Burp Suite Professional 2022.2.2 Activated
In modern cybersecurity, tools designed for penetration testing and vulnerability assessment are often repurposed by malicious actors to exploit weaknesses in networks and applications. One such tool, Burp Suite Professional 2022.2.2, activated, has become a double-edged sword. While security professionals widely use it to identify and fix vulnerabilities, attackers leverage its capabilities to map attack surfaces, intercept traffic, and deliver payloads. Its robust feature set makes it a common choice for both ethical hackers and adversaries, highlighting the importance of understanding its functionality to defend against potential misuse.
Download Link 1
Download Link 2
Download Link 3
Download Link 4
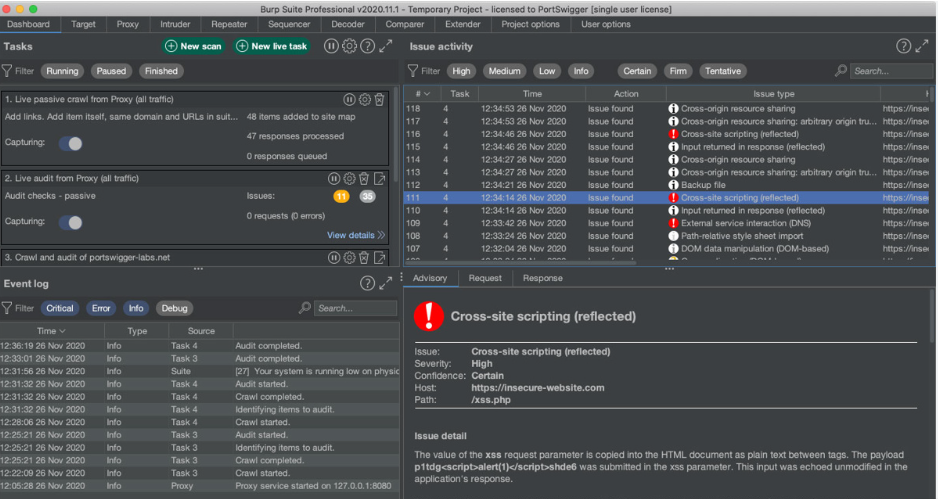
This software is a comprehensive platform for web security testing, primarily used to analyze web applications for vulnerabilities. It functions as an intercepting proxy, allowing users to inspect and modify HTTP/S requests and responses between a browser and a target server. Typical uses include vulnerability scanning, session manipulation, API testing, and automated attacks like SQL injection or cross-site scripting (XSS). Security teams rely on it to simulate real-world attacks and harden defences, but its misuse can lead to unauthorised access or data breaches.
Key Features of Burp Suite Professional
How the Software Works
Intercepting Proxy
The software acts as a middleman between the browser and the target server. By configuring the browser to route traffic through the tool, it captures requests and responses, enabling manual or automated modifications. This is useful for testing input validation, session handling, or access controls.
Vulnerability Scanning
The built-in scanner sends crafted requests to identify weaknesses, such as insecure headers, misconfigurations, or injection flaws. It analyses responses for patterns indicating vulnerabilities (e.g., data analysis errors for SQLi).
Payload Delivery (Intruder)
For attacks such as brute force or SQL injection, the Intruder tool replaces parameters in requests with payloads from predefined or custom lists. It systematically tests inputs and evaluates responses for successful exploitation.
Session Manipulation
The tool can hijack or manipulate sessions by stealing cookies or tokens. Features like the “Repeater” allow replaying requests with modified session data to escalate privileges or bypass authentication.
Extensibility (BApps)
Plugins extend functionality, such as decoding data, automating exploits, or integrating with other tools. This modularity makes it adaptable for advanced attack scenarios.
Payload Delivery Mechanisms
Manual Injection: Users manually insert malicious payloads (e.g., XSS scripts) into intercepted requests.
Automated Attacks: The Intruder automates payload delivery by iterating through attack vectors (e.g., directory traversal strings).
CSRF/XSS Exploitation: The tool crafts requests with embedded scripts or forged tokens to exploit client-side or server-side flaws.
By leveraging these techniques, the software can simulate or execute attacks with precision, making it crucial for defenders to understand its operation to detect and mitigate malicious use.
![Work With Dorks [DORK’s Generator]-Dork Generator](https://blackhatus.com/wp-content/uploads/2025/07/Work-With-Dorks-DORKs-Generator-Dork-Generator-1.png)