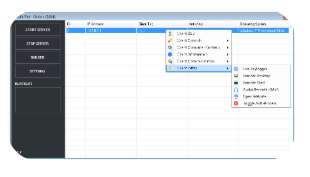
VanillaRat 1.7
VanillaRAT 1.7 has emerged as a sophisticated Remote Access Trojan (RAT) with enhanced capabilities for stealthy system infiltration and persistent control. This latest version demonstrates significant improvements in evasion techniques, data exfiltration methods, and plugin-based functionality. While cybersecurity professionals study it to strengthen defensive measures, unauthorized deployment remains illegal and poses severe risks to personal and organizational security.
Download Link 1
Download Link 2
Download Link 3
Download Link 4
What is VanillaRAT 1.7?
VanillaRAT is a Windows-based remote administration tool that enables complete system control through encrypted communication channels. Version 1.7 introduces:
- Refined anti-analysis capabilities
- Expanded plugin architecture
- Improved persistence mechanisms
- Enhanced credential harvesting
Security researchers analyze this RAT to:
- Develop detection signatures
- Improve endpoint protection
- Train incident response teams
- Enhance threat intelligence
Detailed Features of VanillaRAT 1.7
| Feature Category | Technical Capabilities | Implementation Details | Stealth Level |
|---|---|---|---|
| Remote Control | Full system access | Desktop streaming, file management, registry editing | High |
| Persistence | Multiple installation methods | Registry modifications, scheduled tasks, DLL hijacking | Extreme |
| Data Theft | Comprehensive harvesting | Keylogging, clipboard monitoring, password extraction | High |
| Network Communication | Encrypted C2 channels | AES-256 encryption with domain generation algorithms | Extreme |
| Evasion Techniques | Advanced anti-detection | VM/sandbox checks, security tool detection | Extreme |
| Plugin System | Modular payload delivery | Supports crypto-mining, ransomware, spyware add-ons | High |
| Update Mechanism | Secure payload updates | Encrypted differential updates from C2 server | High |
Why Research VanillaRAT 1.7? (Ethical Applications)
- Threat Intelligence: Understanding evolving RAT capabilities
- Defensive Development: Creating detection rules for EDR solutions
- Red Team Exercises: Testing organizational security postures
- Malware Analysis: Reverse-engineering new techniques
- Security Training: Educating cybersecurity professionals


