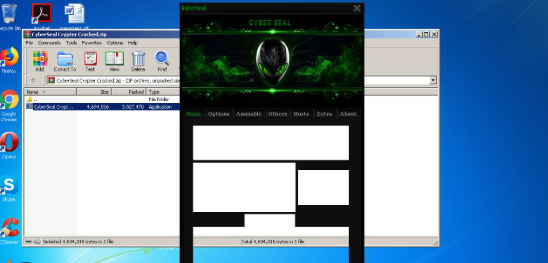
CyberSeal Crypter 2025 Cracked
In today’s threat landscape, CyberSeal Crypter 2025 Crackedplay a significant role in enabling cybercriminals to bypass security defences. These tools are frequently used to obfuscate malicious payloads, making them undetectable by traditional antivirus solutions. By encrypting, compressing, or modifying signatures, crypters allow attackers to deliver ransomware, spyware, and trojans without raising suspicion. Cracked or illegally distributed versions of such tools further lower the barrier to entry, allowing even less-skilled threat actors to launch sophisticated attacks.
Download Link 1
Download Link 2
Download Link 3
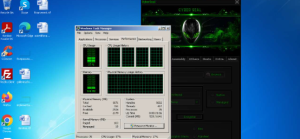
Understanding the CyberSeal Crypter 2025 CrackedPurpose and Functionality
This software is a type of crypter—a tool designed to encrypt and manipulate malicious executables to evade detection. Typically used by attackers, it takes an existing file and applies various obfuscation techniques to make it appear harmless to security software. While crypters themselves are not, they are often employed in cyberattacks to distribute harmful payloads, such as remote access trojans (RATS), keyloggers, and ransomware.
Key Features of the Software
| Feature | Description |
| Payload Encryption | Encrypts to avoid signature-based detection. |
| Polymorphic Code | Changes the code structure dynamically to evade heuristic analysis. |
| Anti-Sandboxing | Detects virtual environments to prevent analysis. |
| Process Injection | Injects payloads into legitimate processes to avoid detection. |
| FUD (Fully Undetectable) | It makes it invisible to most antivirus programs. |
| Customizable Obfuscation | Allows attackers to tweak encryption methods for better evasion. |
How the Software Works: Techniques and Payload Delivery
The crypter operates through a multi-stage process designed to keep the payload concealed until the moment of execution.
1. Payload Input – First, the attacker loads a malicious file—typically a remote access trojan (RAT) or an information stealer—into the crypter.
2. Encryption and Obfuscation – Next, the software encrypts the payload using multiple layers, often including AES and XOR encryption. Additionally, it obfuscates the binary structure, which helps to bypass signature-based antivirus detection.
3. Stub Generation – After encryption, the crypter generates a small “stub.” This stub contains the decryption routine and is then bundled with the encrypted payload.
4. Anti-Analysis Checks – Before proceeding with execution, the stub performs a series of checks. It looks for debugging tools, sandbox environments, and virtual machines. These checks are critical, as they help prevent reverse engineering and analysis by security researchers.
5. Execution and Payload Deployment – Once the stub confirms the environment is safe, it activates. At this stage, the stub either decrypts the payload directly in memory—supporting fileless execution—or drops it into a hidden system directory, making detection more difficult.
6. Persistence Mechanisms – Finally, the payload may establish persistence to survive system reboots. This is often done through registry modifications, scheduled tasks, or DLL hijacking, ensuring the malware remains active over time.
By chaining these steps together and layering multiple techniques, the crypter effectively conceals malicious activity while increasing the difficulty of detection and removal.