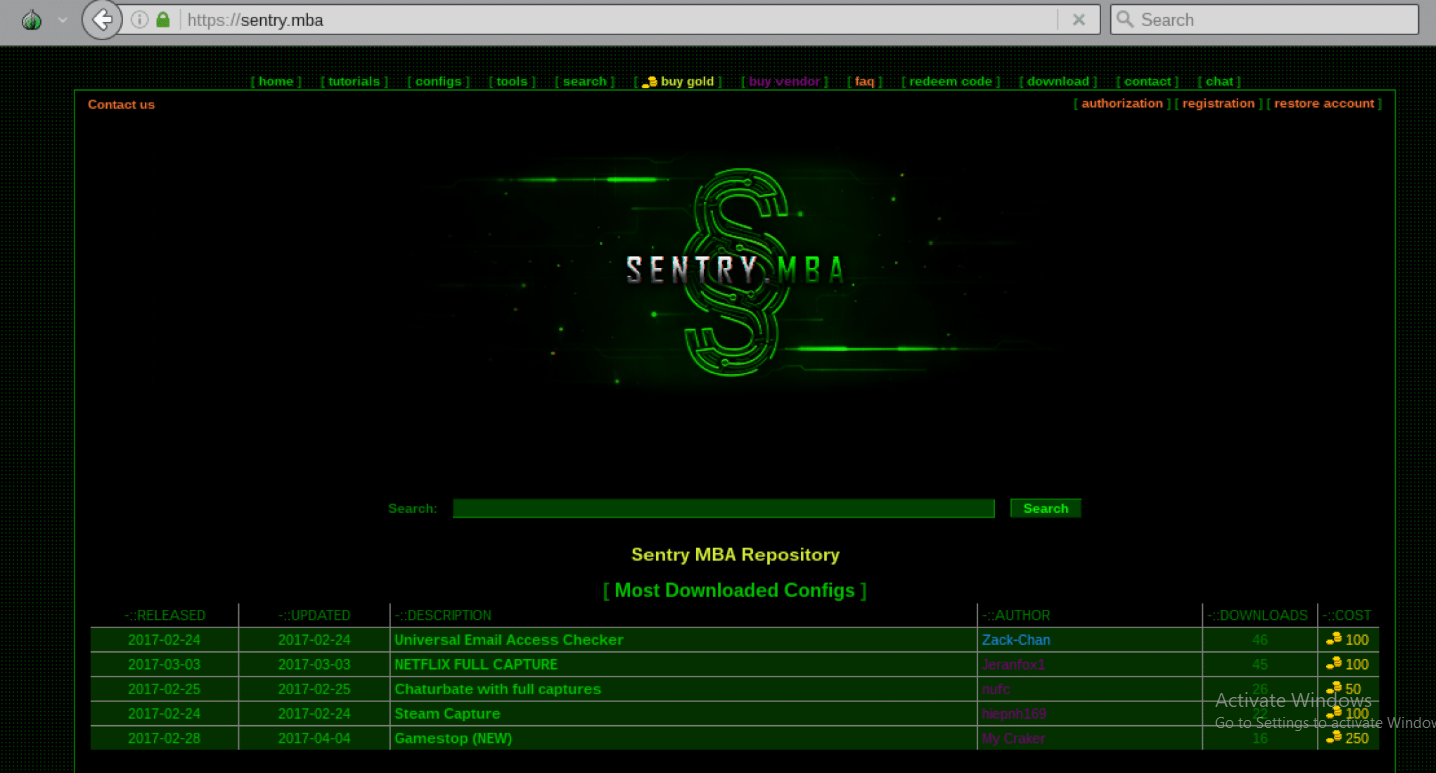
Sentry MBA 1.4.1 Cracked
Automated credential-testing tools have become a cornerstone of modern cyberattacks, enabling threat actors to breach online accounts at an unprecedented scale. Among these tools, modified versions of legitimate security testing software pose a particular threat when weaponized by malicious actors. These cracked or repurposed tools often incorporate enhanced evasion capabilities and underground exploit modules not found in their original versions. In 2025, such tools are frequently employed in credential stuffing attacks against e-commerce platforms, social media accounts, and financial services, resulting in billions of dollars in annual fraud losses while remaining difficult to detect due to their ability to mimic legitimate traffic patterns.
Download Link 1
Download Link 2
Download Link 3
Download Link 4
Sentry MBA 1.4.1 software is a specialized credential validation platform originally designed for security professionals to test authentication systems. The modified version discussed here has been altered to remove license restrictions and augmented with additional attack modules sourced from underground forums. It functions as an automated login testing suite capable of processing thousands of credential combinations per minute against target websites. While penetration testers might use the legitimate version to identify weak passwords, cybercriminals deploy the modified version to verify stolen credential databases before monetizing them through account takeover (ATO) attacks, credential reselling, or fraudulent transactions.
Key Features
| Feature | Description |
| Multi-threaded Engine | Processes 1000+ simultaneous login attempts across multiple targets |
| Proxy/VPN Support | Rotates IPs through SOCKS5/HTTP proxies to evade IP-based blocking |
| CAPTCHA Bypass | Integrates with third-party solving services and AI-based recognition |
| Custom Configuration | Allows creation of site-specific attack templates (headers, form data, etc.) |
| Session Hijacking | Steals and reuses authentication tokens to bypass MFA |
| Detailed Reporting | Exports valid credentials with associated account metadata (balance, etc.) |
| Modular Plugin System | Supports add-ons for specific platforms (banking, social media, etc.) |
How Sentry MBA 1.4.1 Cracked Works
The attack process follows a sophisticated workflow designed to maximize success while minimizing detection:
- Credential Preparation Phase
- Imports credential lists (typically email: password combinations) from breach compilations
- Filters and formats credentials using regex patterns to match target requirements
- Applies mutation rules (e.g., “Password123” → “Password123!”) to exploit common variations
- Target Configuration
- Loads pre-built configuration files (“configs”) specifying:
- Login page URLs and request methods (GET/POST)
- Required HTTP headers and cookies
- Form field parameters (username/password field names)
- Success/failure response identifiers
- Loads pre-built configuration files (“configs”) specifying:
- Attack Execution
- Distributes login attempts across multiple threads (typically 500-1000 concurrent)
- Route traffic through proxy lists to avoid rate limiting and IP bans
- Handles CAPTCHAs by either:
- Submitting to solving services (2Captcha, Anti-CAPTCHA)
- Using integrated OCR for simpler challenges
- Implements randomized delays (200- 1500ms) between attempts
- Response Analysis
- Monitors HTTP responses for indicators of successful logins:
- Session cookies in response headers
- Account-specific redirects (e.g., to dashboard pages)
- Balance/account information in response bodies
- Validates sessions by requesting authenticated pages (profile/account info)
- Monitors HTTP responses for indicators of successful logins:
- Post-Exploitation
- For valid credentials:
- Harvests available account data (payment methods, contacts, etc.)
- Attempts to achieve session persistence via cookie extraction
- May initiate automated actions (password changes, transfers)
- Exports results in organized formats for:
- Direct monetization (account resale)
- Further attacks (credential stuffing on other platforms)
- For valid credentials:


