Malware
Here are various types of malware you can download. Virus, Worm, Trojan, Ransomware, Spyware, Adware, Keylogger, Rootkit and Botnet Malware.
Hao Rat
Hao RAT is a powerful Remote Access Trojan (RAT) often studied by cybersecurity researchers, penetration testers, and ethical hackers. It shows how attackers gain remote control over compromised systems, steal sensitive data, and evade detection. By analyzing Hao RAT, professionals can better understand RAT operations, strengthen defenses, and improve malware detection strategies. Download Link 1 […]
Hicham RAT
Hicham RAT is a stealthy Remote Access Trojan (RAT) commonly studied by cybersecurity researchers, penetration testers, and ethical hackers. It demonstrates how attackers secretly control infected systems, capture sensitive data, and operate undetected. By analyzing Hicham RAT, professionals can understand RAT techniques, improve malware detection, and strengthen security defenses. Download Link 1 Download Link 2 […]
XpertRAT Malware
XpertRAT is a stealthy and powerful Remote Access Trojan (RAT) often analyzed by cybersecurity researchers, penetration testers, and ethical hackers. It demonstrates how attackers remotely control infected machines, steal sensitive information, and bypass security defenses. By studying XpertRAT, professionals can gain valuable insights into RAT operations and strengthen malware detection strategies. Download Link 1 Download […]
Mega RAT – Powerful RAT Tool
Mega RAT is a powerful Remote Access Trojan (RAT) designed for cybersecurity researchers, penetration testers, and ethical hackers. It demonstrates how attackers gain complete control over infected systems, steal sensitive data, and maintain stealth. By analyzing Mega RAT, professionals can better understand RAT operations and enhance malware detection and defense strategies. Download Link 1 Download […]
LuxNET RAT Malware
LuxNET RAT is a sophisticated Remote Access Trojan (RAT) used by cybersecurity researchers, penetration testers, and ethical hackers. It demonstrates how attackers remotely control infected systems, steal sensitive information, and operate stealthily. By analyzing LuxNET RAT, professionals can gain insights into modern RAT techniques and improve malware detection and defense strategies. Download Link 1 Download […]
Slayer RAT – Powerful RAT Tool
Slayer RAT is a powerful Remote Access Trojan (RAT) designed for cybersecurity researchers, penetration testers, and ethical hackers. It demonstrates how attackers gain full control over infected systems, steal sensitive data, and maintain stealth. By analyzing Slayer RAT, professionals can understand RAT operations and improve malware detection and defensive strategies. Download Link 1 Download Link […]
jSpy monitoring and remote access tool
jSpy is a powerful monitoring and remote access tool used by cybersecurity researchers, penetration testers, and ethical hackers. It demonstrates how attackers can secretly monitor system activity, capture sensitive information, and maintain stealth on infected machines. By analyzing jSpy, professionals can learn about spyware techniques and improve security defenses. Download Link 1 Download Link 2 […]
Cobian RAT Remote Access Trojan
Cobian RAT is a powerful Remote Access Trojan (RAT) designed for cybersecurity researchers, penetration testers, and ethical hackers. It demonstrates how attackers remotely control infected systems, steal sensitive data, and maintain stealth. By studying Cobian RAT, professionals can gain insights into RAT operations and improve malware detection and defense strategies. Download Link 1 Download Link […]
LimeRAT Remote Access Trojan
LimeRAT is a versatile Remote Access Trojan (RAT) widely studied by cybersecurity researchers, penetration testers, and ethical hackers. It demonstrates how attackers gain full control over infected systems, steal sensitive information, and maintain persistence. By analyzing LimeRAT, professionals can better understand RAT behaviors, improve malware detection, and enhance defensive strategies. Download Link 1 Download Link […]
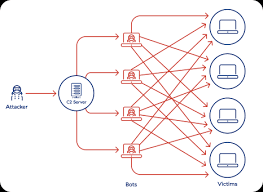
Solar Botnet for Researchers & Ethical Hackers
Solar Botnet is a powerful botnet malware often studied by cybersecurity researchers, penetration testers, and ethical hackers. It demonstrates how attackers build and manage large-scale botnet networks to perform tasks such as DDoS attacks, spam campaigns, and data exfiltration. By analyzing Solar Botnet, professionals can gain valuable insights into modern botnet operations and improve defensive […]