Cracked Software
Here you can find all cracked software for hacking like emails, SMS, Whatsapp related as well as all cracking tools for you
Eziriz Net Reactor 5.9.2.0
Eziriz Net Reactor is a powerful obfuscation and protection tool designed to secure .NET applications from reverse engineering and unauthorized modifications. While it serves as a valuable resource for developers, its robust capabilities have also made it a favored choice among threat actors aiming to conceal malicious code, evade detection, and deploy payloads in cyberattacks. […]
HULK DDOS 2024
Distributed Denial-of-Service (DDoS) attacks remain a persistent threat in cybersecurity, and tools like HULK DDoS 2024 have emerged as potent weapons for disrupting online services. Unlike traditional DDoS methods, modern iterations employ advanced evasion techniques and increased scalability, making them more challenging to mitigate. These attacks overwhelm target servers with massive volumes of malicious traffic, often […]
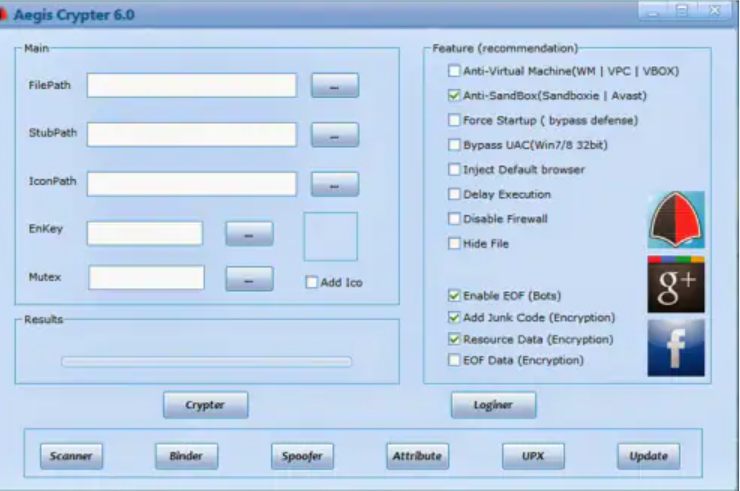
HACK PACK Crypters, Binders, Keyloggers
In the evolving landscape of cyber threats, attackers frequently employ tools such as crypters, binders, and keyloggers to facilitate malicious activities. These components often come bundled in “HACK PACK Crypters,” providing cybercriminals with the ability to obfuscate malware, combine malicious payloads with legitimate files, and stealthily capture sensitive user data. Threat actors leverage such tools […]
ATM Card Cloning All Tools 2025
