Hacking Tutorial
This platform is very informative for you because here you can find all hacking tutorial which helps you to become expert
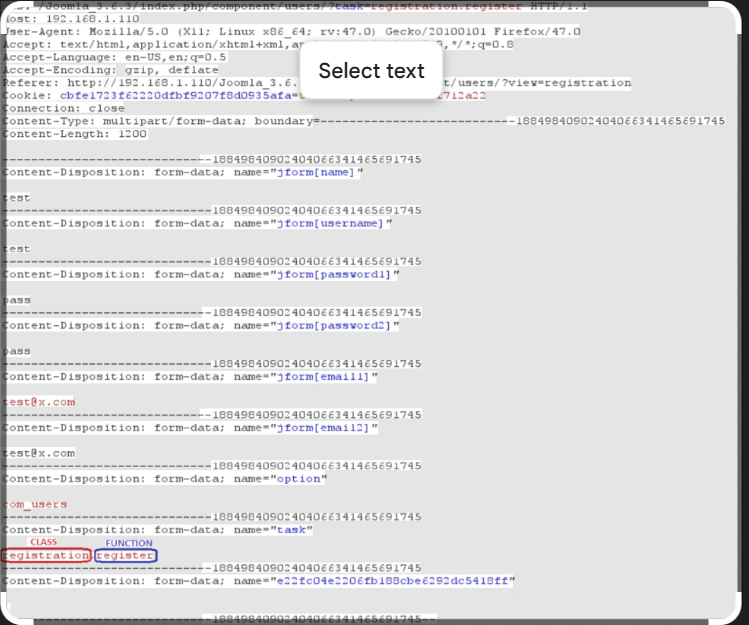
Joomla User Exploit Helper v1.1: Essential Tool for Cybersecurity Vulnerabilities in 2026
Short Intro: Introducing Joomla User Exploit Helper v1.1, a powerful cybersecurity utility focused on detecting and mitigating exploits within Joomla content management systems. This tool empowers professionals to conduct thorough audits of Joomla-based websites, protecting against data breaches. Its standout feature is the intuitive dashboard that simplifies exploit analysis, setting it apart for rapid, effective […]
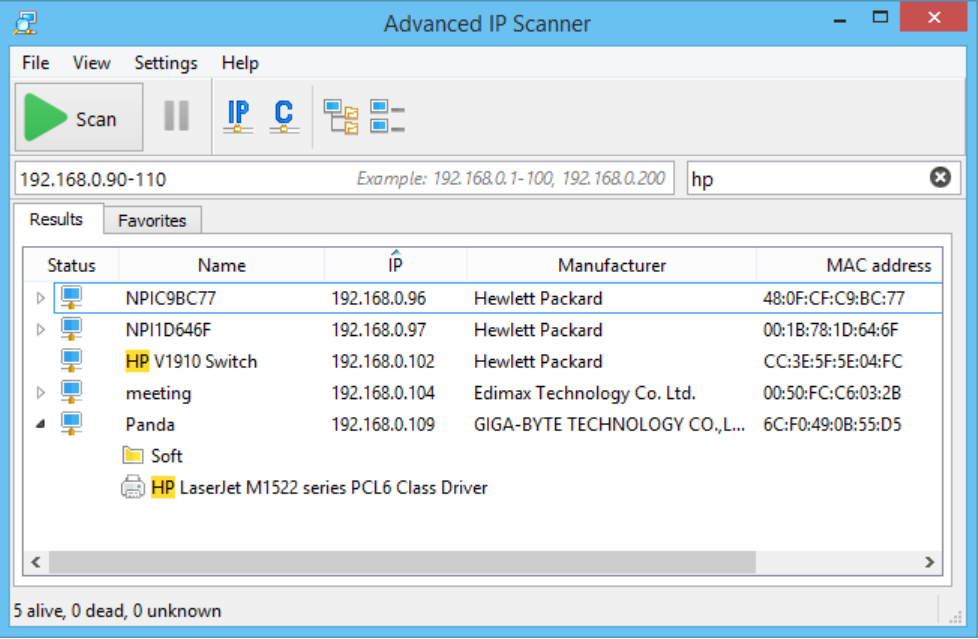
Xdedic IP Scanner 2026
Short Intro: The Xdedic IP Scanner 2026 is a cutting-edge cybersecurity tool designed to scan and analyze IP addresses for vulnerabilities, ensuring robust network security. Its primary purpose is to help professionals identify threats proactively, making it an essential asset for IT teams and cybersecurity experts. What sets it apart is its lightning-fast scanning speed […]
Lime Crypter 2026 – Revolutionizing Malware Encryption
Short Intro: Lime Crypter 2026 stands out as a premier cybersecurity solution focused on transforming raw data into fortified, undecryptable formats. It serves to block unauthorized decryption attempts and enhance overall system resilience against digital intrusions. What sets it apart is its AI-driven adaptive encryption, which learns from threats to provide dynamic, intelligent protection. Feature […]
Learning Tor and the Dark Web 2024
The Dark Web and the Tor network continue to play vital roles in cybersecurity, digital privacy, and ethical hacking. Often misunderstood, the Dark Web isn’t solely a hub for illegal activity—it also serves as a critical tool for whistleblowers, journalists, and privacy-focused users. Learning how Tor works and how to explore the Dark Web responsibly […]
Certified Ethical Hacker v10 PDFs Books
The Certified Ethical Hacker (CEH) v10 certification remains one of the most respected credentials in the field of cybersecurity. Although CEH v12 is now the latest version, CEH v10 books and PDFs continue to be highly useful for learning penetration testing, ethical hacking, and defensive strategies. This guide explores why CEH v10 study materials are […]
Hacking Android 2024
With over 3 billion active devices, Android remains the most widely used mobile operating system—and consequently, a top target for cyberattacks. Ethical Android hacking plays a vital role in defending against these threats by identifying vulnerabilities, securing applications, and testing system defenses. Whether you’re a penetration tester, security researcher, or cybersecurity student, mastering Android hacking […]
CEH V11 EC-COUNCIL CERTIFIED ETHICAL HACKER
The CEH v11 (Certified Ethical Hacker) certification by EC-Council is a globally recognized program designed to train cybersecurity professionals in identifying and mitigating vulnerabilities in modern systems. As cyberattacks become increasingly sophisticated, ethical hacking tools and methodologies—often covered in resources like the EC-Council Certified Ethical Hacker (CEH V11)— play a crucial role in both offensive […]
Hacking WEP/WPA/WPA2 WiFi Networks
Hacking WEP/WPA/WPA2 networks, particularly targeting WEP, WPA, and WPA2 security protocols, remains a significant threat in cybersecurity due to the widespread use of wireless networks. Weak encryption, poor password practices, and protocol vulnerabilities make these networks prime targets for attackers seeking unauthorized access, data interception, or network infiltration. While WEP is now largely obsolete due […]
WiFi Hacking for Beginners 2025
WiFi hacking remains a critical concern in modern cybersecurity, as wireless networks are often the weakest link in an organization’s defense. Attackers exploit vulnerabilities in WiFi Hacking for Beginners 2025, weak encryption, or poor configuration to gain unauthorized access, intercept data, or deploy malware. In 2025, beginner-friendly tools have made these attacks more accessible, allowing […]