SSH Rat Keylogger Crypter 3 in 1
SSH RAT Keylogger Crypter 3-in-1 is a sophisticated, multi-functional malware suite that combines remote access, keystroke logging, and file encryption into a single powerful payload. Emerging in underground forums in early 2024, this tool stands out for its ability to bypass modern security measures by leveraging SSH tunneling for stealthy communication. Unlike traditional RATs, this package integrates three critical attack vectors: remote control, credential theft, and data encryption, making it a versatile weapon for hackers targeting both individuals and organizations.
Download Link 1
Download Link 2
Download Link 3
Download Link 4
What is SSH RAT Keylogger Crypter 3-in-1?
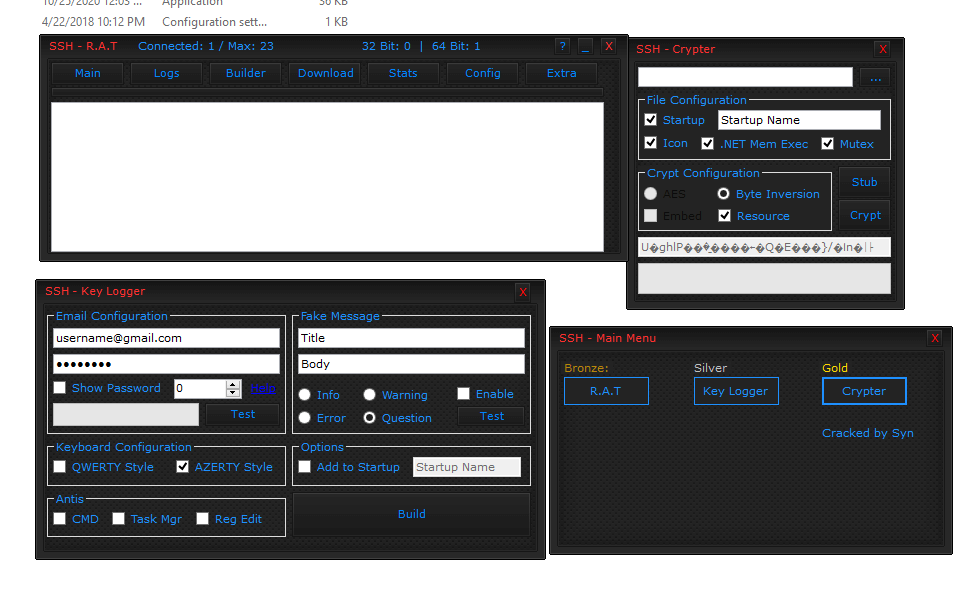
SSH RAT Keylogger Crypter 3-in-1 is a modular cyber-espionage tool that provides attackers with complete system control, real-time keylogging, and ransomware-like file encryption capabilities. The malware uses SSH (Secure Shell) tunneling to mask its command-and-control (C2) traffic as legitimate encrypted connections, evading network monitoring tools. Its three core components remote access, keylogging, and file encryption can operate independently or together, allowing hackers to customize attacks based on their objectives.
Detailed Features
| Feature Category | Technical Specifications |
|---|---|
| SSH-Based C2 | Encrypted communication via SSH tunnels, mimicking admin traffic. |
| Remote Desktop Control | Full GUI access with mouse/keyboard input redirection. |
| Advanced Keylogging | Logs keystrokes, clipboard data, and application focus. |
| File Encryption Module | AES-256 encryption with customizable ransom notes. |
| Persistence | Installs as a hidden service or registry entry. |
| Process Injection | Injects into trusted processes (explorer.exe, svchost.exe). |
| Credential Harvesting | Targets browser passwords, FTP clients, and email credentials. |
| Screen Capture | Takes screenshots during login sessions or banking activity. |
| USB Propagation | Auto-spreads via infected USB drives with hidden partitions. |
| Dynamic Evasion | Detects sandbox environments and delays execution. |
| Multi-OS Support | Works on Windows & Linux (experimental macOS module). |
| Self-Destruct | Removes traces if security tools are detected. |
Why Do Hackers Use SSH RAT Keylogger Crypter 3-in-1?
- All-in-One Attack Suite: Combines RAT, keylogger, and ransomware in a single payload.
- SSH Stealth: Blends into normal encrypted admin traffic, bypassing firewalls.
- High Success Rate: Targets credentials and locks files for double extortion.
- Cross-Platform Capability: Works on Windows and Linux systems.
- Low Detection Rate: Uses legitimate encryption to avoid suspicion.