Cybercriminals continually refine their methods to exploit financial systems, with ATM Card cloning remaining a significant threat. Attackers now utilize highly sophisticated tools to steal card data, bypass security measures, and withdraw funds illegally. These tools employ advanced techniques, including skimming, magnetic stripe manipulation, and malware deployment, which create significant risks for banks and individuals. To develop […]
MVII Port Scanner v1.0
Port scanning is a fundamental technique in network reconnaissance, often employed to identify open ports and services on target systems. One such tool, MVII Port Scanner v1.0, is capable of scanning a predefined range of ports (typically 1-65535) to detect vulnerabilities in networked devices. While port scanners are legitimate tools for network administrators, they are also […]
Cracking Tools Mega 2025
The Cracking Tools Mega 2025 poses a growing cybersecurity threat by consolidating multiple exploitation tools into a single, easily deployable package. Threat actors frequently use these toolkits to automate attacks, bypass security measures, and exploit vulnerabilities across networks and systems. Their modular design allows attackers to quickly adapt to emerging threats, making these tools a […]
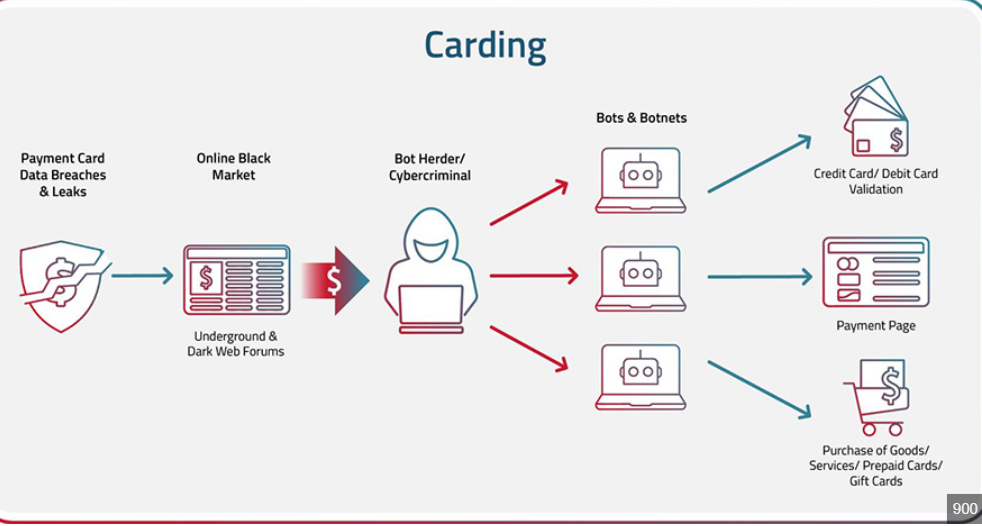
Carding and Hacking Tools 2024
Cyberattacks continue to evolve in sophistication, leveraging advanced tools to exploit vulnerabilities in systems and networks. Among these tools, carding and hacking software has become a significant threat, enabling malicious actors to conduct financial fraud, data breaches, and unauthorized access at scale. The “Carding and Hacking Tools 2024” category represents a collection of modernized utilities […]
