CosaNostra v1.2 HTTP Botnet Cracked with Tutorial
The cybercrime underground continues to evolve with increasingly sophisticated botnet tools, and CosaNostra v1.2 HTTP BotNet with Tutorial has emerged as a particularly dangerous threat in modern network attacks. This advanced botnet framework demonstrates how cybercriminals are making powerful attack tools more accessible through comprehensive tutorials and user-friendly interfaces. CosaNostra v1.2 HTTP BotNet with Tutorial has been actively used in DDoS attacks, credential stuffing campaigns, and large-scale spam operations, showcasing its versatility in coordinated cyberattacks. Its HTTP-based architecture and modular design make it particularly effective at bypassing network security measures while maintaining persistent control over infected devices.
Download Link 1
Download Link 2
Download Link 3
Download Link 4
CosaNostra v1.2 HTTP Botnet Cracked with Tutorial latest version
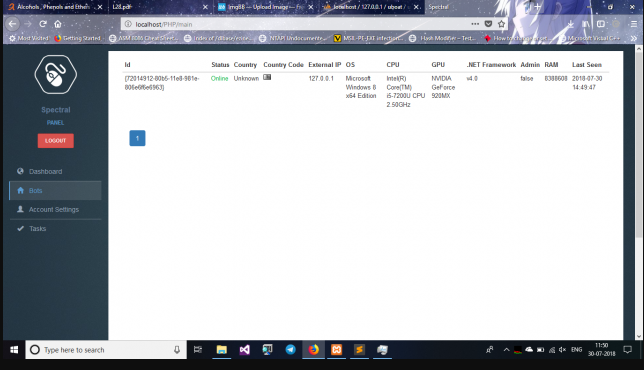
What is the CosaNostra v1.2 HTTP Botnet
This software is a sophisticated botnet framework that allows attackers to create and manage networks of compromised devices through HTTP-based communication. Designed for both novice and experienced cybercriminals, it includes detailed tutorials that lower the technical barrier for conducting large-scale attacks. The botnet typically spreads through exploit kits, phishing campaigns, or malicious downloads, infecting devices ranging from home routers to enterprise servers. Once installed, it enables attackers to remotely control infected machines, launch coordinated attacks, and steal sensitive data. Cybercriminals primarily use it for DDoS attacks, credential harvesting, and as a payload delivery system for other malware.
Key Features
| Feature | Description |
| HTTP-Based C2 | Uses standard web protocols to evade detection |
| Modular Architecture | Supports dynamic loading of attack modules |
| DDoS Capabilities | Conducts multiple attack vectors (HTTP flood, SYN flood, etc.) |
| Credential Stuffing | Automates login attempts using stolen credentials |
| Persistence | Maintains access through registry modifications and service creation |
| Geo-Targeting | Focuses attacks on specific regions or networks |
| Encrypted Payloads | Uses AES encryption for C2 communication and module delivery |
| Bot Management | Provides real-time monitoring and control of infected devices |
How the CosaNostra v1.2 HTTP Botnet Works
The botnet operates through a structured infection and attack process:
1. Delivery and Infection
Initial compromise typically occurs through:
- Exploit kits.
- Phishing emails.
- Drive-by downloads.
The infection process:
- Drops a lightweight loader that fetches the full payload.
- Exploits system vulnerabilities to gain persistence.
- Connects to the C2 server using HTTP/S requests.
2. Bot Registration
Once installed, the malware:
- Sends system information to the C2 server.
- Receives a unique bot ID and configuration.
- Downloads additional modules based on attacker commands.
3. Attack Execution
The botnet can conduct multiple attack types:
DDoS Attacks:
- HTTP/S flood attacks against web servers.
- SYN/ACK floods for network layer attacks.
- Slowloris-style application layer attacks.
Credential Stuffing:
- Test stolen credentials across multiple sites.
- Uses rotating proxy lists to avoid detection.
- Reports successful logins to attackers.
Data Exfiltration:
- Scans for sensitive documents and databases.
- Compresses and encrypts stolen data.
- Uploads to attacker-controlled servers.
4. C2 Communication
The botnet uses advanced techniques for stealth:
- Domain generation algorithms.
- HTTPS traffic blending.
- Dead drop resolvers.
- Time-based activation.
5. Persistence and Evasion
To maintain operations:
- Process hollowing.
- Rootkit functionality.
- Regular updates.
- Self-destruct.


