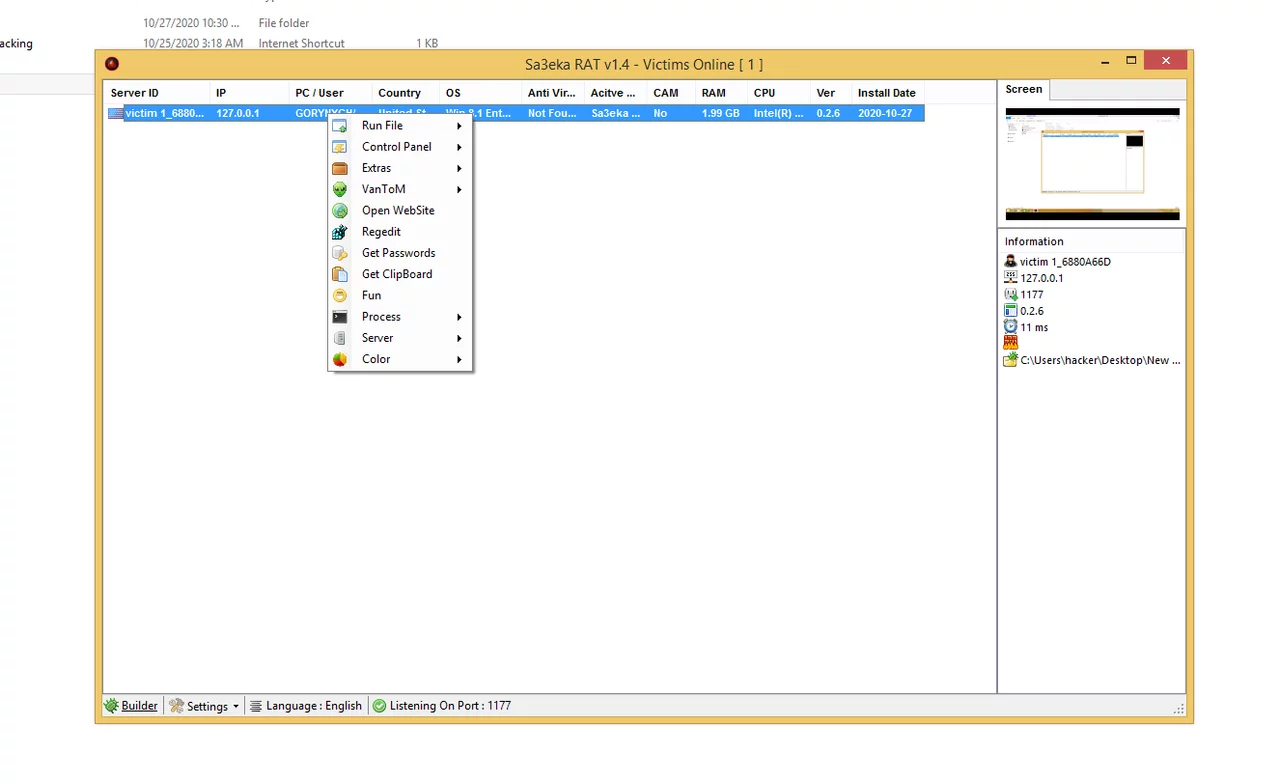
Sa3eka RAT v1.4
Sa3eka RAT v1.4 is an emerging remote access trojan that first appeared in underground hacking forums in early 2024. Designed for persistent surveillance and data exfiltration, this Arabic-origin malware (“Sa3eka” meaning “hunter”) has quickly gained popularity among sophisticated threat actors due to its unique evasion techniques and multi-vector attack capabilities. Unlike conventional RATs, version 1.4 introduces innovative features specifically tailored for Middle Eastern targets, including Arabic-language phishing templates and regional bank trojan modules.

What is Sa3eka RAT v1.4?
Sa3eka RAT v1.4 is a modular espionage tool that combines traditional remote access functionality with advanced cyber-espionage features. The malware primarily targets Windows systems but includes experimental modules for Android devices. Its architecture follows a plugin-based design, allowing attackers to customize functionality based on their objectives. The RAT’s most distinctive feature is its “Sleep Mode” capability, where it can remain dormant for extended periods before activating during specific system events.
Detailed Features of Sa3eka RAT v1.4
| Feature Category | Technical Specifications |
|---|---|
| Stealth Injection | Uses process doppelgänging and atom bombing techniques |
| Regional Targeting | Pre-configured Arabic keyboard layout interception |
| Financial Module | Dedicated banking trojan for Middle Eastern financial institutions |
| Scheduled Operation | Activates only during specific hours/days to avoid detection |
| Screen Capture | Intelligent screenshot capture when specific applications are open |
| Audio Surveillance | Records from microphones and captures VoIP calls |
| Document Theft | Auto-targets PDF, Word, and Excel files with Arabic content |
| Self-Destruction | Emergency wipe capability via SMS command |
| Tor Communication | Built-in Tor client for anonymous C2 communication |
| USB Propagation | Creates a hidden autorun.inf files with Arabic filenames |
| Defense Evasion | Detects and bypasses common Middle Eastern antivirus products |
Why Do Hackers Choose Sa3eka RAT v1.4?
- Regional Specialization: Optimized for Middle Eastern targets and languages.
- Operational Security: Multiple fallback C2 channels ensure persistence.
- Financial Focus: Dedicated modules for regional banking systems.
- Low Profile: Average memory footprint under 5MB.
- Customizable: Payload can be rebuilt with different obfuscation for each target.
- Multi-Platform: Experimental support for Android expands attack surface.


