
| Surveillance | Screen capture, microphone recording, webcam activation |
| Persistence | Registry autorun, scheduled tasks, service installation |
| Evasion Techniques | Process hollowing, API unhooking, junk code injection |
| C2 Communication | Encrypted HTTP/HTTPS with Telegram/Discord fallback |
| Plugin System | Supports custom modules (keylogger, ransomware, DDoS) |
| Anti-Analysis | VM/sandbox detection, debugger checks |
| Tutorial Content | Step-by-step guides for: • Deployment • Botnet management • Anti-forensics |
Why Do Hackers Use Revenge RAT v0.2?
Easy to Deploy – Tutorial lowers the learning curve.
Low Detection Rate – Polymorphic code evades most AVs.
Flexible Attack Options – Plugins allow for ransomware, spyware, or DDoS.
Stealthy Operation – Runs in memory (fileless) or injects into trusted processes.


