SMTP Mailer By Marks Man 2024
In 2024, mass emailing tools play a dual role in both legitimate marketing campaigns and malicious cyber operations. While businesses use them for newsletters and promotions, threat actors frequently exploit these tools for spam, phishing, and malware distribution. SMTP Mailer by Marks Man and disposable email services enable attackers to send thousands of messages while evading detection. Such tools contribute to the growing volume of social engineering attacks, credential harvesting, and ransomware distribution, making them a persistent challenge for email security systems.
Download Link 1
Download Link 2
Download Link 3
Download Link 4
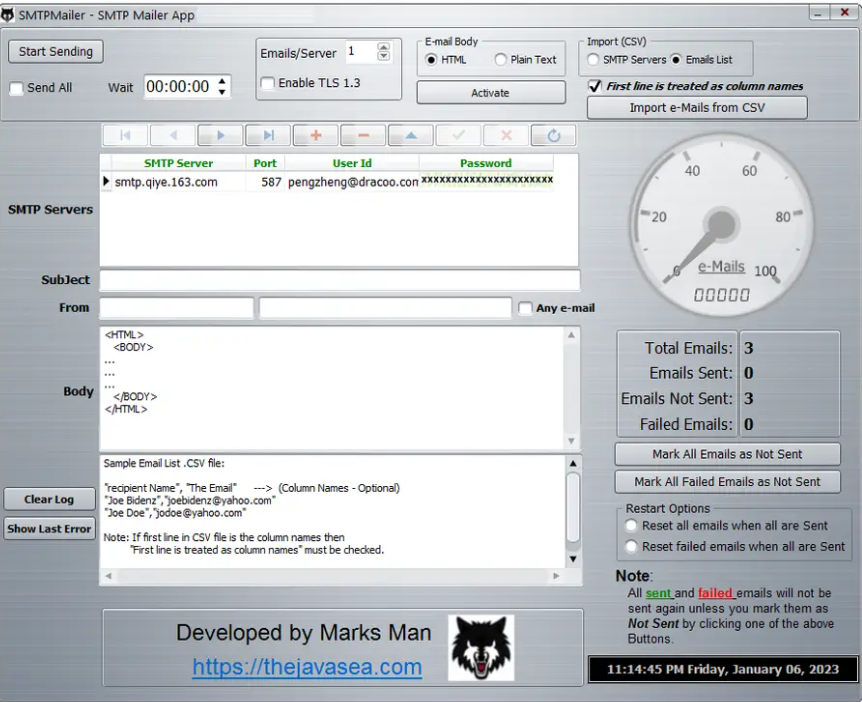
This software is a specialized tool designed to send bulk emails by leveraging SMTP protocols, often with features that bypass standard email security measures. It allows users to customize sender addresses, message content, and delivery timing to maximize reach and avoid spam filters. While marketers may use similar tools for legitimate purposes, malicious actors typically deploy this software for phishing campaigns, malware distribution, or fraudulent schemes. The application often includes built-in proxy support, email template customization, and automated sending capabilities to streamline large-scale operations.

Key Features
| Feature | Description |
| SMTP Server Integration | Supports multiple SMTP servers (legitimate or compromised) for sending emails. |
| Proxy & VPN Support | Rotates IP addresses to avoid blacklisting and maintain anonymity. |
| Email Spoofing | Masks the sender’s address to impersonate trusted entities. |
| Bulk Sending | Processes and dispatches thousands of emails in a single session. |
| HTML & Template Support | Allows rich formatting and dynamic content for convincing phishing emails. |
| Delay & Throttling | Adjusts sending speed to mimic human behavior and evade spam filters. |
| List Management | Imports, segments, and manages recipient email lists efficiently. |
How SMTP Mailer By Marks Man Works
The software automates the process of sending mass emails while incorporating evasion techniques to bypass security measures. Below is a detailed breakdown of its functionality:
1. Setup & Configuration
- SMTP Server Selection: The user configures the software to use either legitimate SMTP services (e.g., Gmail, Outlook) or compromised/hacked servers.
- Sender Spoofing: Attackers often forge the “From” field to impersonate trusted organizations (e.g., banks, corporate entities).
- Email Template Design: Pre-designed HTML templates with embedded links or malicious attachments can be loaded for phishing or malware campaigns.
2. Recipient List Processing
- The software imports a target email list (often obtained from data breaches or scraping tools).
- Lists may be segmented to personalize messages (e.g., using the recipient’s name) for higher engagement.
3. Email Delivery & Evasion
- Proxy Rotation: The tool routes traffic through multiple proxies to avoid IP-based blocking.
- Rate Limiting: Sending speed is adjusted to prevent triggering spam filters (e.g., delaying emails by a few seconds).
- Header Manipulation: Modifies email headers (e.g., X-Mailer, Reply-To) to appear as a legitimate mailing service.
4. Payload Delivery
Depending on the attacker’s goal, the emails may contain:
- Phishing Links: Redirecting victims to fake login pages to steal credentials.
- Malware Attachments: Executable files (.exe, .js) or malicious documents (PDF, Word) that install malware when opened.
- Scam Messages: Fraudulent offers (e.g., fake invoices, lottery wins) to trick users into sending money.
5. Post-Delivery Tracking (Optional)
Some advanced versions include:
- Open/Click Tracking: Logs which recipients interact with the email.
Bounce-Back Analysis: Identifies invalid emails for list refinement.


