SSH IP Generator, Port Scanne,r RDP Cracker 2024
SSH IP Generator Port Scanner RDP Cracker 2024 is a versatile, all-in-one cybersecurity tool designed for penetration testers, ethical hackers, and network administrators. It combines IP generation, port scanning, and credential cracking to help identify vulnerabilities and strengthen network defenses effectively.
Download Link 1
Download Link 2
Download Link 3
Download Link 4

What Is SSH IP Generator, Port Scanner, RDP Cracker?
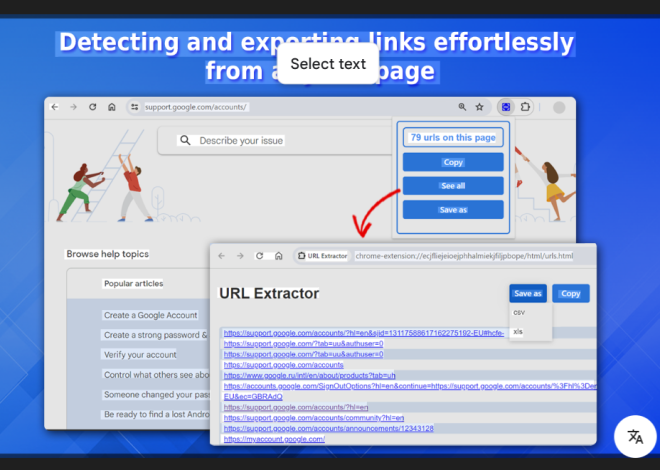
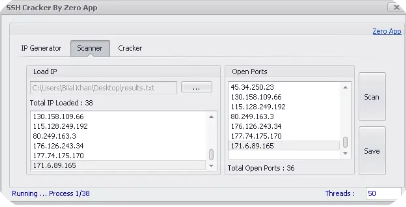
This advanced utility integrates three key functions—an SSH IP generator, a port scanner, and an RDP cracker—into a single platform. It automates the process of discovering active SSH servers, scanning for open ports, and performing brute-force attacks on RDP credentials. Built for accuracy and efficiency, it aids security professionals in uncovering weaknesses before they can be exploited.
Detailed Features
| Feature | Description |
|---|---|
| SSH IP Generator | Automatically generates and validates live SSH server IPs across specified subnet ranges. |
| Port Scanner | Scans target IP addresses for open TCP/UDP ports, detecting services like HTTP, FTP, SSH, and RDP. |
| RDP Cracker | Performs brute-force and dictionary attacks on RDP credentials with multi-threaded support for speed. |
| Custom Wordlists | Supports importing custom wordlists to improve credential cracking success rates. |
| Proxy & VPN Support | Routes scanning and attacks through proxies or VPNs to maintain user anonymity and avoid detection. |
| User-Friendly Interface | Provides both command-line and graphical interfaces for users of all experience levels. |
| Logging & Reporting | Exports scan results and cracked credentials in multiple formats such as TXT and CSV. |
| Multi-Threaded Performance | Enables parallel scanning and attacks to maximize speed without overloading system resources. |
Why Use SSH IP Generator Port Scanner RDP Cracker?
This comprehensive tool helps cybersecurity experts and administrators proactively identify and fix network vulnerabilities. By automating IP discovery, port scanning, and credential testing, it streamlines penetration testing, network hardening, and remote access security audits—ensuring robust protection against unauthorized access.