Exploiter
Here you can find all types of Exploiter like , Remote Exploiters, Local Exploiters, Automated Exploit Kits, Web Exploiters, Hardware Exploiters, Social Engineering Exploiters.
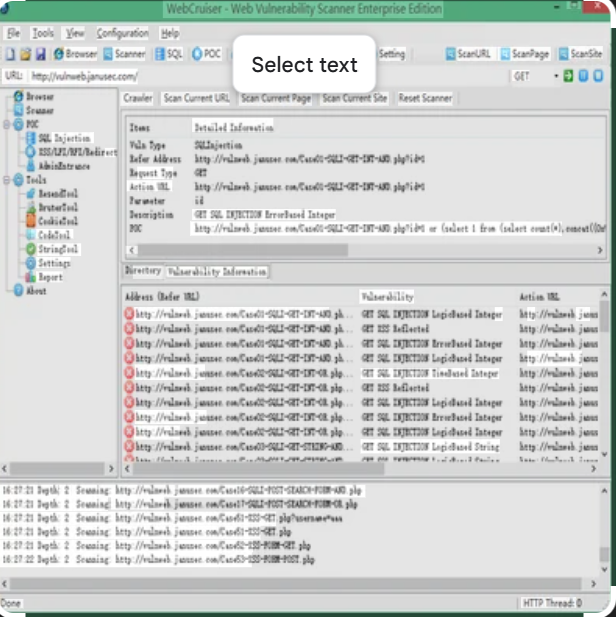
Elevate Your Web Security with WebCruiser Vulnerability Scanner 2026
Short Intro: Introducing WebCruiser Vulnerability Scanner 2026, a sophisticated cybersecurity solution engineered to scan and secure web-based systems against a myriad of vulnerabilities. Its core purpose is to deliver efficient, scalable protection for businesses facing evolving digital risks, from small startups to large enterprises. What sets it apart is its unparalleled speed and accuracy in […]
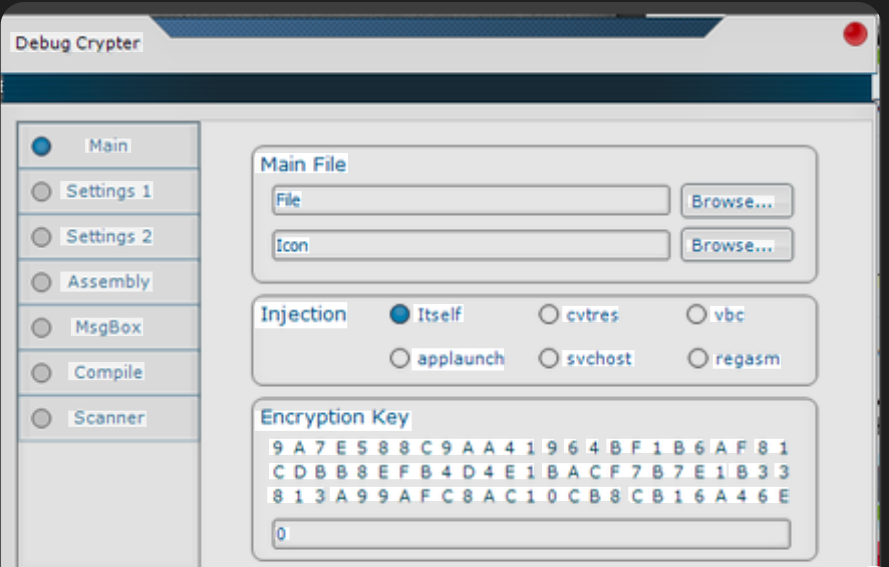
Crypter Polymorph 1.0 Elevate Your Cybersecurity Arsenal Free Download
Short Intro: Crypter Polymorph 1.0 stands out as a powerful cybersecurity tool engineered to encrypt and mutate code files, preventing unauthorized access and analysis in high-risk digital landscapes. It serves the essential purpose of fortifying applications against hackers, ensuring intellectual property remains protected. What sets it apart is its innovative polymorphic engine, which creates ever-evolving […]
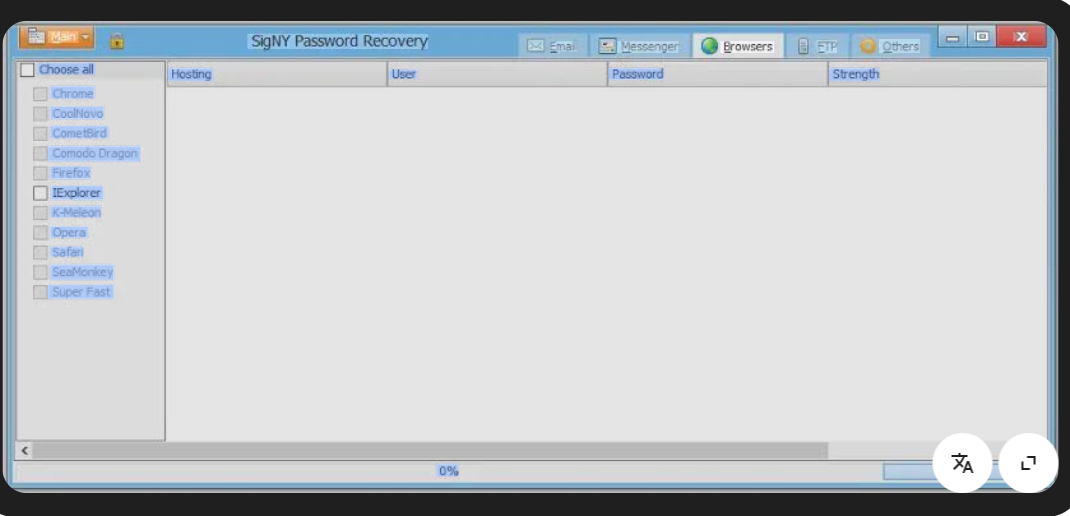
Signy Password Recovery 2026 – Your Go-To Cybersecurity Password Tool
Short Intro: Signy Password Recovery 2026 stands out as a robust cybersecurity tool engineered to retrieve inaccessible passwords with precision and reliability. It serves the critical purpose of restoring account access for users facing digital lockouts, while prioritizing data protection. What makes it unique is its proprietary recovery engine that combines speed with unbreakable encryption, […]
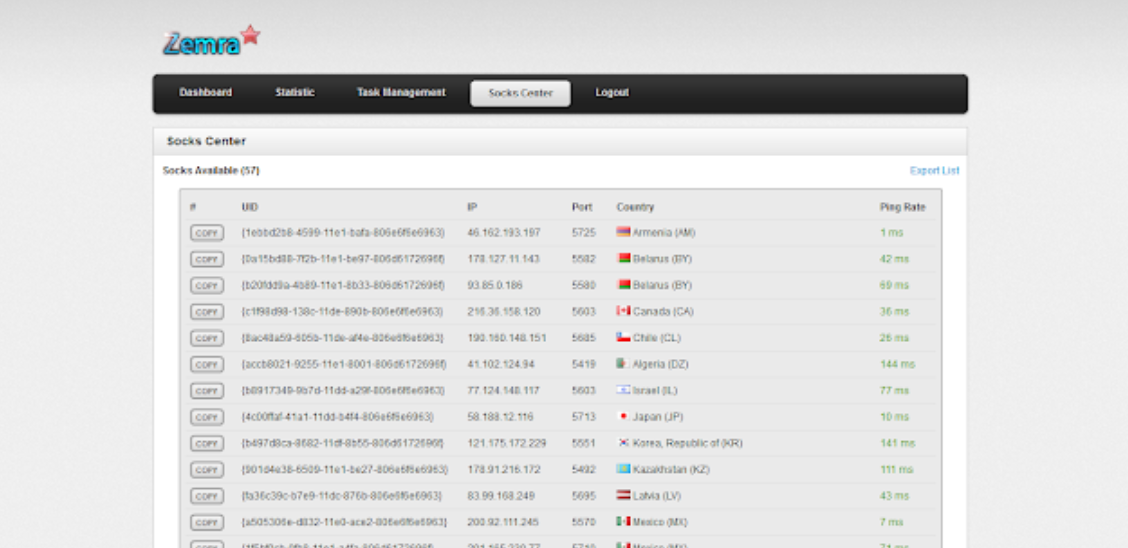
Enhance Your Network Security with Zemra Botnet 2026
Short Intro: Zemra Botnet 2026 serves as a robust cybersecurity tool engineered to expose and eliminate IoT-based botnet threats through advanced simulation techniques. It aims to empower IT professionals by modeling attack scenarios to preempt breaches and safeguard infrastructures. What sets it apart is its seamless integration with existing security stacks, delivering efficient, resource-light operations […]
Zeroday Link exploit 2024
