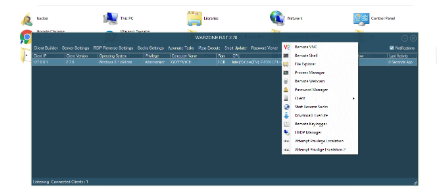
Warzone 2.70 Cracked
Warzone 2.70 Cracked refers to an unauthorized, modified version of the legitimate Warzone remote access trojan (RAT) software. This cracked variant circulates through underground hacking forums and poses significant cybersecurity risks. While some may seek it for penetration testing, its primary use is malicious, enabling unauthorized system access, data theft, and surveillance.
Download Link 1
Download Link 2
Download Link 3
Download Link 4
What Is Warzone 2.70 Cracked?
Warzone 2.70 Cracked is a pirated and altered version of the commercial Warzone RAT, stripped of licensing restrictions and often bundled with malware. Unlike the original tool (intended for IT administration), this cracked version is weaponized for cyberattacks, including credential theft, keylogging, and backdoor access. Security researchers may analyze it to understand threats, but its unlicensed use is illegal.
Detailed Features
- Remote System Control: Full access to victim devices, including file management and command execution.
- Keylogging: Records keystrokes to steal passwords, messages, and sensitive data.
- Webcam & Microphone Hijacking: Secretly captures audio/video feeds.
- Persistence Mechanisms: Installs itself via registry edits or scheduled tasks to survive reboots.
- Credential Harvesting: Extracts saved logins from browsers (Chrome, Firefox, Edge).
- Screen Capture: Takes screenshots to monitor user activity.
- Process Injection: Conceals itself within legitimate system processes.
- Network Propagation: Scans LAN/WAN for other vulnerable devices.
- Antivirus Evasion: Uses obfuscation and packing to bypass detection.
- Encrypted C2 Communication: Communicates with attacker servers via AES-256 or custom protocols.
- Discord Token Theft: Targets Discord authentication tokens for account takeover.
- Ransomware Module: Some variants deploy file-encrypting payloads.
Why Is It Used?
- Cybercriminals: Deploy it for espionage, financial theft, or botnet recruitment.
- Black Hat Hackers: Sell access to compromised systems on dark web markets.
- State-Sponsored Actors: Use it for targeted attacks against organizations.
- Security Researchers: Analyze samples to develop detection signatures (in controlled environments).
Ethical and Legal Implications
- Illegality: Distributing or using cracked RATs violates software licensing and cybersecurity laws (e.g., CFAA, GDPR).
- Risks to Users: Cracked versions often contain hidden malware (e.g., cryptominers, spyware).
- Mitigation: Use endpoint protection (EDR/XDR) to detect RAT behavior.
- Educate users about phishing (common delivery method for RATs).
- Disable unnecessary remote access protocols (RDP, VNC).
- Ethical Alternatives: Legitimate pentesting tools like Metasploit or Cobalt Strike (with proper licensing).


