SpyMax 4 RAT Cracked
Cybercriminals increasingly rely on commercially available spyware tools to conduct surveillance and data theft operations. Among these threats, cracked or pirated versions of legitimate monitoring software pose a significant risk, as they are often repurposed for malicious activities. SpyMax 4 RAT provides attackers with powerful capabilities while evading legal restrictions, making them attractive for unauthorized surveillance, financial fraud, and corporate espionage. Their widespread availability on underground forums lowers the barrier to entry, enabling even low-skilled attackers to deploy sophisticated spying campaigns.
Download Link 1
Download Link 2
Download Link 3
Download Link 4
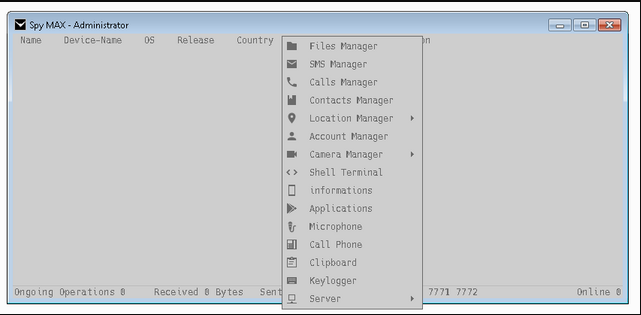
This software is a modified, unauthorized version of a commercial monitoring tool designed to operate as a remote access trojan (RAT). It allows attackers to secretly monitor and control compromised devices, harvesting sensitive data such as keystrokes, screenshots, and login credentials. Typically, it is used in cybercrime operations targeting individuals, businesses, or unsuspecting victims through phishing, malicious downloads, or social engineering. Unlike legitimate monitoring software, cracked versions lack security updates and are often bundled with additional malware, increasing their danger.
Key Features
| Feature | Description |
| Live Screen Capture | Takes real-time screenshots of the victim’s device. |
| Keylogging | Records all keystrokes, including passwords and messages. |
| Webcam & Mic Access | Secretly activates cameras and microphones for surveillance. |
| File Exfiltration | Steals documents, images, and other stored files. |
| Remote Control | Allows attackers to execute commands and manipulate the system. |
| Persistence | Ensures the malware remains installed after reboots. |
| Data Upload to C2 | Sends stolen information to a remote server. |
| Evasion Techniques | Disguises itself as a legitimate process to avoid detection. |
How SpyMax 4 RAT Works
Infection & Deployment
The malware is typically distributed through:
- Phishing Emails: Malicious attachments or links that install the payload when opened.
- Fake Software Crack Sites: Victims download what they believe is a legitimate tool, only to infect themselves.
- Malvertising: Compromised or fake ads that redirect users to malware-laden downloads.
Once executed, the malware installs itself silently, often using deceptive filenames or hiding within system directories.
Persistence & Stealth
To maintain long-term access, the malware employs:
- Autostart Entries: Modifies registry keys or startup folders to relaunch on system boot.
- Process Injection: Runs within trusted system processes to blend in with normal activity.
- Anti-Detection Measures: Disables security software notifications or mimics benign applications.
Data Collection & Exfiltration
Once active, the malware performs:
- Keystroke Logging: Captures all typed inputs, including banking credentials and private messages.
- Screen Recording: Takes periodic screenshots to monitor user activity.
- Audio/Video Surveillance: Activates webcams and microphones without the victim’s knowledge.
- File Theft: Scans the system for valuable documents (PDFs, Word files, databases) and uploads them.
Command & Control (C2) Communication
The malware connects to an attacker-controlled server using encrypted channels (HTTP/HTTPS). The C2 server can:
- Send commands (e.g., start recording, delete files).
- Retrieve stolen data in real time.
- Push updates or additional malware modules.


