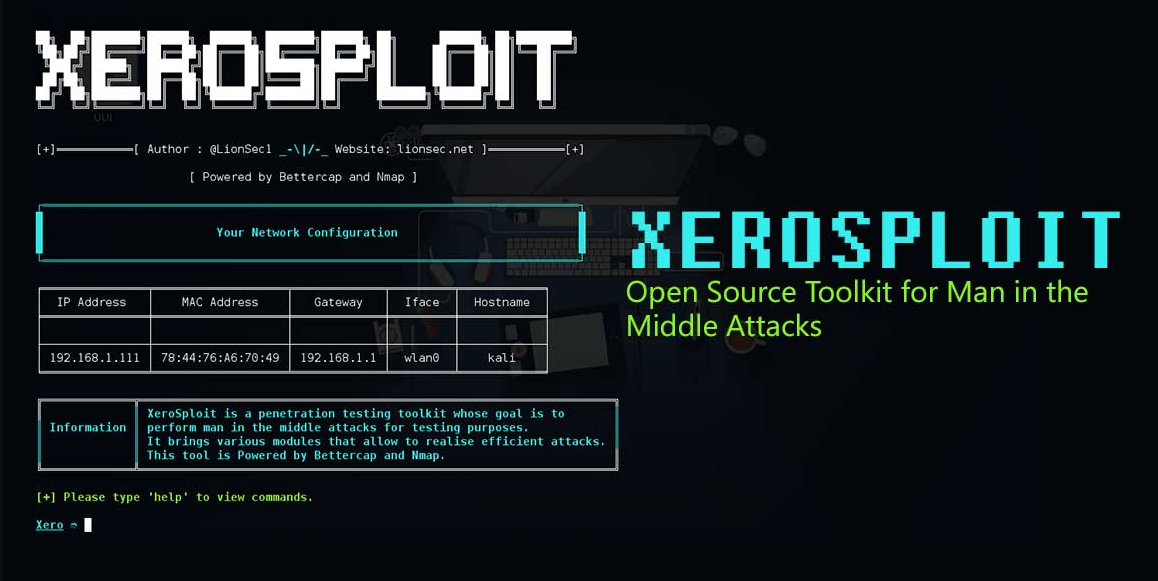
Xerosploit Toolkit 2025
Modern cyberattacks increasingly leverage sophisticated network penetration toolkits that automate man-in-the-middle (MITM) attacks and network exploitation. These frameworks have become particularly dangerous as they enable attackers to intercept, manipulate, and exploit network traffic with minimal technical expertise. When weaponised by malicious actors, Xerosploit Toolkit 2025 can facilitate credential theft, session hijacking, and malware distribution, while evading traditional network security measures. Their ability to operate on local networks makes them especially potent for corporate espionage, financial fraud, and advanced persistent threats.
Download Link 1
Download Link 2
Download Link 3
Download Link 4
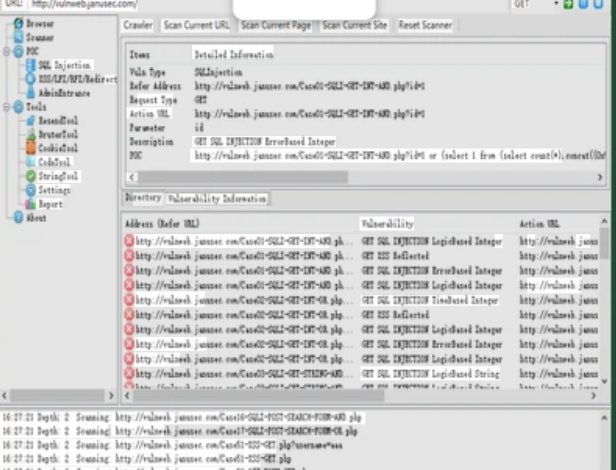
This software is an advanced network attak framework designed to perform comprehensive Man-in-the-Middle (MITM) attacks and exploit network vulnerabilities. It provides a suite of tools that allow attackers to intercept and manipulate network traffic, exploit connected devices, and deploy malicious payloads across local networks. While initially developed for ethical penetration testing, unauthorized versions have been adopted by cybercriminals for stealing sensitive data, distributing malware, and conducting reconnaissance. The toolkit is particularly effective against wireless networks and can be used to compromise IoT devices, workstations, and mobile devices connected to the same network segment.
Key Features of Xerosploit Toolkit 2025
| Feature | Description |
| Automated MITM Attacks | ARP/DHCP spoofing and DNS hijacking capabilities |
| Network Sniffing | Real-time traffic interception and analysis |
| Session Hijacking | Cookie stealing and TCP session takeover functionality |
| Payload Injection | Ability to inject malicious code into network streams |
| Vulnerability Scanner | Built-in detection of network device weaknesses |
| Traffic Manipulation | On-the-fly modification of HTTP/HTTPS content |
| Wireless Exploits | Specialized modules for attacking WiFi networks |
How Xerosploit Toolkit 2025 Works
The toolkit operates through a multi-stage process that automates network compromise:
- Network Reconnaissance
- Performs automated network mapping using ARP scanning
- Identifies active hosts, open ports, and running services
- Fingerprints operating systems and network devices
- Builds target profile for vulnerability assessment
- MITM Establishment
- Executes ARP cache poisoning to redirect traffic
- Implements DNS spoofing to manipulate domain resolution
- For HTTPS traffic, employs SSL stripping attacks
- Sets up transparent proxy for traffic interception
- Exploitation Phase
- Deploys various attack modules based on discovered vulnerabilities:
- Credential Harvesting: Captures login credentials from plaintext protocols
- Session Hijacking: Steals active web session cookies
- Code Injection: Injects malicious JavaScript into web pages
- Malware Delivery: Replaces downloads with compromised files
- Post-Compromise Actions
- Establishes persistent backdoors on compromised systems
- Performs lateral movement across the network
- Exfiltrates collected data through encrypted channels
- Maintains stealth by mimicking normal network patterns