SQLi Dumper 9.7
In the evolving landscape of cybersecurity threats, automated exploitation tools have become a significant concern for organizations worldwide. One such tool, often utilised by malicious actors, is designed to automate the process of identifying and exploiting SQLi Dumper 9.7 vulnerabilities in web applications. These vulnerabilities, if left unpatched, can lead to unauthorized data access, data breaches, and even complete system compromise. The tool in question streamlines the attack process, making it accessible even to less-skilled attackers, thereby increasing the frequency and scale of SQLi-based cyberattacks.
Download Link 1
Download Link 2
Download Link 3
Download Link 4
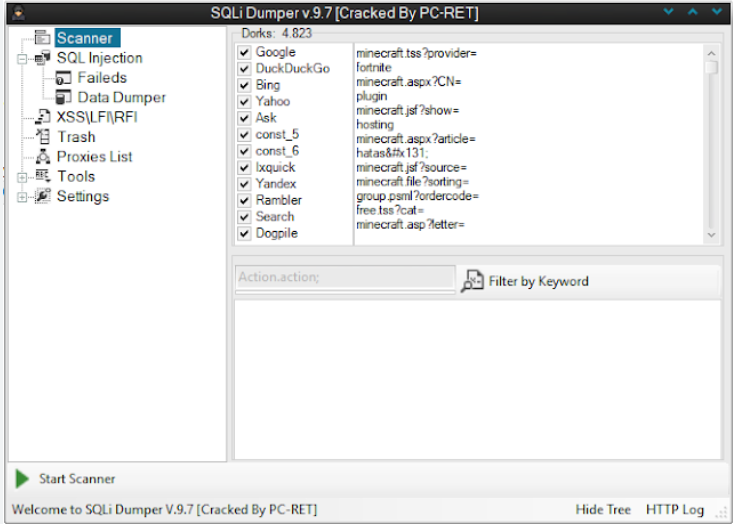
This software is a specialized utility used to scan websites for SQL injection vulnerabilities and subsequently exploit them to extract sensitive data from databases. It automates tasks that would otherwise require manual testing and advanced knowledge of SQLi techniques, making it a popular choice among cybercriminals. Typical uses include harvesting login credentials, personal information, financial records, and other confidential data stored in backend databases. While penetration testers may use similar tools for ethical security assessments, this software is predominantly associated with malicious activities due to its ease of use and effectiveness in breaching vulnerable systems.
Key Features of SQLi Dumper 9.7
| Feature | Description |
|---|---|
| Automated Scanning | Scans target websites for SQL injection vulnerabilities. |
| Exploit Execution | Automates the exploitation process to extract database information. |
| Multiple Database Support | Works with various database systems (e.g., Mysql, MSSQL, Postgresql). |
| Data Extraction | Retrieves table names, columns, and records from vulnerable databases. |
| Proxy Support | Allows attackers to route traffic through proxies to avoid detection. |
| User-Friendly Interface | Provides a graphical interface for ease of use, requiring minimal expertise. |
How the SQLi Dumper 9.7 Works
The software operates through a series of automated steps designed to identify, verify, and exploit SQL injection vulnerabilities. Below is a breakdown of its functionality:
- Target Identification
The user inputs a target URL or a list of URLs to scan. The tool then sends crafted HTTP requests to these URLS, probing for potential SQL injection vulnerabilities by injecting malicious SQL snippets into input fields or URL parameters. - Vulnerability Detection
The tool analyzes server responses for error messages, response delays, or other indicators that suggest a SQL injection flaw. Common techniques include:- Error-Based Detection: Checks for database error messages revealing SQL syntax issues.
- Boolean-Based Detection: Uses actual/false conditions to infer database structure.
- Time-Based Detection: Measures response delays to confirm vulnerabilities.
- Exploitation Phase
Once a vulnerability is confirmed, the tool sends additional payloads to extract database information. This includes:- Enumerating database names, tables, and columns.
- Dumping data from identified tables (e.g., usernames, passwords, credit card details).
- Executing arbitrary SQL commands if privileges permit.
- Payload Delivery
The software dynamically constructs SQL queries tailored to the target database system. For example:- In Mysql, it uses statements to retrieve data.
- In MSSQL, it could leverage stacked questions for further exploitation.
- Data Exfiltration
Extracted data is presented in a structured format within the tool’s interface, allowing attackers to export or misuse it easily. Proxy support helps mask the attacker’s origin, complicating forensic investigations.
![Work With Dorks [DORK’s Generator]-Dork Generator](https://blackhatus.com/wp-content/uploads/2025/07/Work-With-Dorks-DORKs-Generator-Dork-Generator-1.png)