ANARCHY PANEL RAT 4.7 Cracked
In the evolving landscape of cyber threats, remote access trojans (RATs) continue to be a persistent tool for malicious actors. One such example, often referenced in underground forums, is a cracked version of a well-known Remote Access Tool (RAT) that has been repurposed for unauthorized access and control over compromised systems. ANARCHY PANEL RAT 4.7 tools are frequently deployed in targeted attacks, enabling threat actors to steal sensitive data, deploy additional malware, or maintain Persistence within networks. Their modular design and evasion capabilities make them particularly dangerous in modern cyberattacks, where stealth and adaptability are critical.
Download Link 1
Download Link 2
Download Link 3
Download Link 4
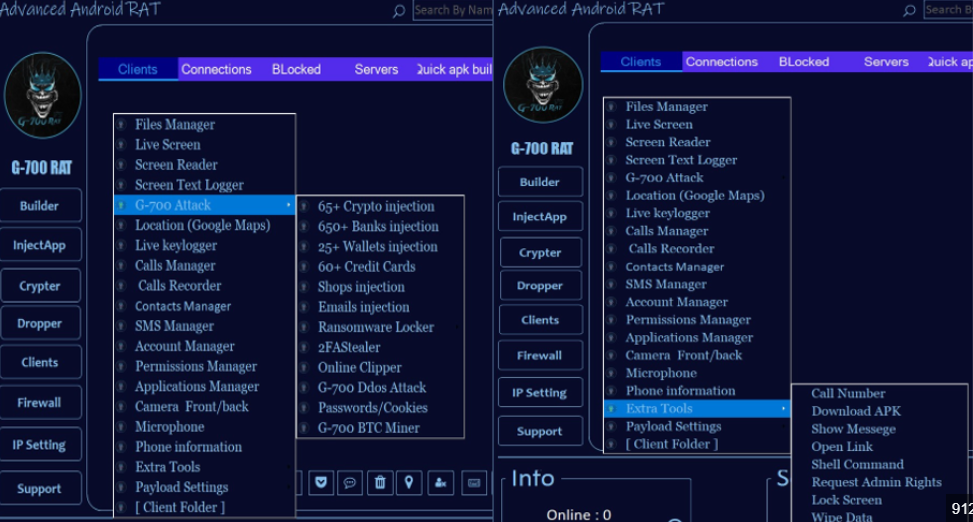
This software is a remote administration tool that, when misused, can function as a remote access tool (RAT). Legitimate versions are used for remote IT support and system management, but cracked variants remove licensing restrictions, allowing malicious use. Attackers leverage it to gain complete control over a victim’s machine, including file manipulation, screen capture, keylogging, and even webcam access. Its popularity among cybercriminals stems from its user-friendly interface and robust feature set, which can be customized for specific attack scenarios.
Key Features of ANARCHY PANEL RAT 4.7
| Feature | Description |
| Remote Desktop Control | Allows real-time interaction with the victim’s desktop. |
| Keylogging | Logs keystrokes to capture credentials and other sensitive input. |
| File Transfer | Uploads and downloads files to and from the compromised system. |
| Persistence Mechanisms | Ensures the malware remains active after reboots, such as through registry edits. |
| Webcam & Microphone Access | Enables unauthorized streaming or recording from connected devices. |
| Process Manipulation | Terminates or spawns processes to evade detection or turn off security tools. |
| Evasion Techniques | Uses obfuscation, encryption, or anti-sandbox methods to bypass defenses. |
How ANARCHY PANEL RAT 4.7 Works
Infection and Execution
The malware typically spreads through phishing emails, malicious downloads, or exploit kits. Once executed, it installs itself silently, often dropping files in hidden directories or masquerading as a legitimate process. Persistence is achieved by modifying registry keys or creating scheduled tasks, ensuring the malware runs every time the system boots.
Communication and Command Control (C2)
After installation, the malware establishes a connection to a command-and-control (C2) server, typically via HTTP, HTTPS, or custom protocols, to blend in with regular traffic. The C2 server sends encrypted commands, which the malware decodes and executes on the victim’s machine. This two-way communication enables attackers to adjust their tactics in response to the compromised environment dynamically.
Payload Delivery and Functionality of ANARCHY PANEL RAT 4.7
The malware operates modularly, allowing attackers to deploy additional payloads as needed. For example:
- Data Exfiltration: Searches for and uploads sensitive files (e.g., documents, credentials) to the Command and Control (C2) server.
- Lateral Movement: Uses harvested credentials or exploits to spread across a network.
- Evasion: Terminates security processes, turns off firewalls, or employs code injection to avoid detection.
Anti-Analysis Techniques
To hinder reverse engineering, the malware may use:
- Obfuscation: Encrypts strings or code to obscure its purpose.
- Sandbox Detection: Checks for virtualized environments and halts execution if detected.
- Delayed Execution: Waits before activating to evade automated analysis systems.
By combining these techniques, the malware maintains stealth while providing attackers with extensive control over compromised systems. Its adaptability makes it a significant threat in both targeted attacks and broad cybercrime campaigns.


