VENOM RAT 2.8 FINAL HRDP LOCKER HVNC RAT
Cyber threats continue to evolve, with remote access trojans (RATs) playing a significant role in modern cyberattacks. These malicious tools provide attackers with unauthorized control over compromised systems, enabling data theft, surveillance, and further network infiltration. Among these threats, advanced RATS stand out due to their stealth, persistence, and ability to bypass security measures. VENOM RAT 2.8 is often distributed through phishing campaigns, exploit kits, or disguised as legitimate software, making them a persistent challenge for cybersecurity professionals.
Download Link 1
Download Link 2
Download Link 3
Download Link 4
This type of software is a sophisticated RAT designed to provide attackers with full remote control over infected systems. It operates covertly, allowing threat actors to execute commands, steal sensitive data, and deploy additional malware. Typically, this software attacks businesses, individuals, or critical infrastructure, where financial gain or espionage is the primary motive. Its modular structure enables customization, making it adaptable for various malicious purposes.

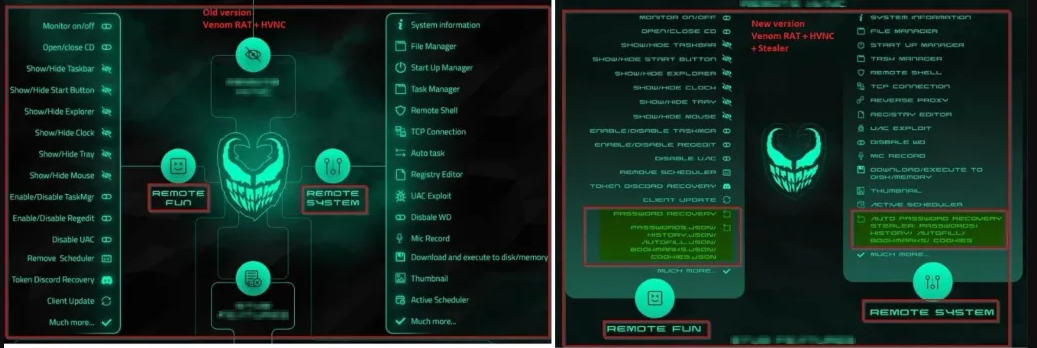
Key Features
| Feature | Description |
| Remote Control | Allows attackers to execute commands, manipulate files, and control the system. |
| Persistence | Ensures the malware remains active after reboots via registry or task scheduling. |
| Data Exfiltration | Steals credentials, documents, and other sensitive data from the victim. |
| Keylogging | Logs keystrokes to capture passwords and other typed information. |
| Screen Capture | Takes screenshots to monitor user activity. |
| HVNC (Hidden VNC) | Operates in a hidden desktop environment to avoid detection. |
| Anti-Detection | Uses obfuscation, encryption, and process injection to evade security tools. |
| Payload Delivery | Can download and execute additional malware from a C2 server. |
How VENOM RAT 2.8 Works
Infection and Execution
The malware typically infiltrates a system through social engineering (e.g., malicious email attachments, fake software installers) or exploits. Once executed, it establishes persistence by modifying system registry keys or creating scheduled tasks. Some variants also use process hollowing—a technique where a legitimate process (like explorer.exe) is hijacked to run malicious code, making detection harder.
Communication with C2
After installation, the malware connects to a command-and-control (C2) server, often using encrypted protocols like HTTPS or DNS tunneling to avoid network monitoring. The C2 server sends instructions, which may include:
- Downloading and executing additional payloads.
- Activating keylogging or screen capture modules.
- Updating the malware to evade detection.
Stealth and Evasion Techniques
To avoid detection, the malware employs several techniques:
- HVNC (Hidden Virtual Network Computing): Creates a hidden desktop session, allowing attackers to interact with the system without the user noticing.
- Code Injection: Injects malicious code into trusted processes to blend in with legitimate activity.
Encryption: Encrypts C2 communications and stored data to hinder analysis.


