Account Hitman BETA V1.33
Account Hitman BETA V1.33 is a sophisticated security assessment tool designed to test the vulnerability of online accounts against unauthorized access attempts. This tool simulates credential-based attacks to help cybersecurity professionals and system administrators identify weak authentication mechanisms. It is strictly intended for ethical hacking and penetration testing purposes with proper authorization.

What Is Account Hitman BETA?
Account Hitman BETA is a specialized brute-force and credential-stuffing tool that evaluates the strength of account security across various online platforms. Unlike malicious hacking tools, it serves as a legitimate security solution, enabling organizations to proactively strengthen their authentication systems by identifying exploitable weaknesses before malicious actors can take advantage of them.
Detailed Features
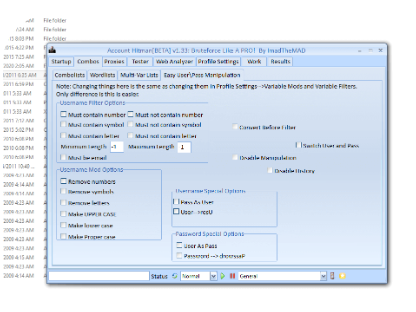
- Multi-Platform Support: Tests account security across websites, APIs, and mobile applications.
- Advanced Brute-Force Engine: Uses intelligent algorithms to optimize attack patterns.
- Credential Stuffing: Tests known username/password combinations from breach databases.
- Proxy & VPN Integration: Rotates IP addresses to bypass rate-limiting defenses.
- Custom Wordlist Support: Imports tailored password dictionaries for targeted testing.
- Session Management: Resumes interrupted attacks without data loss.
- Two-Factor Authentication (2FA) Testing: Attempts to bypass methods for SMS/email-based 2FA.
- CAPTCHA Bypass Techniques: Handles basic CAPTCHA challenges automatically.
- Request Throttling Control: Adjusts attack speed to mimic human behavior.
- Detailed Reporting: Generates comprehensive logs of successful breaches and vulnerabilities.
- User-Agent Randomization: Avoids detection by mimicking legitimate browser traffic.
- API Mode: Enables automated testing for developers securing backend systems.
Why Use Account Hitman BETA V1.33?
Account Hitman BETA V1.33 is essential for:
- Security Teams: Identifying weak passwords and flawed authentication systems.
- Developers: Stress-testing account security during application development.
- Compliance Auditors: Verifying adherence to cybersecurity best practices.
- Ethical Hackers: Conducting authorized penetration tests for clients.
Additional Information & Education
- Legal Compliance: Unauthorized use violates cybersecurity laws; always obtain explicit permission.
- Mitigation Strategies: Enforce strong password policies and mandatory 2FA.
- Implement account lockout mechanisms after repeated failed attempts.
- Monitor for unusual login patterns and credential-stuffing attacks.
- Responsible Disclosure: Report discovered vulnerabilities to the relevant organizations for patching.


