AsyncRAT v0.5.6
In the rapidly evolving cybersecurity landscape, AsyncRAT v0.5.6 has become increasingly sophisticated, posing significant threats to individuals and organizations alike. One particularly dangerous variant, known for its asynchronous communication capabilities, has gained prominence among cybercriminals for its stealth and versatility. This RAT enables attackers to maintain persistent access to compromised systems while evading traditional detection methods. Its ability to blend malicious activities with normal network traffic makes it especially effective for data theft, surveillance, and secondary payload deployment, cementing its role as a favored tool in modern cyberattacks.
Download Link 1
Download Link 2
Download Link 3
Download Link 4

What is AsyncRAT v0.5.6?
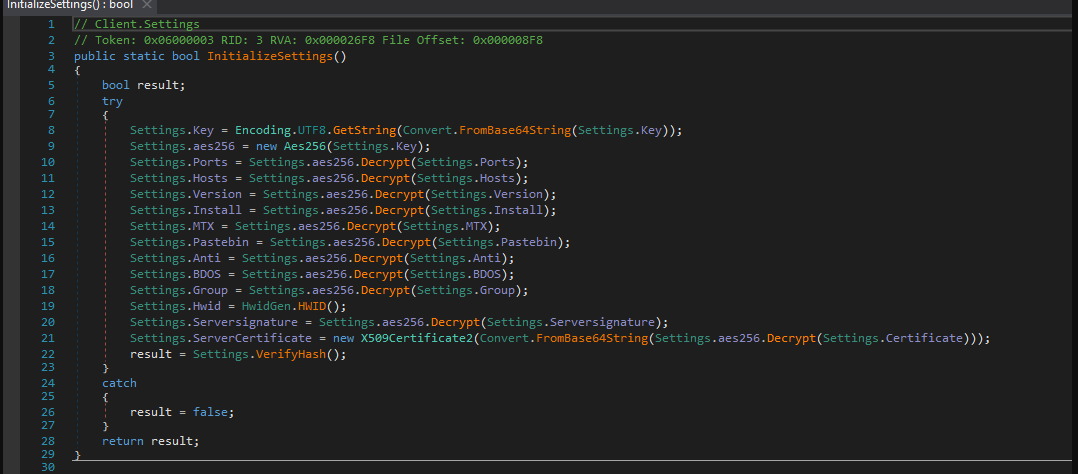
This RAT is a NET-based remote administration tool that has been repurposed for malicious activities. Unlike traditional RATs, it utilizes asynchronous communication with its command-and-control (C2) servers, making detection more challenging. The malware is primarily distributed through phishing campaigns, malicious document macros, and software cracks. Once installed, it provides attackers with comprehensive control over infected systems, enabling activities ranging from credential theft to cryptocurrency mining. Its modular design allows for easy customization, making it adaptable for various attack scenarios.
Key Features of AsyncRAT v0.5.6
| Feature | Description |
| Asynchronous C2 Communication | Uses non-blocking calls to blend with legitimate traffic |
| Process Injection | Executes within legitimate processes like explorer.exe |
| Credential Harvesting | Extracts passwords from browsers and email clients |
| Keylogging | Captures all keyboard input |
| Screen Capture | Takes periodic screenshots |
| File Management | Full access to the victim’s file system |
| Persistence Mechanisms | Registry modifications and scheduled tasks |
| Anti-Analysis Techniques | Detects sandboxes and virtual machines |
| Plugin Support | Allows additional functionality through modules |
How AsyncRAT v0.5.6Works
Delivery and Infection
- Phishing emails with malicious Office documents containing macros.
- Compressed executables disguised as legitimate software.
- Exploit kits target unpatched vulnerabilities.
Initial Execution
- Decrypts its configuration data.
- Injects into a legitimate Windows process.
Persistence Establishment
- Creates registry run keys.
- Sets up scheduled tasks.
- It may install itself as a Windows service.
C2 Communication
- HTTP/S protocols with encrypted traffic.
- Domain generation algorithms (DGAs) for resilience.
- Asynchronous callbacks to avoid detection.
Malicious Functionality
- Remotely execute commands via PowerShell.
- Deploy additional payloads.
- Steal sensitive documents and credentials.
- Activate the victim’s webcam and microphone.
- Mine cryptocurrency using the victim’s resources.
Evasion Techniques
- String obfuscation and anti-debugging tricks.
- Process hollowing to hide in legitimate processes.
- Traffic encryption using AES or similar algorithms.
- Delayed execution to bypass sandbox analysis.


