Verci Spy System RAT Cracked 2024
Verci Spy System RAT Cracked 2024 has emerged as a significant threat in the cybercrime landscape, representing a cracked version of a commercial surveillance tool now weaponized for malicious purposes. This sophisticated remote access trojan has been observed in targeted attacks against businesses, government agencies, and high-net-worth individuals, demonstrating alarming capabilities in stealth and persistence. Security researchers have documented its use in corporate espionage, financial fraud, and large-scale data theft operations, with attackers leveraging its professional-grade features to bypass modern security measures. The 2024 cracked version has become particularly dangerous due to its expanded accessibility in underground forums, enabling even low-skilled threat actors to conduct advanced surveillance operations.
Download Link 1
Download Link 2
Download Link 3
Download Link 4

What is the Verci Spy System RAT
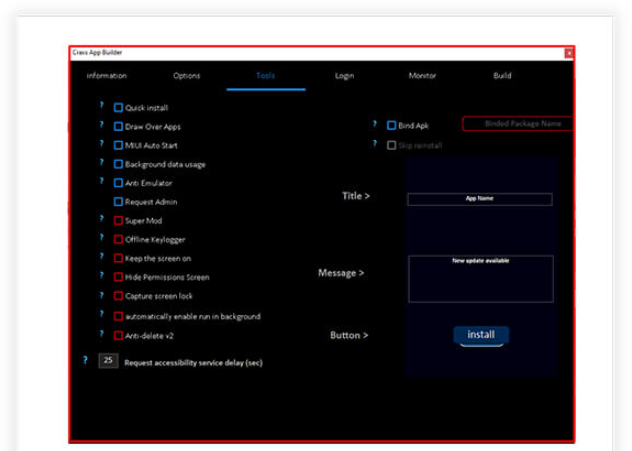
This software is a full-featured remote administration tool repurposed for cybercriminal activities, offering attackers complete control over compromised systems. The cracked version maintains all the dangerous functionality of the original commercial product while being distributed freely in hacker communities. Cybercriminals typically deploy it to:
- Conduct covert surveillance through live screen viewing and remote control.
- Steal sensitive data, including documents, credentials, and authentication tokens.
- Maintain long-term persistence in compromised networks.
- Deploy secondary payloads such as ransomware or infostealers.
- Bypass security products using advanced evasion techniques.
Key Features
| Feature | Description |
| Remote Desktop Control | Provides real-time screen sharing with mouse/keyboard input capabilities |
| File System Access | Enables browsing, downloading, and modifying files on infected systems |
| Keylogging | Records all keyboard input to capture passwords and sensitive communications |
| Audio/Video Capture | Secretly activates and records from connected microphones and webcams |
| Process Management | Allows viewing and terminating running processes |
| Persistence Engine | Maintains access through registry modifications and hidden startup entries |
| Encrypted C2 | Uses secure communication channels to evade network monitoring |
| Plugin System | Supports modular extensions for additional malicious functionality |
How the Verci Spy System RAT works
1. Initial Infection Vectors
The malware spreads through multiple channels:
- Spear phishing emails with malicious attachments (documents, PDFs).
- Fake software cracks and pirated applications.
- Compromised websites host drive-by downloads.
- Malicious advertisements redirect to exploit kits.
Upon execution, it:
- Drops multiple components in system directories.
- Modifies registry keys for persistence (e.g., HKCU\Software\Microsoft\Windows\CurrentVersion\Run).
- Disables security features and competing malware.
- Establishes encrypted connection to C2 servers.
2. Command and Control Infrastructure
The RAT employs sophisticated C2 mechanisms:
- Domain generation algorithms (DGA) for resilient communication.
- HTTPS tunneling to blend with legitimate web traffic.
- Fast-flux DNS to evade takedowns.
- Multiple fallback servers for redundancy.
3. Surveillance and Data Theft Capabilities
Attackers can remotely:
- View and control the desktop environment in real-time.
- Log keystrokes to harvest credentials and sensitive communications.
- Exfiltrate files through compressed, encrypted transfers.
- Execute PowerShell scripts for advanced attacks.
- Capture audio/video from connected devices.
- Monitor clipboard contents for sensitive data.
4. Evasion and Anti-Forensics Techniques
The malware incorporates multiple stealth features:
- Process hollowing (injecting into legitimate Windows processes).
- Memory-only operation to avoid disk detection.
- Sandbox detection to prevent analysis.
- Regular binary updates from C2 servers.
- User-mode rootkit functionality to hide artifacts.


