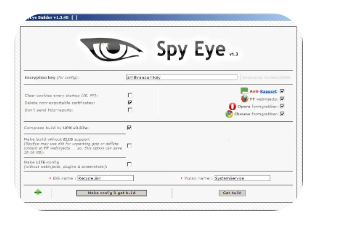
SpyEye Botnet 2024
SpyEye Botnet 2024 marks the alarming resurgence of one of history’s most notorious banking trojans, now upgraded with modern evasion tactics and expanded targeting capabilities. This reengineered malware combines sophisticated web injection frameworks with advanced persistence mechanisms, specializing in financial data theft from both consumer and corporate banking platforms. Its modular architecture allows for real-time updates, enabling threat actors to adapt quickly to security measures while maintaining a low detection profile across global financial systems.

What is SpyEye Botnet 2024?
SpyEye Botnet 2024 is a next-generation financial malware suite distributed through exploit kits and phishing campaigns, designed to automate large-scale banking fraud. The rebooted version features cloud-based C2 infrastructure, AI-assisted target profiling, and blockchain-anonymized payment redirection. Unlike its predecessor, the 2024 variant incorporates virtualized execution environments to evade sandbox detection while maintaining the original’s formidable form-grabbing and web injection capabilities that made SpyEye infamous in the cybersecurity community.
Technical Feature Breakdown
| Feature Category | Operational Specifications |
|---|---|
| Web Injection Framework | Dynamic DOM manipulation for 200+ global banking portals |
| Data Capture | Form grabbing, HTML5 canvas fingerprinting, and biometric spoofing |
| Transaction Hijacking | Real-time interception of 2FA tokens and payment verification steps |
| Evasion Suite | VM-aware execution stalls, API call spoofing, and TLS 1.3 C2 channels |
| Persistence | BIOS-level rootkit (x86 systems) + UEFI firmware infection (x64) |
| Lateral Movement | Exploits Zerologon and PetitPotam vulnerabilities for domain escalation |
| Cloud Integration | AWS/GCP-abusing C2 nodes with fast-flux DNS rotation |
| Mobile Sync | Companion APK for intercepting banking app notifications (Android) |
| Analytics Dashboard | Real-time victim profiling with geofenced attack recommendations |
Operational Advantages for Threat Actors
- Financial Precision – Machine learning identifies high-value targets based on browsing patterns
- Anti-Forensic Design – Memory-only execution leaves minimal disk artifacts
- Supply Chain Abuse – Compromised SaaS platforms serve as distribution vectors
- Profit Scaling – Automated wire transfer templates adapt to regional banking UIs
- Resilient Infrastructure – Blockchain-based C2 failover prevents single-point takedowns


