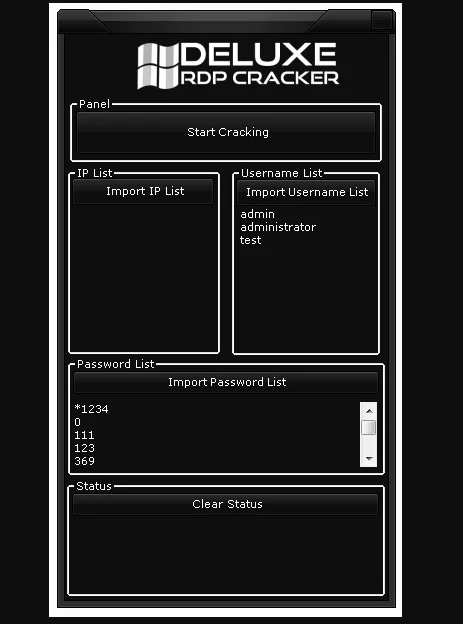
Deluxe RDP Cracker 2024
As organizations increasingly rely on Remote Desktop Protocol (RDP) for remote access and administration, the risk of unauthorized access via weak credentials also rises. Deluxe RDP Cracker 2024 is a professional-grade tool designed to assess RDP security by simulating brute-force attacks—intended solely for ethical hacking, security research, and authorized penetration testing.
Download Link 1
Download Link 2
Download Link 3
Download Link 4
What is Deluxe RDP Cracker 2024?
Deluxe RDP Cracker 2024 is a cybersecurity tool used by ethical hackers and penetration testers to evaluate the security of RDP endpoints. It simulates password-based attacks on RDP services to uncover weak credentials and misconfigurations before they can be exploited by malicious actors. The tool supports multi-threaded operations, proxy/VPN integration, and advanced scripting for in-depth audits.
Key Features
| Feature | Description |
|---|---|
| Brute-Force Attack Engine | Rapidly tests thousands of username/password combinations to identify weak logins. |
| Dictionary Attack Support | Accepts custom wordlists for more targeted password auditing. |
| Proxy & VPN Integration | Enables IP masking for secure and anonymous testing sessions. |
| Multi-Threaded Cracking | Increases attack speed using concurrent connections. |
| Automated RDP Port Scanning | Scans defined IP ranges to identify systems with open RDP ports (default 3389). |
| Session Hijacking Detection | Flags vulnerable live sessions that could be hijacked. |
| Exploit Modules | Includes checks for known RDP vulnerabilities like BlueKeep (CVE-2019-0708). |
| Custom Scripting Interface | Extend functionality by writing personalized test scripts. |
| Logging & Reporting Tools | Generates detailed activity logs and PDF/CSV reports for audits. |
| Cross-Platform Compatibility | Works on Windows and Linux environments. |
Why Use Deluxe RDP Cracker 2024?
✅ Proactively Identify Weak Credentials – Audit RDP logins to avoid brute-force attacks.
✅ Enhance RDP Security Posture – Evaluate exposure to known RDP exploits like BlueKeep.
✅ Train Security Teams – Use in red team/blue team exercises and ethical hacking labs.
✅ Support Compliance – Helps with audits by detecting misconfigurations and weak access points.
✅ Speed + Accuracy – Multi-threaded operations and automation reduce testing time.


