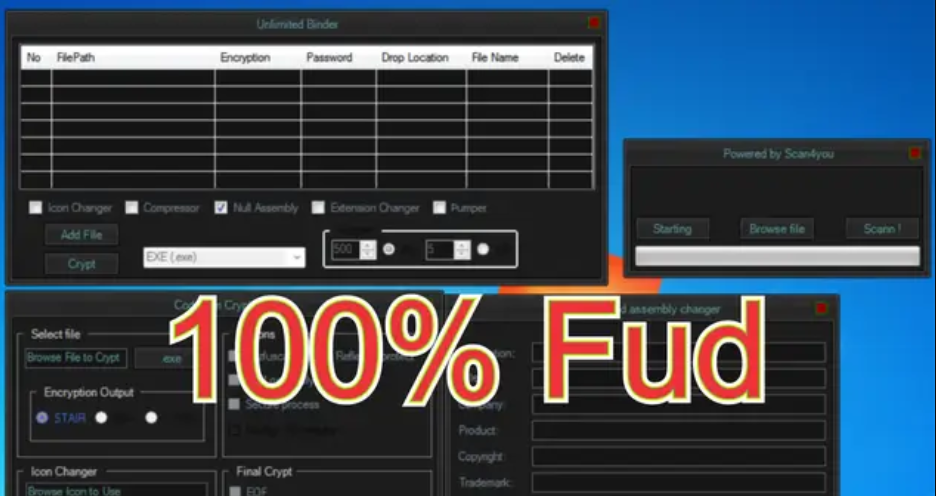
Crypter
Here are various crypter for you like PE (Portable Executable) Crypters, FUD, Code Packers, Metamorphic Crypters, Web Crypters, and .NET Crypters.
Cybersecurity Strategy with Davoser v1.1 for 2026
Short Intro: Davoser v1.1 stands as an innovative cybersecurity tool engineered to fortify online environments against sophisticated cyber risks. It serves the purpose of delivering layered protection through intelligent automation and expert insights. Its standout USP lies in seamless integration with existing infrastructures, reducing setup time and boosting efficiency without compromising security. Feature Explanations: Threat […]
Master Email Security Vulnerabilities Using Mail Brute 1.5 for 2026
Short Intro: Introducing Mail Brute 1.5, an innovative cybersecurity tool tailored for professionals conducting rigorous email brute force assessments. Its primary purpose is to evaluate and strengthen email account resilience against unauthorized access attempts. What sets it apart is the seamless integration with AI-driven prediction models, delivering unprecedented accuracy in vulnerability detection for 2026 security […]
Advanced Cybersecurity Defenses with Combo Essentials v1.2
Short Intro: The is a cutting-edge cybersecurity tool designed to fortify networks against emerging digital threats in 2026. It integrates automated vulnerability scanning with real-time monitoring to provide comprehensive protection for businesses and individuals. The key USP lies in its AI-driven predictive analytics, which anticipates attacks before they occur, ensuring unparalleled security efficiency. Feature Explanations: […]
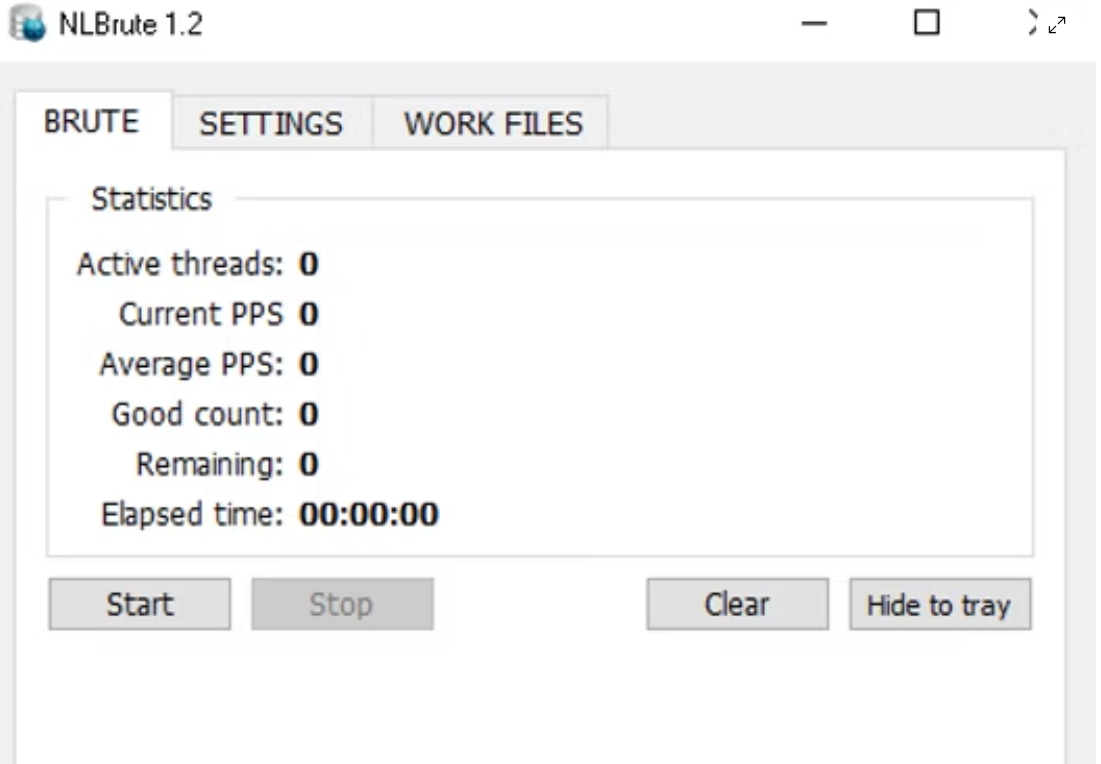
Arsenal with NL Brute 1.2 x64 + VPN Edition + Keygen 2026
Short Intro: NL Brute 1.2 x64 is a powerful cybersecurity tool designed for advanced penetration testing and security audits. It combines brute force capabilities with integrated VPN support to ensure anonymous and efficient operations. Key USP: Seamless key generation for rapid testing, making it indispensable for ethical hackers and security professionals in 2026. Feature Explanations: […]
Free Download The Ultimate ProRat v1.9
Short Intro: ProRat v1.9 is a cutting-edge cybersecurity tool designed for ethical hackers and security professionals to simulate and detect remote access threats. Its primary purpose is to enhance network security through comprehensive monitoring and control capabilities. The key USP lies in its stealthy deployment and real-time alerting, making it indispensable for proactive threat mitigation […]
