Spy max v2.0
In an era where digital surveillance and data theft have become increasingly sophisticated, tools like Spy Max v2.0 have emerged as potent threats in the cybercrime arsenal. This advanced spyware represents a significant evolution in surveillance malware, combining traditional monitoring capabilities with modern evasion techniques. Unlike basic keyloggers or simple data stealers, this software offers attackers comprehensive control over compromised systems, enabling everything from real-time activity monitoring to remote file access. Its availability in underground markets has made it particularly appealing to both cybercriminals and unethical surveillance actors, contributing to its growing prevalence in targeted attacks against individuals and organizations alike.
Download Link 1
Download Link 2
Download Link 3
Download Link 4
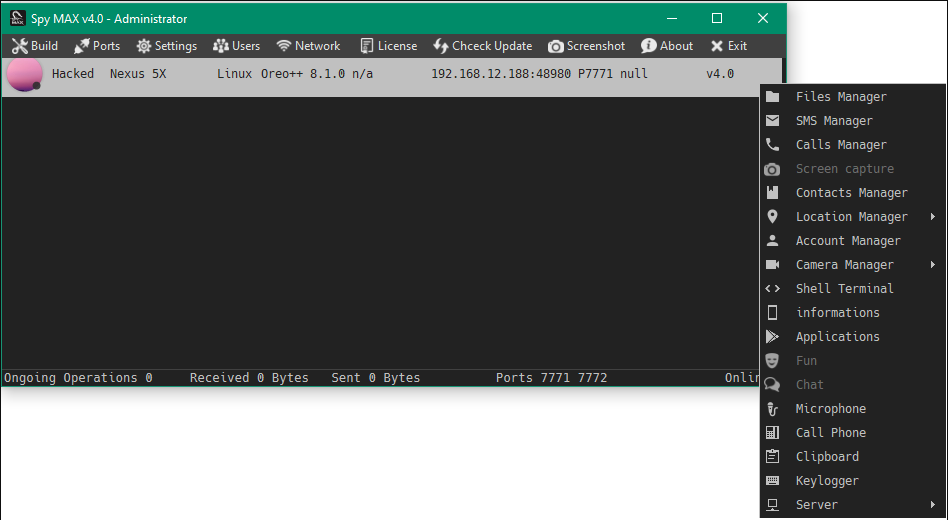
This software is a feature-rich surveillance tool designed to operate covertly on infected systems while gathering extensive user data. It functions as a full-fledged remote access trojan (RAT) with additional spyware capabilities, allowing attackers to monitor nearly all aspects of a victim’s digital activity. The malware is typically distributed through social engineering tactics, such as disguised as legitimate software updates, pirated applications, or email attachments. Once installed, it establishes persistence and begins collecting data ranging from keystrokes and screenshots to microphone recordings and browsing history. The collected information is then transmitted to command-and-control (C2) servers, often encrypted to avoid detection. Its modular architecture allows attackers to customize which surveillance features are active, making it adaptable to various malicious scenarios from corporate espionage to personal harassment.

Key Features
| Feature | Description |
| Keylogging | Captures all keyboard input, including passwords and messages |
| Screen Capture | Takes periodic screenshots or records live desktop activity |
| Audio Surveillance | Activates microphone to record ambient conversations |
| Webcam Access | Hijacks camera for visual surveillance |
| File Exfiltration | Steals documents, images, and other sensitive files |
| Browser Monitoring | Tracks browsing history, downloads, and form inputs |
| Clipboard Logging | Captures copied text, including cryptocurrency addresses |
| Process Injection | Hides within legitimate processes to evade detection |
| Persistence | Maintains access through registry edits and system services |
| Anti-Analysis | Detects and avoids virtual machines and security tools |
How Spy max v2.0 Works
1. Distribution and Infection
The malware employs multiple infection vectors:
- Social Engineering: Masquerades as cracked software, game mods, or productivity tools
- Phishing Campaigns: Distributed via malicious email attachments (e.g., fake invoices, resumes)
- Drive-by Downloads: Automatically installed through compromised websites
- Infected Removable Media: Spreads via USB devices with autorun exploits
2. Installation and Evasion
Upon execution, the malware performs several critical operations:
- Environment Checks: Scans for virtualization, sandboxes, or security tools
- Persistence Mechanisms:
- Creates registry entries for automatic startup
- Installs itself as a Windows service
- Modifies system firewall rules to allow C2 communication
- Process Hollowing: Injects malicious code into legitimate processes (e.g., explorer.exe)
3. Surveillance Operations
The malware activates multiple monitoring modules:
Input Monitoring
- Logs all keystrokes with timestamps and application context
- Tracks mouse movements and clicks
- Captures clipboard content in real-time
Visual Surveillance
- Takes screenshots at configurable intervals (e.g., every 30 seconds)
- Activates webcam when available (often with LED disabled)
- Records active windows and applications in use
Audio Collection
- Activates microphone during voice calls or periods of activity
- Compresses audio recordings for efficient exfiltration
- Some variants can detect and record VoIP conversations
Data Harvesting
- Steals saved credentials from browsers and email clients
- Collects documents from recent files and desktop
- Targets specific file types (PDFs, Word docs, spreadsheets)
4. Data Exfiltration
Collected data is processed and transmitted:
- Local Storage: Temporarily stores data in encrypted hidden folders
- Compression: Uses efficient algorithms to reduce file sizes
- C2 Communication:
- Primary: Encrypted HTTPS connections to attacker servers
- Fallback: Email attachments or cloud storage uploads
- Alternative: Peer-to-peer networks for decentralized control
- Data Packaging: Organizes information by type and timestamp
5. Remote Control Capabilities
Advanced versions include:
- Live desktop viewing and remote control
- File system navigation and download/upload functionality
- Command execution via hidden command prompt
- Ability to deploy additional payloads
6. Self-Preservation
- Regularly checks for and kills security processes
- Modifies its own signatures to evade detection
- Can disable Windows Defender and other security tools
- Uses domain generation algorithms (DGAs) for resilient C2