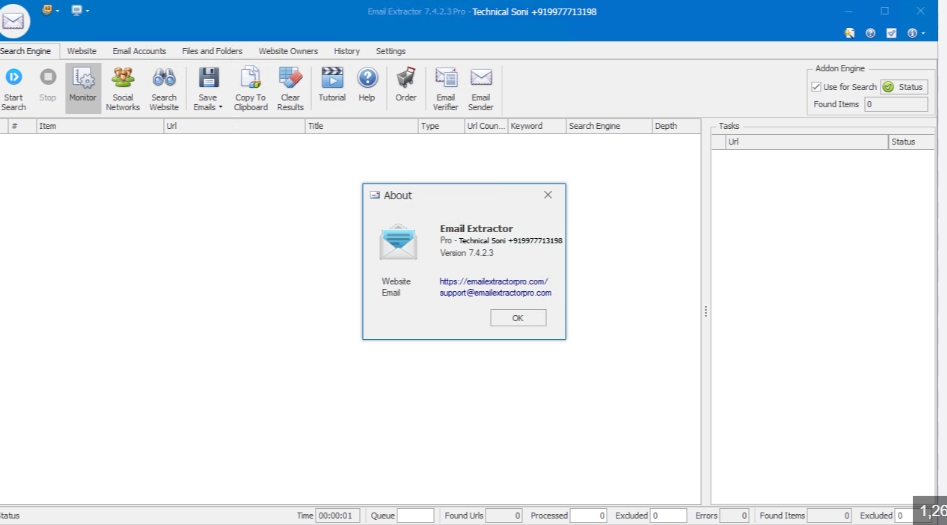
Free Email Extractor 5.7 cracked
The proliferation of cracked Email Extractor 5.7 tools has significantly contributed to the escalation of cyberattacks, particularly in the realm of data harvesting and phishing campaigns. One such tool, a widely distributed email extraction utility, is often exploited in its cracked form to bypass licensing restrictions, enabling threat actors to harvest email addresses end masse […]
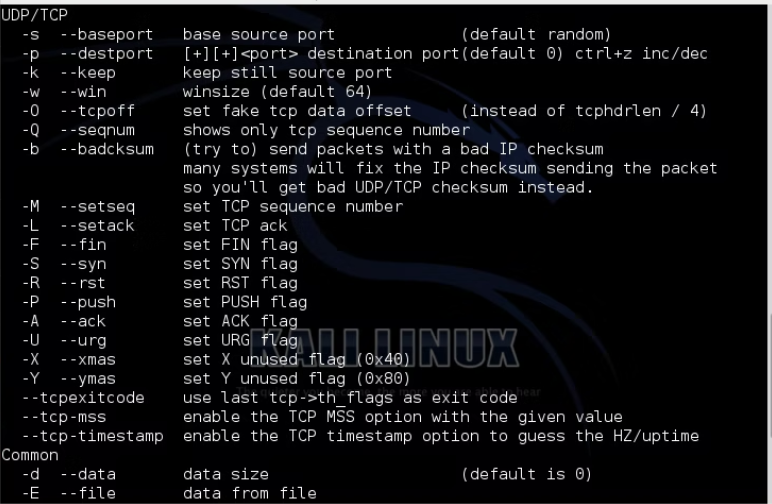
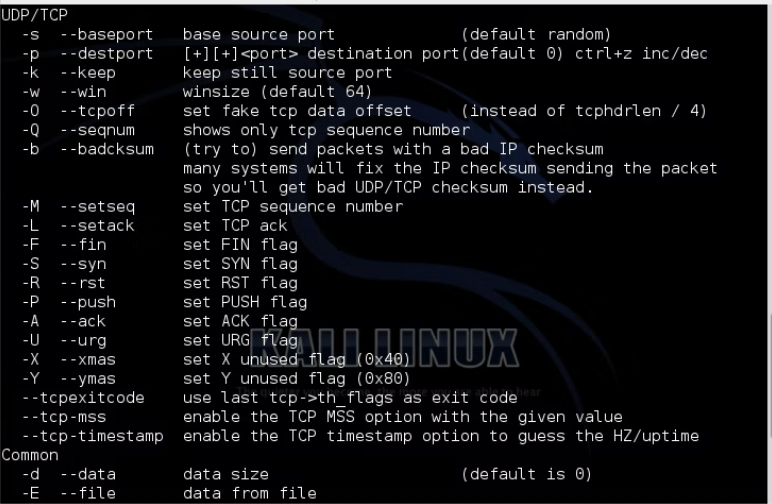
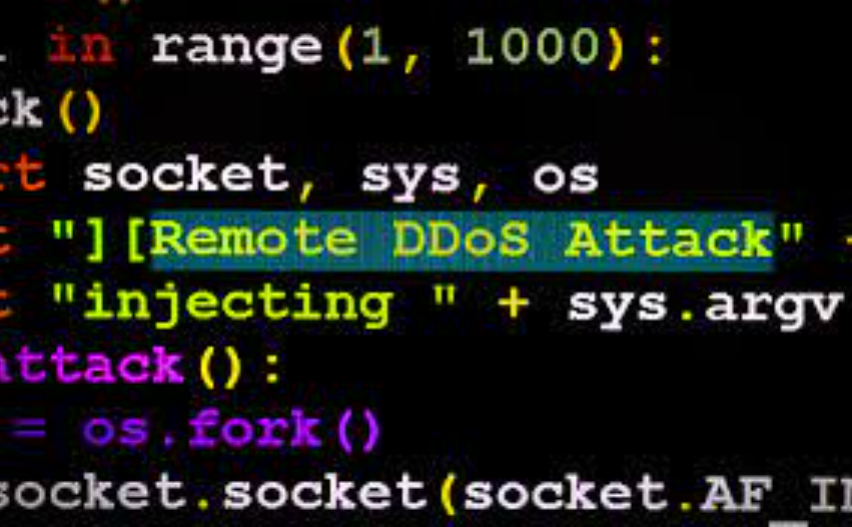
Layer 4 DDOS Tool Python 2024
Distributed Denial-of-Service (DDoS) attacks continue to pose a persistent threat in cybersecurity, with Layer 4 attacks being particularly disruptive due to their ability to overwhelm network resources. In 2024, a Python-based DDoS tool gained attention for its efficiency in launching high-volume attacks by exploiting transport-layer protocols. Such tools are frequently used in cyberattacks to disrupt […]
Advance Bulk Mailer 4.5 Cracked
Cybercriminals increasingly rely on cracked or pirated software to distribute malware, evade detection, and automate malicious campaigns. For instance, one such tool, often referred to as an “Advance Bulk Mailer 4.5 Cracked” version, has been repurposed by threat actors to conduct spam campaigns, phishing attacks, and malware distribution. Although the original software may have legitimate uses, cracked […]