UBoat HTTP Botnet 2025
Botnets remain one of the most dangerous tools in a cybercriminal’s arsenal, enabling large-scale attacks such as Distributed Denial-of-Service (DDoS), data theft, and malware distribution. The UBoat HTTP Botnet 2025 represents a modern evolution of these threats, leveraging HTTP-based communication to blend in with legitimate web traffic and evade traditional security measures. Unlike older botnets that relied on easily detectable IRC or custom protocols, this new generation uses encrypted web requests, making it harder to detect and block. Its modular design allows attackers to deploy multiple malicious functions, from spam campaigns to ransomware distribution, making it a versatile weapon in cyber warfare.
Download Link 1
Download Link 2
Download Link 3
Download Link 4
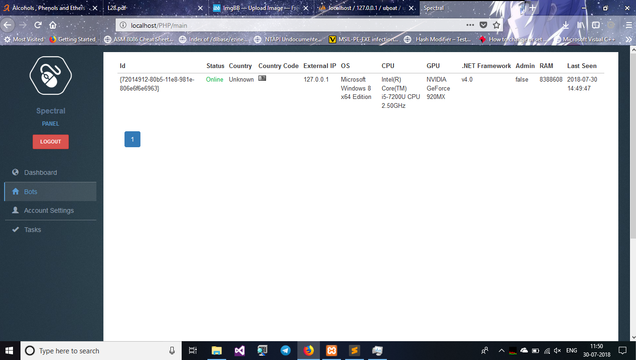
This software is a sophisticated botnet builder that creates and manages a network of infected machines (bots) controlled via HTTP/HTTPS protocols. Attackers use it to recruit compromised devices into a centralized command-and-control (C2) infrastructure, enabling remote execution of malicious activities. The botnet is typically spread through phishing emails, exploit kits, or malicious downloads, targeting both individual users and enterprise systems. Once installed, it operates silently, awaiting instructions from the attacker while maintaining persistence and evading detection.

Key Features
| Feature | Description |
| HTTP/HTTPS C2 Communication | Uses standard web protocols to blend in with normal traffic, avoiding detection. |
| Modular Payload System | Supports plugins for DDoS, ransomware, keyloggers, and more. |
| Process Injection | Injects malicious code into legitimate processes to evade task manager detection. |
| Persistence Mechanisms | Maintains access via registry edits, scheduled tasks, or service installation. |
| Anti-Analysis | Detects virtual machines, debuggers, and sandboxes to hinder reverse engineering. |
| Geographic Targeting | Can restrict attacks to specific regions to avoid early detection. |
| Encrypted Configuration | Obfuscates bot settings to prevent security tools from analyzing behavior. |
How UBoat HTTP Botnet 2025 Works
The botnet operates in stages, from initial infection to full command execution:
1. Infection & Initial Compromise
- The botnet spreads through:
- Phishing Campaigns: Malicious email attachments or links.
- Exploit Kits: Targeting browser or software vulnerabilities.
- Malware Bundling: Hidden in pirated software or fake updates.
- Once executed, the payload checks for security tools, virtual environments, or debugging before proceeding.
2. Establishing Persistence
- The malware ensures long-term access by:
- Adding itself to startup via registry keys (HKCU\…\Run).
- Creating scheduled tasks to reactivate periodically.
- Installing itself as a disguised Windows service.
3. C2 Communication & Bot Enrollment
- The infected machine contacts the C2 server via HTTP/HTTPS, mimicking legitimate web traffic.
- The server responds with encrypted commands, which may include:
- Downloading additional malware (e.g., ransomware, spyware).
- Updating the bot’s configuration.
- Activating attack modules (DDoS, spam, etc.).
4. Attack Execution
Depending on the attacker’s goals, the botnet can perform various malicious activities:
- DDoS Attacks: Floods target servers with HTTP requests, rendering them inaccessible.
- Data Exfiltration: Steals credentials, documents, or cryptocurrency wallets.
- Ransomware Deployment: Encrypts files and demands payment.
- Proxy Relaying: Uses infected machines to route malicious traffic anonymously.
5. Evasion & Maintenance
- The botnet continuously updates itself to avoid signature-based detection.
- It may switch C2 servers dynamically using domain generation algorithms (DGAs).
- Traffic is encrypted, and commands are obfuscated to bypass network monitoring.