Zero-Day Link Exploit 2024 is a recently discovered cybersecurity vulnerability that enables attackers to execute malicious code or gain unauthorized access through unpatched software flaws. This exploit poses a critical threat due to its ability to bypass conventional security defenses, putting organizations and individuals worldwide at risk. Download Link 1 Download Link 2 Download Link […]
Silent Doc Exploit 2024
Silent Doc Exploit 2024 is a sophisticated and stealthy exploitation framework designed to leverage document-based attack vectors for penetration testing and red teaming. Unlike traditional exploits, it operates covertly by embedding malicious payloads within seemingly harmless documents (e.g., PDFs, Word, Excel), making it a potent tool for advanced security assessments. Download Link 1 Download Link […]
Exploit Pack 2024
Exploit Pack 2024 is a state-of-the-art cybersecurity tool tailored for penetration testers, ethical hackers, and security researchers. It offers a comprehensive suite of exploits, payloads, and vulnerability assessment modules to help identify and address security risks in modern systems. With an intuitive interface and advanced automation, Exploit Pack streamlines security testing while adhering to ethical […]
Multi Exploit Builder V1
Multi Exploit Builder V1 is a powerful and flexible tool designed for cybersecurity professionals, ethical hackers, and penetration testers. It streamlines exploit creation and deployment, enabling efficient identification and mitigation of vulnerabilities. With an intuitive interface and advanced features, it is essential for modern cybersecurity tasks. Detailed Features of Multi Exploit Builder Feature Description Multi-Platform […]
Doc Exploit FUD 2024 with Tutorial
In the fast-changing cybersecurity landscape, attackers continually develop advanced tools to evade detection. Doc Exploit FUD 2024 is one such tool—a fully undetectable (FUD) payload generator targeting Microsoft Word documents. This overview explains its functionality, key features, use cases, and includes an educational guide. What Is Doc Exploit FUD 2024? Doc Exploit FUD 2024 is […]
Link Exploit 2024
In the constantly evolving digital landscape, effective link management is vital for cybersecurity professionals, ethical hackers, and IT specialists. Link Exploit 2024 stands out as an advanced tool designed to analyze, manipulate, and secure URLs with high accuracy. Ideal for penetration testing, vulnerability assessments, and red team operations, this tool offers a comprehensive framework for […]