Ultimate Cracking And Hacking Pack 2024
In the evolving landscape of cybersecurity threats, malicious toolkits have increasingly become major enablers of modern cyberattacks. Among these, Ultimate Cracking packs stand out, often bundling a variety of exploits, payloads, and utilities specifically designed to compromise systems, steal data, or deliver malware.
For instance, one widely circulated toolkit is well-known for its versatility in facilitating unauthorized access, credential theft, and remote system control. Thanks to its modular design, attackers can tailor their approach based on the target’s vulnerabilities. As a result, this toolkit presents a persistent and adaptive threat across both individual and organizational environments.
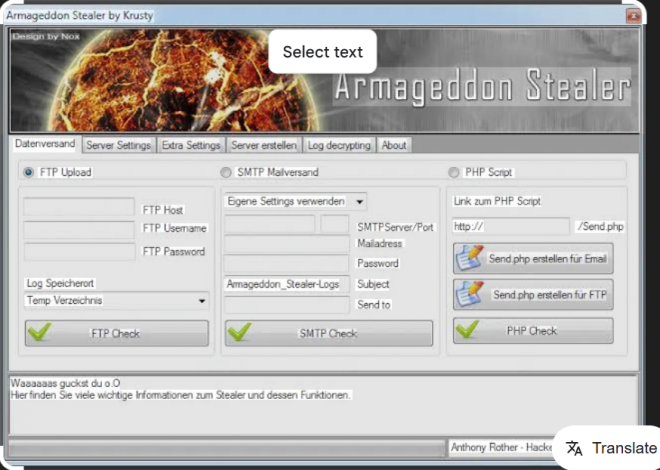
This Ultimate Cracking suite is a comprehensive collection of hacking tools that merges automated exploits, password-cracking utilities, and covert payload delivery mechanisms into a single package. Typically, threat actors use it to breach systems, escalate privileges, exfiltrate sensitive data, or even deploy ransomware.
Although some components of the toolkit may have legitimate applications in ethical hacking and penetration testing, in practice, it is predominantly used for malicious purposes. Due to its ease of use and high effectiveness against poorly secured systems, it remains a favored choice among cybercriminals.
Download Link 1
Download Link 2
Download Link 3
Download Link 4
Key Features of Ultimate Cracking
| Feature | Description |
| Automated Exploits | Pre-configured exploits for known vulnerabilities in OSes, apps, and networks. |
| Credential Cracking | Supports brute-force, dictionary, and rainbow table attacks against passwords. |
| Payload Generator | Creates custom malicious payloads, such as reverse shells and keyloggers. |
| Anti-Detection Bypass | Techniques to evade AV and EDR solutions (e.g., obfuscation, process injection). |
| Remote Access Toolkit | Provides persistent backdoor access to compromised systems. |
| Network Sniffing | Captures and analyzes network traffic for sensitive data. |
How the Ultimate Cracking Works
Techniques and Functionality
The Ultimate Cracking toolkit operates through a powerful combination of automated scanning, exploitation, and post-exploitation activities. To better understand its capabilities, here’s a step-by-step breakdown of how it works:
Reconnaissance and Scanning
The process begins with reconnaissance, where the software identifies potential targets by scanning IP ranges or domains. Specifically, it looks for open ports, running services, and exploitable vulnerabilities.
In addition, it references integrated vulnerability databases to match its findings with known exploits—such as unpatched CVEs. This step lays the groundwork for effective exploitation.
Exploitation of Ultimate Cracking
Once a vulnerability is detected, the toolkit automatically deploys the most suitable exploit to gain initial access to the system.
Commonly, it relies on techniques such as buffer overflow attacks, SQL injections, or exploiting misconfigured services. These attacks are tailored to the discovered weaknesses, making the breach more effective.
Payload Delivery
Following successful exploitation, the attacker selects and delivers a malicious payload to the target machine.
Typically, payloads may include malware, remote access tools, or keyloggers. Moreover, these are often obfuscated or encrypted to bypass detection by antivirus software and other security tools.
Privilege Escalation and Persistence
After the initial compromise, the toolkit attempts to elevate its privileges using local escalation exploits, allowing it to gain admin or root access.
Furthermore, it establishes persistence on the target system. This is achieved through methods like registry edits, scheduled tasks, or service hijacking, ensuring the attacker maintains long-term control.
Exfiltration or Remote Control
Finally, once full access is secured, data exfiltration begins. Depending on the attacker’s goals, sensitive information is extracted using covert channels.
Alternatively, the attacker may opt to assume ongoing remote control of the system via embedded backdoors, effectively turning the compromised device into a controllable asset.