SQLi-DB-SQL Injection Dork Scanner v1.0
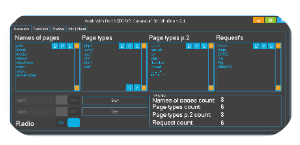
SQLi-DB-SQL Injection remains one of the most critical vulnerabilities in web applications, allowing attackers to manipulate databases and extract sensitive information. Automated tools designed to exploit these vulnerabilities play a significant role in both offensive security testing and malicious cyberattacks. Among these tools, SQLi dork scanners are widely used to identify vulnerable websites by leveraging search engine queries (dorks) that expose poorly secured databases. While penetration testers use such tools ethically to uncover weaknesses, malicious actors exploit them for data breaches, making it crucial to understand their functionality for effective defense.
Download Link 1
Download Link 2
Download Link 3
Download Link 4
This software is designed to automate the process of finding websites vulnerable to SQL injection by using predefined search patterns (dorks). It scans search engine results for websites with weak input validation and then tests them for SQL injection flaws. Typically used by security researchers and penetration testers, the tool helps identify and patch vulnerabilities before attackers can exploit them. However, in the wrong hands, it can facilitate unauthorized database access, leading to data theft or website defacement.
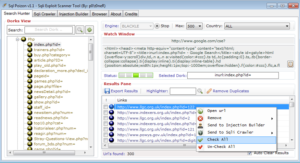
Key Features of the Software
| Feature | Description |
| Dork-Based Scanning | Uses preconfigured or custom search queries to find potentially vulnerable sites. |
| Automated Injection Testing | Tests detected URLS for SQLi vulnerabilities by sending malicious payloads. |
| Multiple Database Support | Works with MySQL, Microsoft SQL Server (MSSQL), Oracle, and other standard database systems. |
| Proxy Integration | Allows anonymous scanning through proxy servers to avoid IP blocking. |
| Payload Customization | Supports manual input of SQLi payloads for targeted attacks. |
| Vulnerability Reporting | Generates logs of vulnerable sites for further analysis or exploitation. |
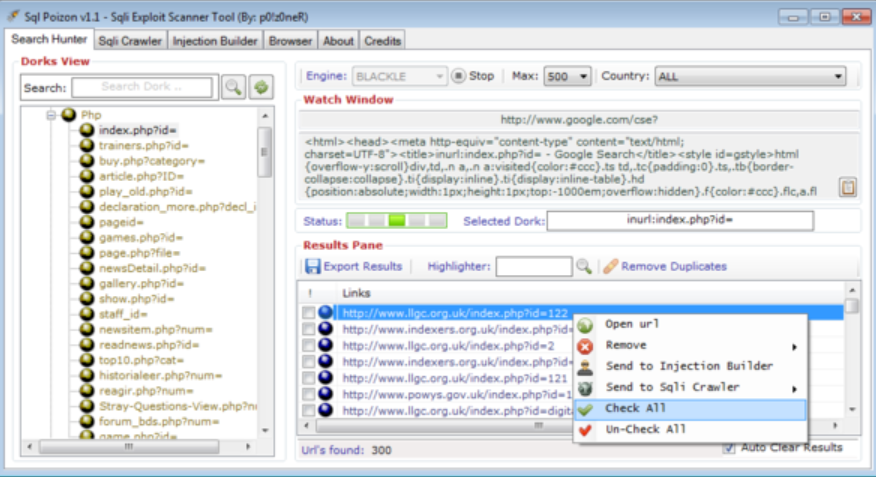
How the SQLi-DB-SQL Injection: Techniques & Functionality
- Dork Collection & Search Engine Queries
- The tool starts by using a list of predefined or user-supplied “dorks”.
- These dorks are submitted to search engines like Google to retrieve URLS with potential SQLi flaws.
- URL Filtering & Target Selection
- The scanner filters out irrelevant links and focuses on dynamic pages.
- It may exclude certain domains or prioritize high-value targets (e.g., .gov and .edu).
- SQL Injection Testing
- The tool sends crafted SQLi payloads to test for vulnerabilities.
- It analyzes server responses for error messages (e.g., database errors, unusual delays) to confirm SQLi flaws.
- Exploitation & Payload Delivery
- If a vulnerability is detected, the tool can escalate attacks by:
- Extracting database names (UNION SELECT schema name FROM information_schema.schemata).
- Dumping table data (UNION SELECT username, password FROM users).
- Executing commands (in cases of advanced SQLi, like stacked queries).
- If a vulnerability is detected, the tool can escalate attacks by:
- Reporting & Logging
- The results are saved in a structured format (e.g., CSV, TXT) listing vulnerable URLS, parameters, and payloads used.
- Some versions may integrate with other exploitation frameworks for further penetration testing.
![Work With Dorks [DORK’s Generator]-Dork Generator](https://blackhatus.com/wp-content/uploads/2025/07/Work-With-Dorks-DORKs-Generator-Dork-Generator-1.png)