RWX Rat 2024
RWX RAT (Read-Write-Execute Remote Access Trojan) 2024 represents the latest evolution in sophisticated malware, combining advanced penetration techniques with unprecedented stealth capabilities. Emerging in early 2024, this Windows-based threat has quickly gained notoriety among cybersecurity professionals due to its modular architecture and ability to bypass modern security measures. Unlike traditional RATs, RWX 2024 employs innovative memory manipulation techniques that make detection exceptionally challenging for conventional antivirus solutions.

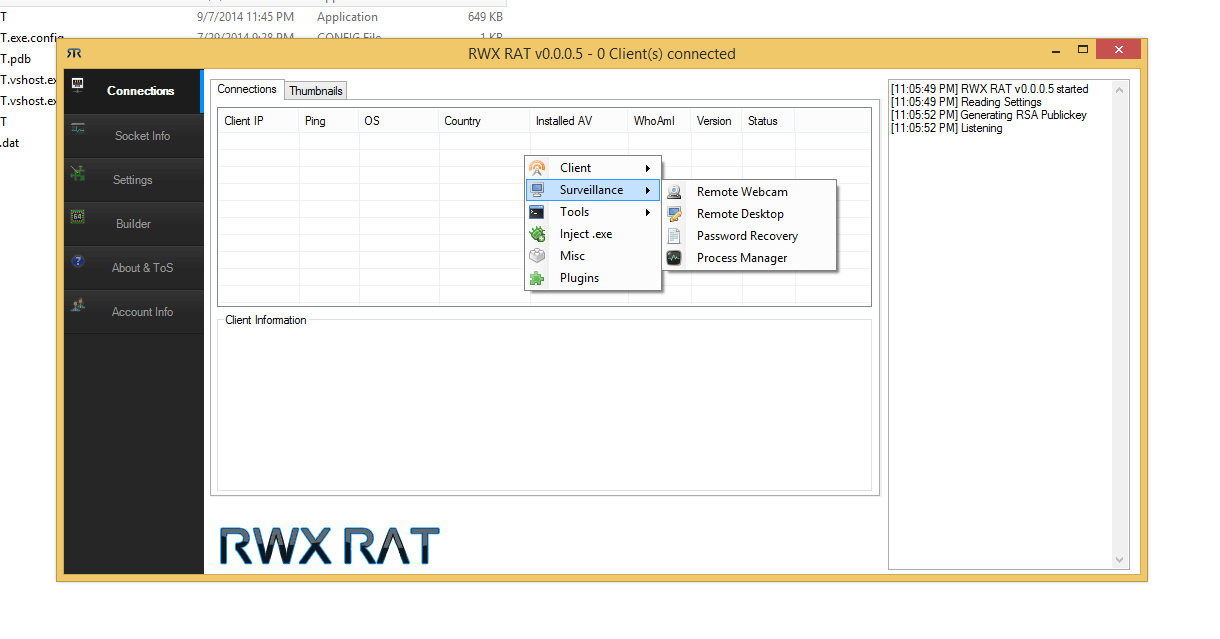
What is RWX RAT 2024?
RWX RAT 2024 is a polymorphic remote access tool that utilizes legitimate Windows functions to hide malicious activities. The name derives from its unique ability to manipulate memory permissions (Read-Write-Execute) dynamically, allowing it to operate without writing suspicious files to disk. This RAT specializes in privilege escalation, lateral movement, and data exfiltration, making it particularly dangerous for corporate networks. Its command-and-control infrastructure uses decentralized protocols, including blockchain-based communication in some variants.
Detailed Features of RWX RAT 2024
| Feature Category | Technical Description |
|---|---|
| Memory-Resident Operation | Executes entirely in RAM using process hollowing and reflective DLL injection. |
| Dynamic Code Obfuscation | Real-time code mutation with AES-encrypted payload segments. |
| Zero-Day Exploit Integration | Comes pre-loaded with unpublished vulnerabilities for initial access. |
| Cloud Storage Abuse | Uses legitimate services (Google Drive, Dropbox) for C2 communication. |
| Biometric Data Theft | Can harvest Windows Hello fingerprint/facial recognition data. |
| GPU-Based Cryptojacking | Utilizes victim’s graphics card for silent cryptocurrency mining. |
| AI-Powered Behavior | Machine learning models adapt to user patterns to avoid detection. |
| VPN/Virtual Machine Detection | Identifies and bypasses analysis environments. |
| Ransomware Module | Optional plug-in for automated file encryption and extortion. |
| Voice Synthesis | Can generate synthetic voice commands for social engineering. |
Why Do Hackers Prefer RWX RAT 2024?
- Forensic Evasion: Leaves minimal disk artifacts for incident responders.
- Targeted Attacks: Precision targeting of financial and healthcare sectors.
- Profit Maximization: Combines data theft, cryptojacking, and ransomware.
- Adaptive Infrastructure: Shifts between TOR, I2P, and legitimate cloud services.
- Low Resource Usage: Consumes under 2% CPU to avoid suspicion.
Advanced Protection Strategies
- Memory Protection: Implement tools like Windows Defender Credential Guard.
- Network Segmentation: Isolate critical systems using micro-segmentation.
- Behavioral Analysis: Deploy solutions like Cisco Secure Endpoint.
- Privilege Management: Enforce strict least-privilege access controls.
- Threat Intelligence: Monitor underground forums for new variants.


