VyprVPN Checker 2025
In the evolving landscape of cybersecurity, tools designed to test network vulnerabilities play a crucial role, both for defenders and attackers. Among these tools, VyprVPN Checker 2025 has gained attention for its dual-use potential. While they can help legitimate users verify their anonymity and connection security. Malicious actors have repurposed them to identify and exploit weaknesses in encrypted communications. In 2025, such tools have become increasingly sophisticated, enabling attackers to bypass security measures.
Download Link 1
Download Link 2
Download Link 3
Download Link 4
This software is primarily designed to analyze and validate VPN connections, checking for IP leaks, DNS vulnerabilities, and encryption integrity. Legitimate users, such as penetration testers and privacy-conscious individuals, utilize it to verify that their VPNs are functioning properly. However, threat actors misuse it to identify exposed systems, detect misconfigurations, and gather intelligence before launching targeted attacks. By probing VPN endpoints, the tool can reveal critical weaknesses that may later be exploited for unauthorized access or data interception.

Key Features of VyprVPN Checker 2025
| Feature | Description |
| IP Leak Detection | Identifies whether the real IP address is exposed despite VPN usage. |
| DNS Request Monitoring | Checks if DNS queries bypass the VPN tunnel, revealing potential vulnerabilities. |
| WebRTC Vulnerability Scan | Detects browser-based leaks that could expose user location or identity. |
| Encryption Strength Test | Assess the robustness of the VPN’s encryption protocols. |
| Geo-Spoofing Verification | Confirms whether the VPN successfully masks the user’s geographic location. |
| Logging & Reporting | Generates detailed logs of detected vulnerabilities for further analysis. |
How VyprVPN Checker 2025 Works
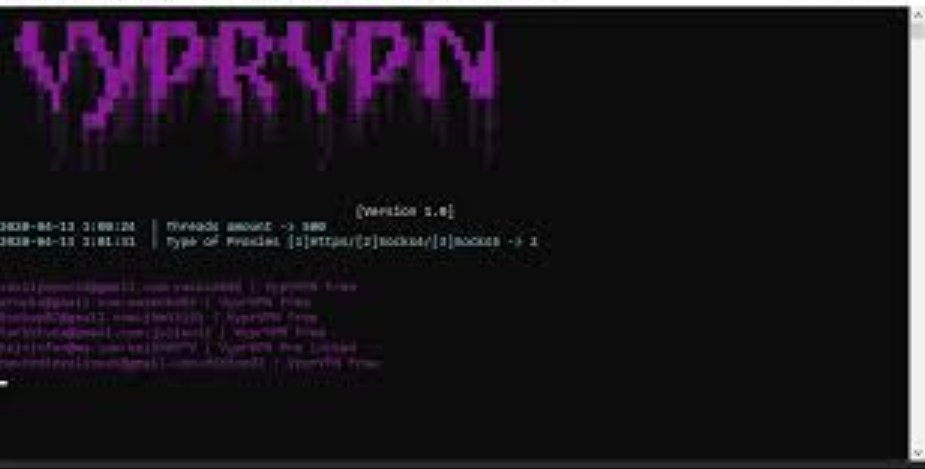
The software operates by simulating network traffic while a VPN is active, analyzing how data is routed and protected. Below is a breakdown of its core functionality:
- Connection Probing – The tool initiates connections to external servers, monitoring whether requests are routed through the VPN or if they leak outside the encrypted tunnel. It checks for discrepancies in IP addresses, DNS resolutions, and WebRTC disclosures.
- Traffic Analysis – By sending test packets, the software examines encryption protocols (e.g., OpenVPN, WireGuard) to detect weak configurations or outdated cipher suites that could be exploited.
- Payload Delivery (Malicious Use Case) – In adversarial scenarios, the tool can be weaponized to inject malicious payloads once a vulnerability is detected.
- Stealth Techniques – To avoid detection, the software may use fragmented requests or mimic legitimate VPN handshake patterns, making it harder for security systems to flag its activity.
By combining these techniques, the tool provides a comprehensive assessment of VPN security, either helping users strengthen their privacy or enabling attackers to exploit gaps in network defenses. Its effectiveness lies in its ability to automate vulnerability detection, making it a potent tool in both ethical and malicious cybersecurity operations.