Codelux Crypter v3.0 Cracked
Codelux Crypter v3.0 Cracked have become a critical tool for cybercriminals, enabling them to bypass security measures and deploy malware undetected. Cracked versions of such tools, often leaked or illegally distributed, lower the technical barrier for attackers, allowing even those with minimal expertise to launch sophisticated attacks. These crypters are commonly used in ransomware campaigns, credential theft, and espionage, making them a persistent challenge for cybersecurity professionals. They evade traditional antivirus solutions by obfuscating malicious code, forcing defenders to rely on advanced behavioural analysis and threat intelligence.
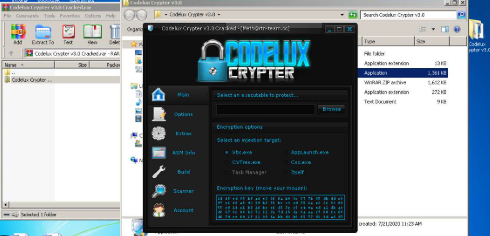
This software is a crypter—a specialised tool designed to encrypt, obfuscate, and manipulate malware to avoid detection by security software. It does not contain malicious code itself but is used to “wrap” harmful payloads (e.g., trojans, stealers, or ransomware) in a way that makes them appear benign. Attackers leverage this tool to distribute malware through phishing emails, malicious downloads, or exploit kits, ensuring their payloads remain hidden until they are executed.
Download Link 1
Download Link 2
Download Link 3
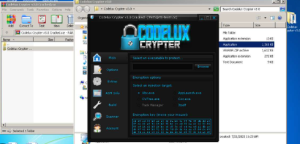
Key Features of Codelux Crypter v3.0 Cracked
| Feature | Description |
| Advanced Encryption | Uses AES, RSA, or custom algorithms to encrypt payloads. |
| Code Mutation | Randomises code structure to evade signature-based scanners. |
| Anti-VM/Sandbox | Detects virtualised environments and halts execution to avoid analysis. |
| Process Hollowing | Injects payload into legitimate processes (e.g., explorer.exe) for stealth. |
| FUD Capability | Renders malware as Fully Undetectable (FUD) by most antivirus (AV) engines at release. |
| Customizable Stub | Allows attackers to modify the loader for targeted evasion techniques. |
How the Software Works: Techniques and Payload Delivery
The crypter follows a structured workflow to ensure that the malware can effectively bypass modern security defenses.
First, the process begins with payload submission — the attacker inputs a malicious executable (e.g., a banking trojan) into the crypter interface.
Next, the tool initiates layered obfuscation, applying multiple techniques to mask the payload’s true nature:
Encryption – The payload is scrambled using strong algorithms, such as AES-256, to prevent static analysis.
Polymorphism – It then generates unique code variants with each build, which helps evade detection by signature-based antivirus engines.
Packing – The payload is compressed to further obscure its structure and behavior.
Afterward, the tool proceeds with stub creation. A lightweight “loader” is produced containing the decryption logic, which is then merged with the encrypted payload to form the final executable.
Before execution, the stub performs evasion checks to avoid detection or analysis. These checks may include:
Detecting the presence of debuggers, sandboxes, or other security tools.
Verifying specific system characteristics, such as the operating system version, locale settings, or hardware configurations. If any condition seems suspicious, execution may be aborted to avoid being analyzed in a controlled environment.
Once the stub is executed on the victim’s machine, the payload activation phase begins:
It may decrypt the payload directly in memory (a fileless technique), or alternatively, it writes the payload to disk in a concealed location.
Then, using techniques like process injection (e.g.,
CreateRemoteThread), it executes the malware inside a legitimate system process to blend in and avoid suspicion.
Finally, to ensure long-term access, the software implements persistence mechanisms, which may involve:
Modifying Windows registry run keys.
Creating scheduled tasks or placing executables in startup folders.
Using DLL sideloading or registering a new system service.
In summary, each phase is carefully engineered to evade detection, execute the payload stealthily, and maintain access over time.