Silent Crypto Miner V 2.0.2
In the evolving landscape of cyber threats, cryptojacking has emerged as a lucrative and stealthy attack vector. One such tool, often referred to as Silent Crypto Miner V 2.0.2, exemplifies the growing sophistication of malicious mining software. Unlike traditional malware, which disrupts systems or steals data, this tool operates covertly, hijacking computing resources to mine cryptocurrency for its attackers. Its ability to evade detection while maximizing profitability makes it a favored choice among cybercriminals, particularly in large-scale attacks targeting enterprises and poorly secured networks.
Download Link 1
Download Link 2
Download Link 3
Download Link 4
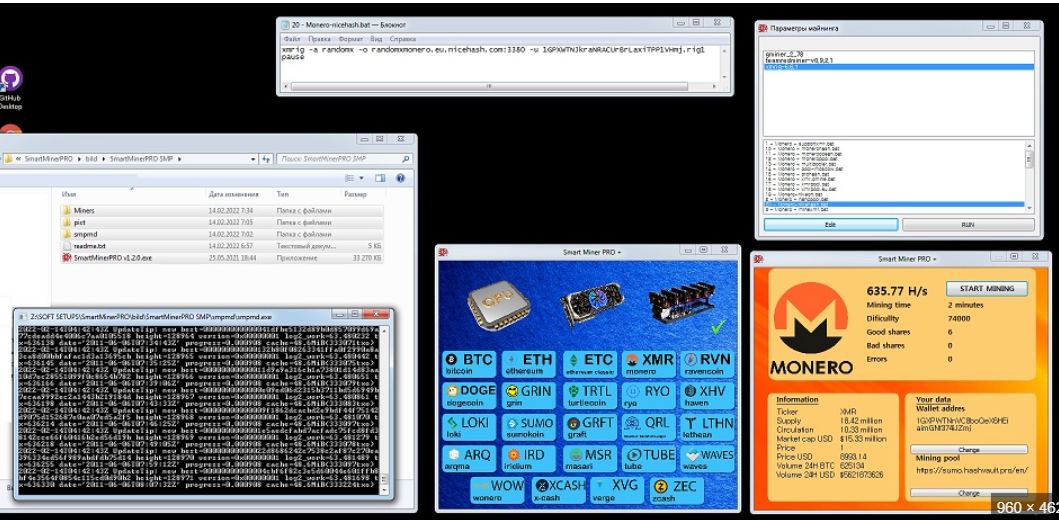
This software is a specialized cryptojacking tool designed to silently infiltrate systems and utilize their processing power for cryptocurrency mining, typically Monero (XMR) due to its privacy-focused features. It is often deployed through phishing campaigns, exploit kits, or compromised software installations. Once active, it runs discreetly in the background, avoiding noticeable performance impacts to prolong its presence. While it can be used ethically in controlled environments for legitimate mining, its primary abuse involves unauthorized deployment on victim machines, turning them into revenue-generating assets for attackers.
Key Features of Silent Crypto Miner V 2.0.2
| Feature | Description |
| Stealth Execution | Operates silently with minimal CPU usage to avoid detection. |
| Persistence Mechanisms | Installs itself to survive reboots (e.g., via registry keys or cron jobs). |
| Anti-Analysis Techniques | Detects virtual machines or sandboxes to evade security researchers. |
| Payload Obfuscation | Uses encryption or packing to hinder reverse engineering. |
| Network Propagation | Spreads laterally across connected devices in a network. |
| Dynamic Pool Switching | Adjusts mining pools to maximize profitability and avoid blacklisting. |
How a Silent Crypto Miner V 2.0.2 Works
Infection and Deployment
The software typically infiltrates systems through:
- Phishing Emails: Malicious attachments or links deliver the payload.
- Exploit Kits: Leveraging vulnerabilities in outdated software (e.g., browsers, plugins).
- Fake Software Bundles: Masquerading as legitimate downloads or cracks.
Once executed, it employs process hollowing or DLL injection to run within a trusted system process (e.g., explorer.exe), making detection harder.
Mining Operations of Silent Crypto Miner V 2.0.2
After establishing persistence, the software connects to a predefined mining pool using the victim’s resources. It uses the XMRig or similar mining libraries, configured to:
- Limit CPU usage to avoid triggering alarms.
- Prioritize mining during low-activity periods to remain unnoticed.
Evasion Techniques
To avoid detection, the software employs:
- Rootkit Functionality: Hides its processes and files from task managers.
- Traffic Masking: Encrypts communication with mining pools to blend with normal traffic.
- User Behaviour Analysis: Pauses mining when the user is active to reduce performance lag.


