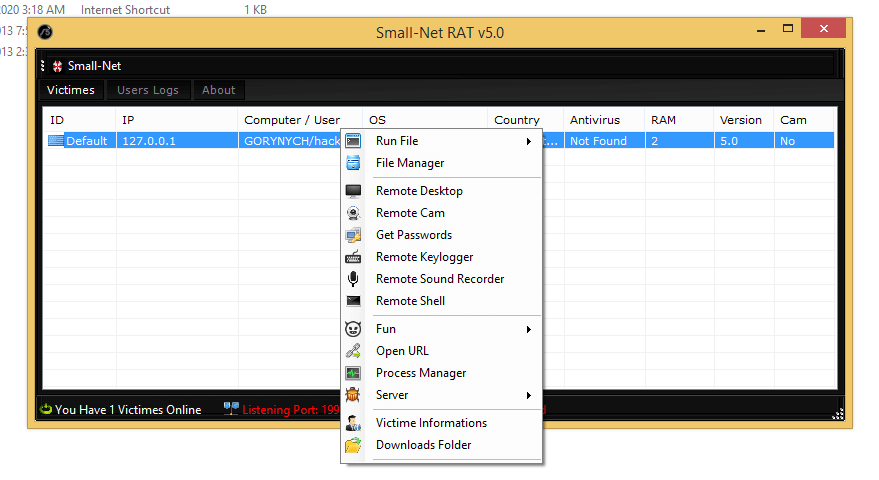
Small Net RAT v5.0
Small Net RAT v5.0 represents the latest evolution of a long-standing remote access tool that has been refined for modern cyber operations. First appearing in underground forums in early 2024, this iteration maintains the malware’s signature compact size while adding sophisticated new capabilities. Unlike bulkier competitors, Small Net RAT specializes in rapid deployment and minimal system footprint, making it particularly dangerous for targets with limited security resources. Its ability to masquerade as legitimate network traffic has made it a favorite among hackers looking for reliable, low-profile access.

What is Small Net RAT v5.0?
Small Net RAT v5.0 is a highly optimized remote administration tool that has been repurposed for unauthorized system access. The “Small Net” designation reflects both its modest file size (under 500KB) and its efficient use of network resources. Version 5.0 introduces enhanced encryption protocols and a new plugin architecture that allows real-time functionality upgrades without requiring the main executable to change. This Windows-focused malware operates through a unique “fire-and-forget” communication model, where infected systems periodically check for commands rather than maintaining constant connections.
Detailed Features of Small Net RAT v5.0
| Feature Category | Technical Specifications |
|---|---|
| Compact Delivery | Complete package under 500KB (can be delivered via image files). |
| Dynamic DNS C2 | Uses rotating domain generation algorithm (DGA) for resilience. |
| Process Hollowing | Injects into legitimate Windows processes (explorer.exe, winlogon.exe). |
| Encrypted Storage | All collected data encrypted with ChaCha20 before exfiltration. |
| Smart Keylogging | Only activates when financial/banking sites are detected. |
| Screen Capture | Configurable quality settings to balance stealth and detail. |
| Plugin System | Hot-swappable modules for added functionality (crypto mining, etc.). |
| Persistence | Multiple methods including registry, scheduled tasks, and service creation. |
| Network Evasion | Traffic mimics standard HTTP/HTTPS patterns. |
| USB Spread | Can auto-copy to removable drives with hidden attributes. |
| Self-Defense | Detects and kills analysis tools like Wireshark and Process Hacker. |
| Update Mechanism | Can fetch new versions from pastebin-style sites. |
Why Do Hackers Prefer Small Net RAT v5.0?
- Efficient Operations: Low bandwidth usage avoids network alarms.
- Easy Deployment: Small size bypasses many email attachment filters.
- Adaptable Infrastructure: DGA domains make takedowns ineffective.
- Cost Effective: Requires minimal infrastructure investment.
- High Success Rate: Focused on small-to-medium business targets.
- Plug-and-Play Modules: Can add features as needed per operation.
- Longevity: Previous versions have evaded detection for years.


