Spy MAX v1.0
Spy MAX v1.0 is a sophisticated surveillance tool designed for remote monitoring, often misused by hackers for unauthorized access to target systems. While marketed as a legitimate monitoring solution, its capabilities make it a potent threat in the wrong hands. Understanding its functionality is crucial for cybersecurity professionals to detect and mitigate potential breaches.
Download Link 1
Download Link 2
Download Link 3
Download Link 4
What is Spy MAX v1.0?
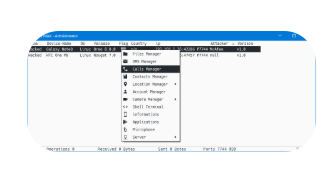
Spy MAX v1.0 is a Remote Access Trojan (RAT) that enables covert surveillance and control over infected devices. It operates stealthily, allowing hackers to monitor activities, steal sensitive data, and execute commands remotely. The tool is commonly distributed through phishing attacks, malicious downloads, or disguised as legitimate software.
Detailed Features of Spy MAX v1.0
| Feature | Description |
|---|---|
| Real-Time Screen Capture | Records or streams the victim’s screen in real-time. |
| Keylogging | Logs all keystrokes to capture passwords, messages, and other typed data. |
| Webcam & Microphone Access | Secretly activates cameras and microphones for live surveillance. |
| File System Explorer | Browses, downloads, uploads, or deletes files on the infected system. |
| Process Manager | Views, starts, stops, or kills running processes. |
| Password Recovery | Extracts saved credentials from browsers, email clients, and applications. |
| Persistent Installation | Ensures the malware remains active after system reboots. |
| Remote Shell Access | Executes command-line instructions on the victim’s machine. |
| Clipboard Monitoring | Captures copied text, including sensitive data like crypto wallet addresses. |
| Anti-Detection Techniques | Uses encryption and obfuscation to evade antivirus detection. |
| Spread via USB Drives | Can propagate by infecting removable storage devices. |
| Data Exfiltration | Sends stolen information to a remote server via encrypted channels. |
Why Do Hackers Use Spy MAX v1.0?
- Stealthy operation (runs silently in the background).
- Comprehensive spying features (covers screen, audio, keystrokes, and files).
- Easy deployment (often spread via phishing or fake software).
- Low detection rate (uses evasion techniques to bypass security software).


