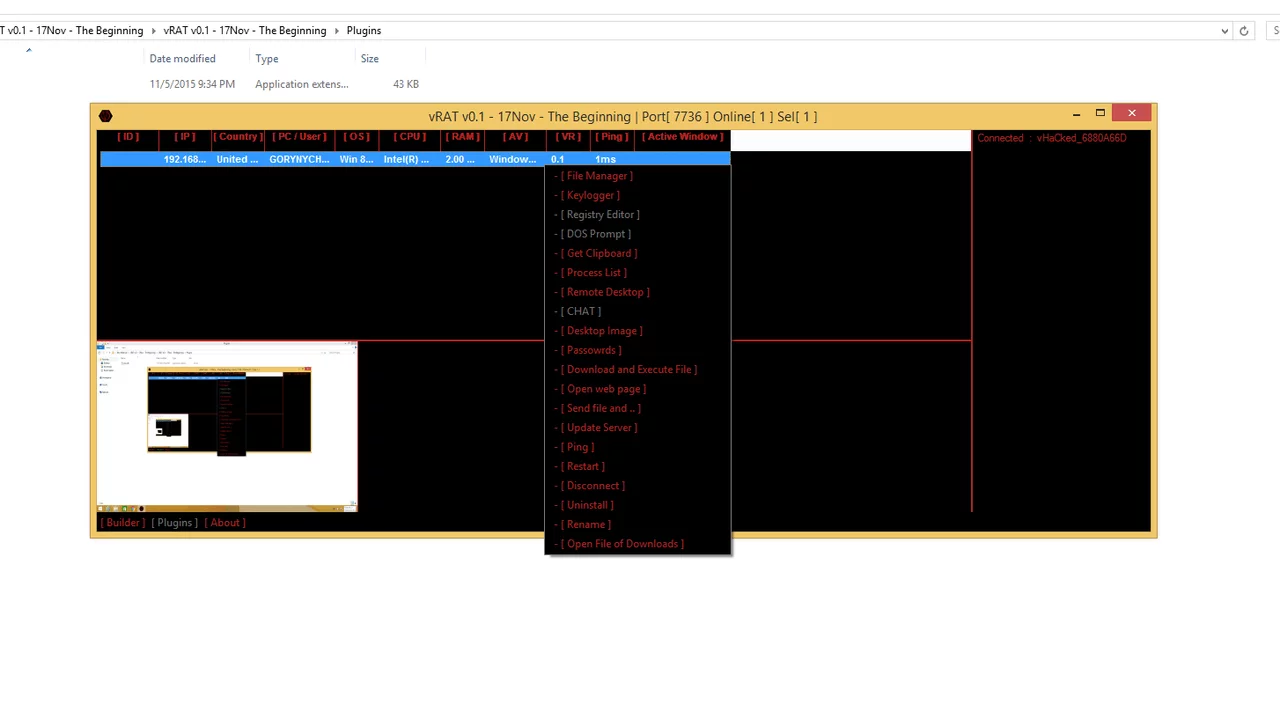
vRAT v0.1
vRAT v0.1 (Virtual Remote Access Trojan) is a newly emerging remote administration tool that has gained attention in cybersecurity circles. While it claims to be a legitimate remote management utility, its capabilities make it a preferred choice for hackers seeking unauthorized access to systems. With its lightweight design and modular approach, vRAT v0.1 poses a significant threat to individuals and organizations with weak security measures.

What is vRAT v0.1?
vRAT v0.1 is a Windows-based malware designed to provide remote control over infected machines. Unlike traditional RATs, it focuses on low detection rates, fast execution, and customizable attack modules. It operates silently in the background, allowing attackers to steal data, manipulate files, and even deploy additional payloads.
Detailed Features of vRAT v0.1
The table below highlights its key functionalities:
| Feature Category | Description |
|---|---|
| Remote Desktop Control | Full access to victim’s screen, mouse, and keyboard inputs. |
| Keylogging | Logs keystrokes to capture passwords, messages, and sensitive data. |
| File System Access | Browse, upload, download, modify, or delete files on the infected system. |
| Process Manipulation | Start, stop, or inject code into running processes. |
| Persistence Mechanism | Survives reboots via registry edits or task scheduler entries. |
| Anti-Detection | Uses obfuscation, junk code, and VM/sandbox evasion techniques. |
| Spread via USB/Email | Infects removable drives or spreads through phishing attachments. |
| Webcam & Mic Capture | Secretly activates recording devices for spying. |
| Clipboard Monitoring | Steals copied text, including passwords and cryptocurrency addresses. |
| Command & Control (C2) | Connects to a remote server for receiving attacker commands. |
Why Do Hackers Use vRAT v0.1?
- Lightweight & Fast: Low system footprint makes it hard to detect.
- Customizable Attacks: Supports plugins for ransomware, cryptojacking, or spyware.
- Stealthy Operations: Avoids triggering antivirus alerts.
- Data Harvesting: Collects credentials, financial info, and personal files.
- Botnet Potential: Can be used to create a network of infected devices.
Additional Risks & Protective Measures
- Victims may experience identity theft, financial fraud, or blackmail.
- Detection & Removal: Use behavior-based antivirus (e.g., CrowdStrike, SentinelOne) and network traffic monitoring.
- User Awareness: Avoid suspicious email attachments, disable autorun for USB drives, and keep software updated.
- Legal Consequences: Using or distributing vRAT v0.1 is illegal in most jurisdictions.


