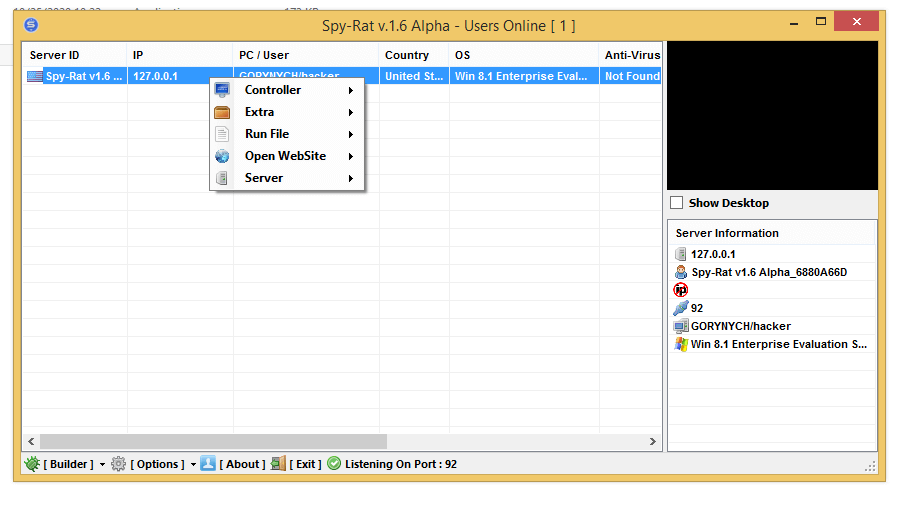
Spy Rat v1.6 Alpha
Spy Rat v1.6 Alpha is an advanced surveillance-focused Remote Access Trojan (RAT) that has emerged in underground cyber communities as a powerful tool for covert data collection. This pre-release version demonstrates significant improvements over previous iterations, with enhanced stealth mechanisms and refined data exfiltration techniques. Designed for targeted espionage, Spy Rat v1.6 Alpha specializes in long-term infiltration, allowing attackers to monitor victims undetected for extended periods while gathering sensitive personal, financial, and corporate data.

What is Spy Rat v1.6 Alpha?
Spy Rat v1.6 Alpha is a sophisticated spying tool that operates silently in the background of infected Windows systems. Unlike traditional RATs that prioritize remote control, this version focuses on passive surveillance, including keylogging, screen recording, microphone activation, and document theft. Its “Alpha” designation indicates it is still in development, yet already demonstrates advanced anti-analysis features, including virtual machine detection and behavioral-based evasion. The malware communicates through encrypted channels, often blending its traffic with legitimate cloud storage services to avoid detection.
Detailed Features of Spy Rat v1.6
| Feature Category | Technical Specifications |
|---|---|
| Advanced Keylogging | Logs keystrokes with context awareness (activates on banking/logins). |
| Screen Recording | Captures video of user activity in configurable intervals. |
| Microphone Surveillance | Activates when voice is detected, saves encrypted audio clips. |
| Webcam Capture | Takes periodic images when the camera is accessible. |
| Clipboard Monitoring | Logs copied text, including passwords and crypto wallet addresses. |
| File Exfiltration | Auto-uploads documents (PDF, DOCX, XLSX) to attacker-controlled cloud storage. |
| Browser Data Theft | Extracts saved passwords, cookies, and browsing history. |
| Persistence | Installs as a disguised Windows service or scheduled task. |
| Anti-Sandboxing | Detects virtual environments and delays execution. |
| Encrypted C2 | Uses TLS 1.3 for secure communication with command servers. |
| Self-Destruct | Removes traces if specific security tools are detected. |
| Dynamic Sleep Mode | Reduces activity during high system usage to avoid detection. |
Why Do Hackers Use Spy Rat v1.6 Alpha?
- Stealth Over Speed: Designed for long-term spying rather than quick attacks.
- High-Value Data Theft: Focuses on credentials, financial info, and corporate documents.
- Low Detection Rates: Mimics legitimate software behaviors to evade antivirus scans.
- Cloud-Based Exfiltration: Uses services like Google Drive or Dropbox for data smuggling.
- Customizable Modules: Attackers enable/disable features based on target value.
- Persistent Access: Remains active through reboots and system updates.


