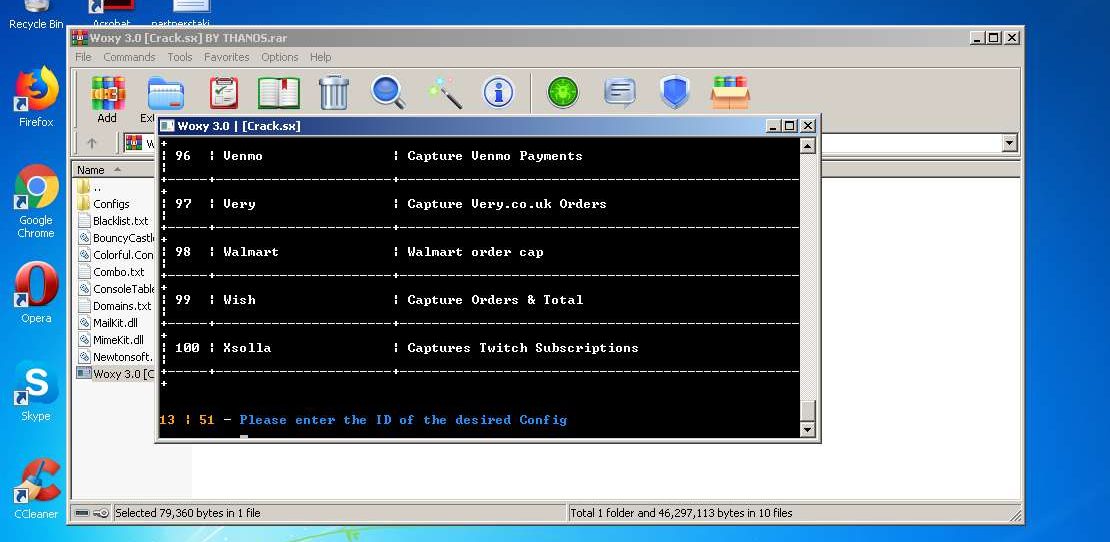
Woxy 3.0+166 Config updated 2023
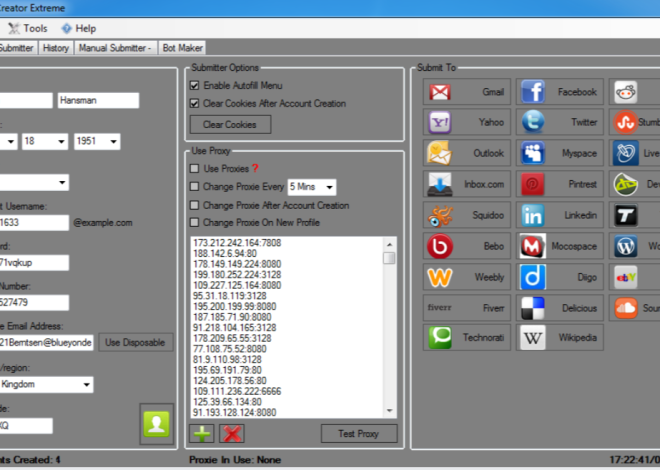
The cybersecurity landscape in 2023 has seen a surge in sophisticated attack tools that leverage legitimate software infrastructures for malicious purposes. Among these, advanced proxy-based utilities have emerged as particularly dangerous enablers of cybercrime, allowing attackers to mask their activities behind layers of seemingly legitimate traffic. Woxy 3.0+166 Config updated tools have become essential components in modern attack chains, facilitating everything from credential stuffing to large-scale web scraping operations while evading traditional security defenses. Their ability to mimic organic user behavior while operating at scale makes them particularly effective for bypassing rate limits and geographic restrictions.
Download Link 1
Download Link 2
Download Link 3
Download Link 4
This software represents a next-generation proxy management solution that malicious actors have repurposed to orchestrate complex cyberattacks. At its core, it functions as a high-performance proxy client with advanced traffic routing capabilities, but its modular architecture allows for extensive customization through configuration files. While originally designed for legitimate web automation tasks, its features have made it particularly valuable for coordinating distributed attacks, managing botnets, and conducting large-scale credential testing campaigns. The software’s frequent configuration updates ensure compatibility with the latest security measures implemented by target websites.

Key Features
| Feature | Description |
| Advanced Proxy Chaining | Supports multi-layer proxy routing with automatic failover |
| Traffic Obfuscation | Mimics human browsing patterns and device fingerprints |
| Configurable HTTP Stack | Allows deep customization of headers and TLS parameters |
| Session Persistence | Maintains stateful connections across IP rotations |
| Adaptive Rate Limiting | Dynamically adjusts request timing based on target responses |
| CAPTCHA Handling | Integrates with solving services and evasion techniques |
| Distributed Execution | Coordinates traffic across multiple endpoints for load balancing |
| Logging & Analytics | Provides detailed attack metrics and success rates |
How Woxy 3.0+166 Config updated 2023 Works
1. Infrastructure Setup
- The operator configures proxy lists (residential, datacenter, or mobile IPs)
- Loads specialized configuration files defining:
- Target website interaction flows
- Success/failure detection rules
- Traffic shaping parameters
- Data extraction patterns
2. Attack Orchestration
Traffic Generation:
- Creates thousands of concurrent connections through proxy networks
- Rotates user agents, device IDs, and browser fingerprints
- Maintains session consistency despite IP changes
Protocol-Level Manipulation:
- Customizes TLS handshakes to match regional browser characteristics
- Randomizes HTTP header order and casing
- Implements varying HTTP protocol versions
3. Evasion Techniques
- IP Rotation Strategies:
- Cyclic rotation based on time/request count
- Target-specific rotation schedules
- Adaptive rotation triggered by security challenges
- Behavioral Obfuscation:
- Mouse movement simulation
- Randomized scroll patterns
- Naturalistic request timing
4. Payload Delivery Mechanisms
Depending on configuration:
- Credential Stuffing:
- Tests breached credentials across multiple sites
- Bypasses security measures through session replay
- Web Scraping:
- Extracts sensitive data behind logins
- Circumvents anti-scraping protections
- Inventory Hoarding:
- Monitors and snaps up limited-availability items
- Automates fraudulent purchases
5. Post-Action Processing
- Parses successful responses for valuable data
- Stores session tokens for persistent access
- Generates detailed reports on attack efficacy
- Automatically updates configurations based on new defenses