Multi Account Cracker 2026 Cracked
Short Intro: Introducing Multi Account Cracker 2026 Cracked, a robust cybersecurity tool engineered for professionals to probe and expose weaknesses in multiple account setups. It serves the critical purpose of enhancing digital security by simulating unauthorized access attempts in controlled environments. What sets it apart is its unparalleled efficiency in cracking diverse account types, reducing […]
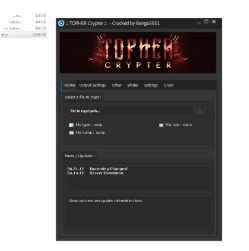
Topher Crypter Cracked 2024
Topher Crypter is a well-known executable obfuscation tool designed to bypass antivirus (AV) detection. The 2024 cracked version refers to an illegally modified release, often distributed through underground forums. While crypters have legitimate uses in penetration testing, cracked versions pose significant security, legal, and ethical risks. This article explores its functionality, dangers, and defensive measures. Download Link 1 Download Link 2 […]
OwnZ Crypter 3.5.9
OwnZ Crypter 3.5.9 is a cutting-edge file encryption and obfuscation tool designed to protect executable files from detection and analysis. It is widely used by developers, cybersecurity professionals, and ethical hackers to safeguard their software from reverse engineering and malicious attacks. With advanced features and a user-friendly interface, OwnZ Crypter ensures top-tier security for sensitive […]
Zeus Crypter 2024
In the ever-evolving landscape of cybersecurity, protecting sensitive files and executables from detection and analysis is crucial. Zeus Crypter 2024 emerges as a cutting-edge solution designed to encrypt, obfuscate, and secure files against reverse engineering and antivirus detection. Whether for ethical penetration testing or advanced malware research, Zeus Crypter 2024 offers robust features to ensure […]
Saddam Crypter 2024
In an era where digital security is paramount, Saddam Crypter 2024 emerges as a cutting-edge solution for encryption and data protection. Designed for both cybersecurity professionals and privacy-conscious users, this tool offers advanced features to safeguard sensitive information from unauthorized access. Whether for personal use or enterprise-level security, Saddam Crypter 2024 provides a robust defense against cyber […]