StormKitty Stealer 2025
In the ever-evolving landscape of cyber threats, information stealers have become one of the most prevalent and damaging tools in an attacker’s arsenal. These specialized malware variants are designed to covertly harvest sensitive data from infected systems, often leading to financial fraud, identity theft, and corporate espionage. The latest iterations of these stealers demonstrate increasing sophistication, employing advanced evasion techniques and modular architectures that make them particularly dangerous and difficult to detect. StormKitty Stealer 2025 role in modern cyberattacks is particularly concerning as it often serves as the initial foothold for more extensive network compromises.
Download Link 1
Download Link 2
Download Link 3
Download Link 4
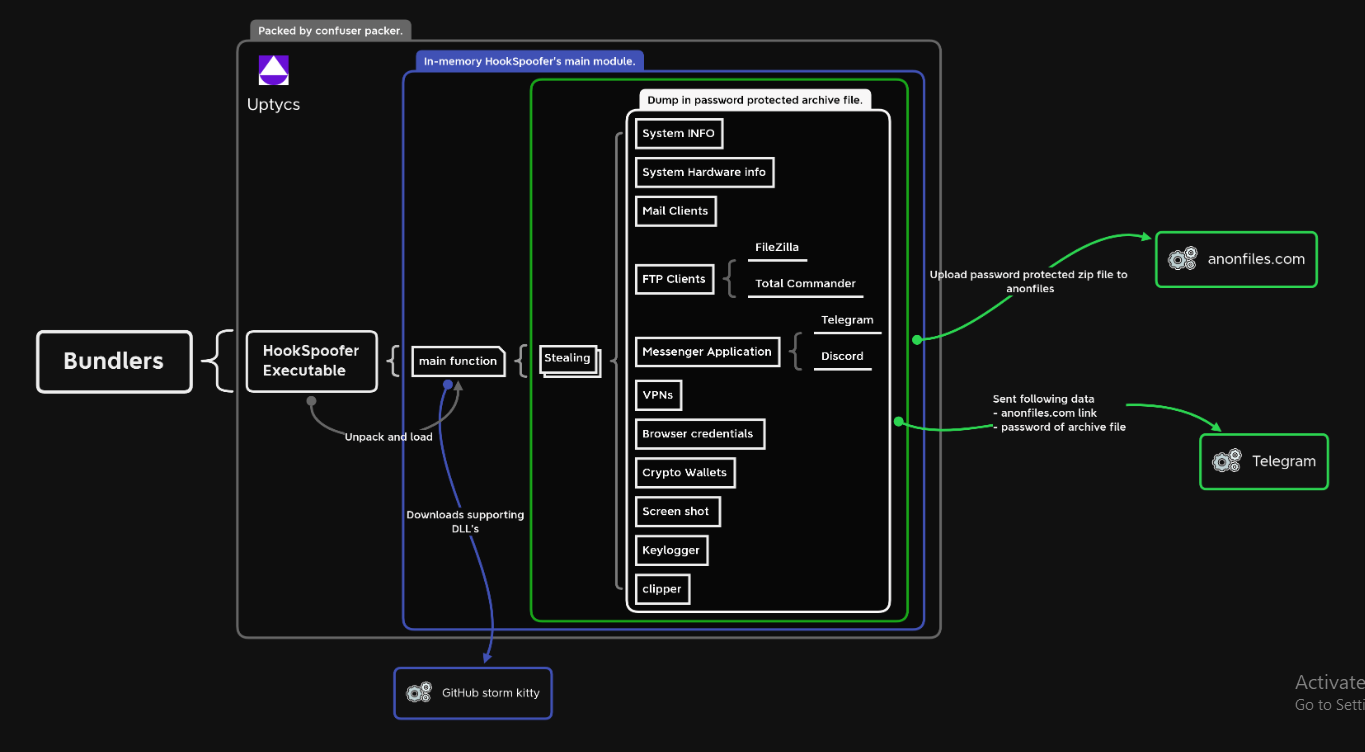
This software represents a new generation of information stealers, specifically engineered to extract valuable data from compromised systems with high efficiency. It primarily targets stored credentials, financial information, cryptocurrency wallets, and other sensitive data that can be monetized on underground markets. Typically distributed through phishing campaigns, malicious advertisements, or bundled with pirated software, this stealer is frequently used in credential-stuffing attacks, banking fraud, and as a precursor to ransomware deployments. Its modular design allows for easy customization, enabling attackers to tailor its functionality for specific campaigns.

Key Features
| Feature | Description |
| Credential Harvesting | Extracts saved logins from browsers and password managers. |
| Cryptocurrency Theft | Targets wallet files and clipboard contents for crypto addresses. |
| Cookie Hijacking | Steals session cookies to bypass authentication. |
| Form Grabbing | Captures form submissions in real-time. |
| System Reconnaissance | Gathers detailed system information for targeted attacks. |
| Anti-Analysis | Detects and evades sandboxes and virtual machines. |
| Persistence | Maintains long-term access through registry modifications. |
| Data Exfiltration | Compresses and encrypts stolen data before transmission. |
How StormKitty Stealer 2025 Works
Infection Vectors
The malware employs multiple distribution methods:
- Phishing Campaigns: Malicious emails with weaponized attachments or links
- Drive-by Downloads: Compromised websites delivering exploit kits
- Software Bundling: Distributed with cracked applications or fake installers
- Social Engineering: Disguised as legitimate software updates or documents
Execution and Evasion
Upon execution, the malware initiates several protective measures:
- Environment Checks: Scans for analysis tools, virtual machines, or security products
- Process Hollowing: Injects its payload into legitimate system processes
- Code Obfuscation: Uses polymorphic techniques to avoid signature detection
- Delayed Activation: Waits for user activity before beginning data collection
Data Collection Process
The stealer performs a comprehensive system scanning for:
- Browser Data: Extracts saved passwords, autofill information, and cookies
- Financial Information: Targets banking credentials and credit card details
- Cryptocurrency Assets: Scans for wallet files and monitors the clipboard for crypto transactions
- System Information: Collects hardware details, network configurations, and installed software
Data Processing and Exfiltration
Collected data undergoes several processing steps:
- Data Sorting: Organizes information by type and value
- Compression: Uses efficient algorithms to reduce size
- Encryption: Applies strong encryption before transmission
- C2 Communication: Connects to multiple fallback servers using HTTPS or custom protocols
Persistence Mechanisms
To maintain presence on infected systems:
- Creates scheduled tasks for periodic execution
- Modifies registry run keys
- Drops secondary payloads in system directories
- Uses fileless techniques when possible


